Pretty Good Privacy (PGP) For Data Encryption and Decryption.
PGP is a program used for encrypting and decrypting digital files and send messages securely over the Internet.
Pretty good privacy is developed by Phil Zimmerman in 1991 gained its popularity in encryption-decryption of email over the internet and also to authenticate messages with digital signatures, and is now widely used by many corporations to ensure privacy.
What is PGP ?
Pretty Good Privacy (PGP) is a data encryption and decryption computer program that provides cryptographic privacy and authentication for data communication. PGP is often used for signing, encrypting, and decrypting text, e-mails, files, directories, and whole disk partitions and to increase the security of e-mail communications.
PGP encryption uses a serial combination of hashing, data compression, symmetric-key cryptography, and finally public-key cryptography, each step uses one of several supported algorithms. Each public key is bound to a username or an e-mail address.
The first version of this system was generally known as a web of trust to contrast with the X.509 system, which uses a hierarchical approach based on certificate authority and which was added to PGP implementations later. Current versions of PGP encryption include both options through an automated key management server.
How it works?
Pretty Good Privacy (PGP) can be used to send messages confidentially. For this PGP combines symmetric-key encryption and public-key encryption. The message is encrypted using a symmetric encryption algorithm, which requires a symmetric key. Each symmetric key is used only once and is also called a session key.
The message and its session key are sent to the receiver. The session key must be sent to the receiver so they know how to decrypt the message, but to protect it during transmission it is encrypted with the receiver’s public key. Only the private key belonging to the receiver can decrypt the session key.
Pretty good privacy uses a variation of asymmetric cryptography hence, requires two separate keys public key (known to all) and private key (known to the user only) per user. These keys may be different but the key pair is mathematically linked. You encrypt a message and send to someone else using their public key. When they receive it, they decrypt it using their private key.
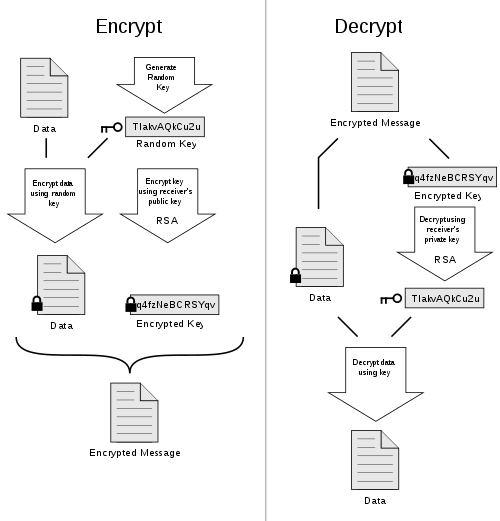
When a user encrypts plaintext with PGP, PGP first compresses the plaintext, then creates a session key, which is a one-time-only secret key. This key is a random number generated from the random movements of your mouse and the keystrokes you type. This session key can work with two public key versions, i.e. RSA and Diffie-Hellman algorithms to encrypt plain text; the result is cipher text.
Once the data is encrypted, the session key is then encrypted to the recipient’s public key. This public key-encrypted session key is transmitted along with the cipher text to the recipient.
Decryption works in the reverse. The recipient’s copy of PGP uses his or her private key to recover the temporary session key, which PGP then uses to decrypt the conventionally-encrypted ciphertext.
Also See: How To Encrypt And Decrypt Data Using PGP – Working
Where we can use pretty good privacy (PGP)?
Pretty good privacy can be used to authenticate digitally signing messages and encrypt/decrypt texts, emails, files, directories and hard disk drives.
For mobile email encryption Symantec gives add-ons mobile encryption application.
Download PGP Data Encryption and Decryption software
For android and iOS
For windows users :
Gpg4win for file and email encryption.
For Linux users:
Seahorse is a graphical interface for managing and using encryption keys. Currently it supports PGP keys (using GPG/GPGME) and SSH keys.











