What is PGP?
First Read Pretty Good Privacy (PGP) – A Program That Provides Data Encryption And Decryption
Have you ever thought the importance to maintain privacy without intervention of outer world?
To solve this problem we can use an encryption technique, Pretty Good Privacy Encryption is one of those technique.
So, How To Encrypt And Decrypt Data Using PGP?
Please check the Video Tutorial at the end of the Article.
This technique is used for data encryption and decryption computer program that provides cryptographic privacy and authentication for data communication.
PGP is a popular solution for encrypting, decrypting, signing, and verifying messages and files, often found in email communications and package repository identity verification (because security matters).
PGP usability depends on the public/private keys pair encryption representation. A public key is the key which is known to everyone and can be used to encrypt a message. A private key just the opposite of public key in which it is known to the individual only.
PGP encryption uses a serial combination of hashing, data compression, symmetric-key cryptography, and finally public-key cryptography, each step uses one of several supported algorithms. Each public key is bound to a username or an e-mail address.
The first version of this system was generally known as a web of trust to contrast with the X.509 system, which uses a hierarchical approach based on certificate authority and which was added to PGP implementations later. Current versions of PGP encryption include both options through an automated key management server.
What is RSA?
RSA (Rivest, Shamir, and Adleman) is one of the best public key cryptographic algorithms in use today that ensures secure communication over networks. It is an asymmetric cryptography algorithm which means it uses two different keys i.e. Public key and Private key.
Let’s Start Working!
Requirements
- gpg4win
- Notepad ++ (You can use simple Notepad too)
For windows we will use gpg4win.
- Download and install gpg4win/Kleopatra from gpg4win.org
- Open Kleopatra
- Click on file -> New key pair
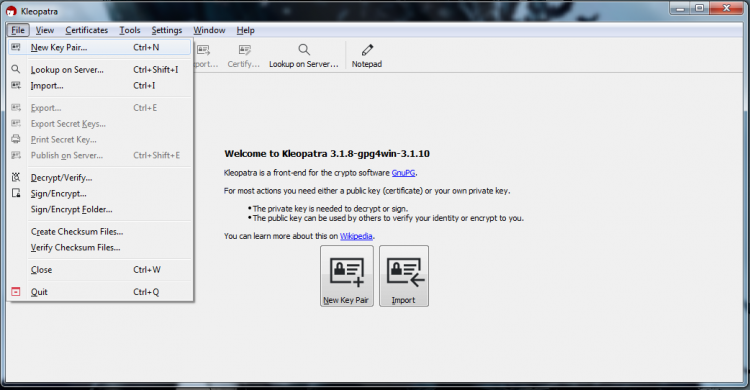
- Click on Create a personal open key pair.
- Provide your name and email details.
- Go to Advanced settings – Select RSA settings then press ok and next.
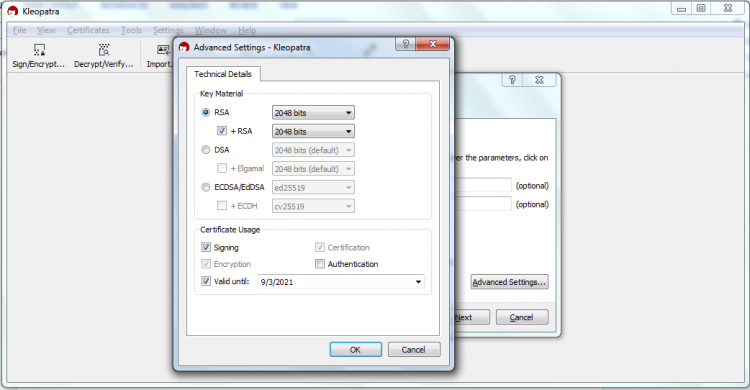
- Confirm your settings and enter your passphrase then finish
- Once created right click on the key and Export public key
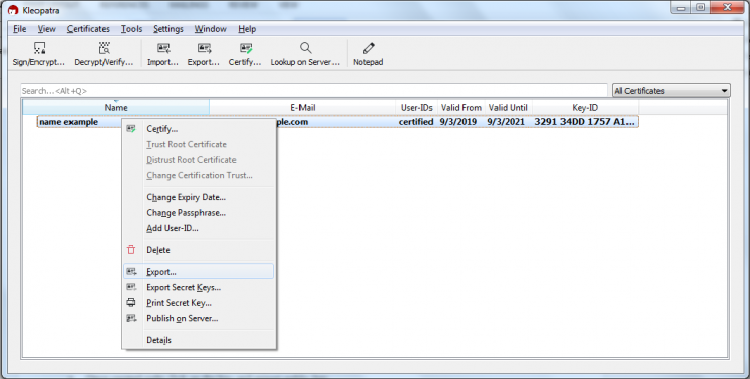
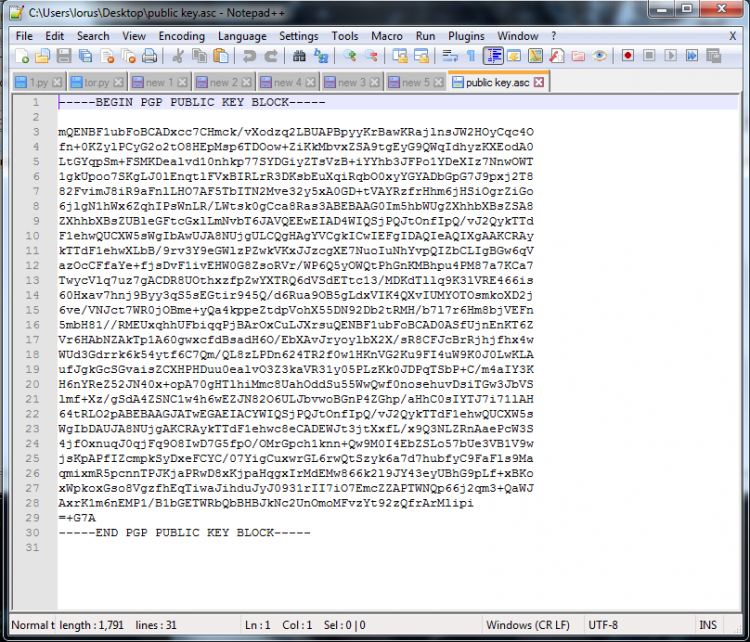
- To open the Public key with notepad ++
- Then right click and Export Secret/Private Key
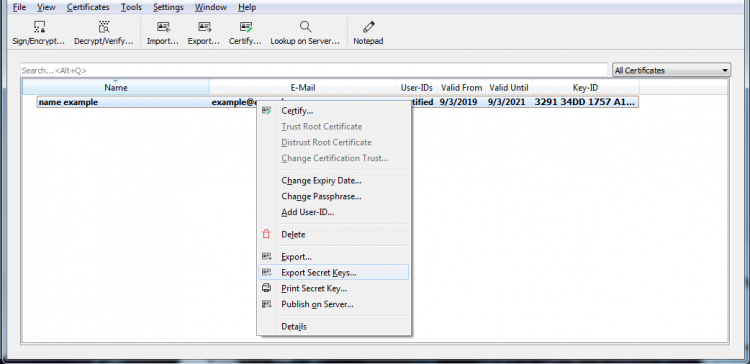
- You can open them both with notepad ++
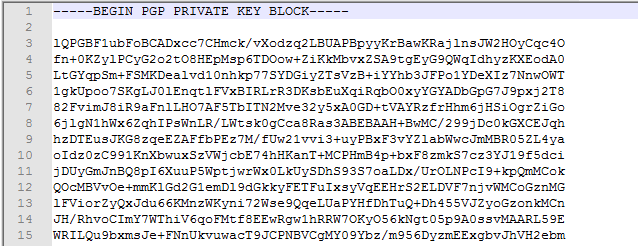
- You can send or post your public key so that it is accessible to people who want to send you information.
SENDERS PERSPECTIVE
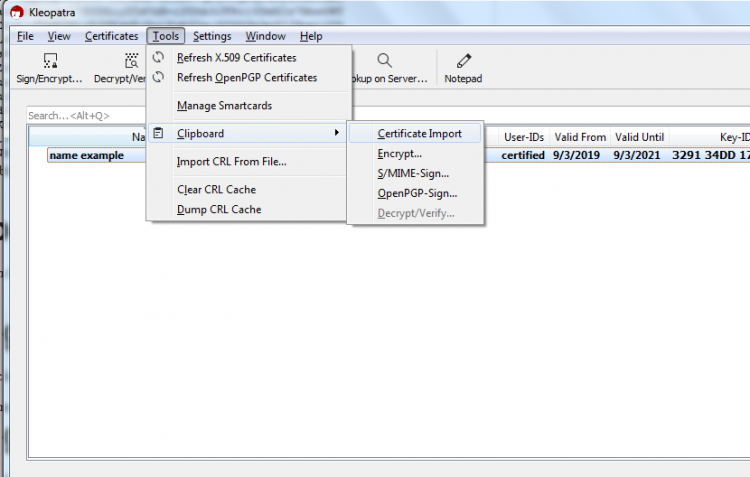
- Copy the public key
- In your task bar, right click on the Kleopatra icon, go to ‘Clipboard’, then click ‘Certificate Import’.
ENCRYPTING A MESSAGE
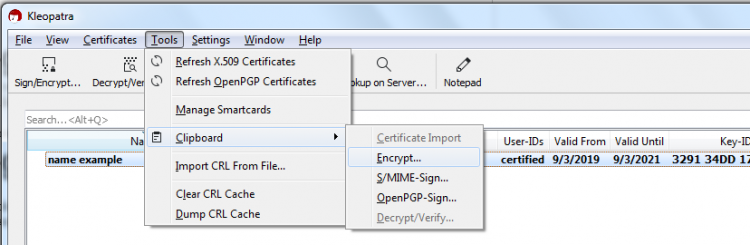
- Copy the message or text you want to encrypt
- Go to kleopatra > Tools > Clipboard and click on Encrypt
- Select Add Recipent
- Select your Certificate > Ok
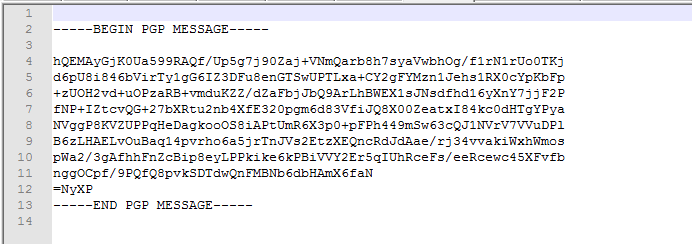
- Done, you can now send the message paste it into notepad
DECRYPTING A MESSAGE
- First copy the PGP (encrypted) message.
- Open Kleopatra > Tools> Clipboard> and Decrypt/Verify
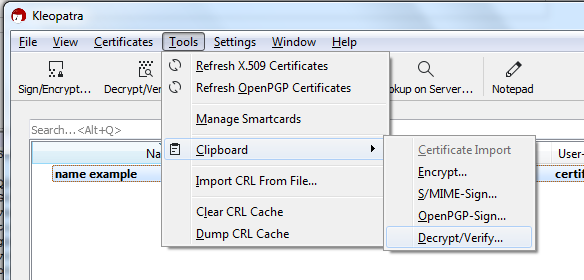
- Enter passphrase and the message will be copied to your clipboard automatically just paste into notepad ++
![]()
PGP also has attack vectors based on CIA triad threats (confidentiality, Integrity and availability). PGP is ideal for the sheer fact that so many people use email and it is one of the best solutions available, despite not being perfect. For instant messaging, it may even be better to use XMPP with OTR(Off the Record) encryption.
PGP can be used for encrypting, decrypting and signing messages and files. We can use command flags and carefully craft our messages to mitigate unnecessary information sharing. Less information is better; we should do what we can to limit the accessibility of our keys and identity on a need-to-know basis.
Watch Video Tutorial











