Cybersecurity: The Core of Computer Science Expertise
In recent years, the digital world has witnessed several high-profile cyber-attacks ranging from ransomware to sophisticated data breaches…
March 23, 2024
3 Seemingly Minor Ways a Business Can Breach Data Protection Rules
Entering into the business landscape in 2024 can be a little daunting. It’s not just about coming up…
March 16, 2024
6 Benefits of Vulnerability Management
Vulnerability management is an ongoing process that helps identify, evaluate, remediate, and mitigate computer and software system vulnerabilities.…
March 12, 2024
Anonymous-Proxies: A Cutting-Edge Proxy Solution
Anonymous-Proxies boasts a wide range of proxy and VPN services, promising security, affordability, and unique features. But does…
February 7, 2024
SAP Data Leak Underscores the Importance of DLP
In a world where technological vulnerabilities are rapidly surfacing, a SAP data leak represents a significant and often…
August 1, 2023
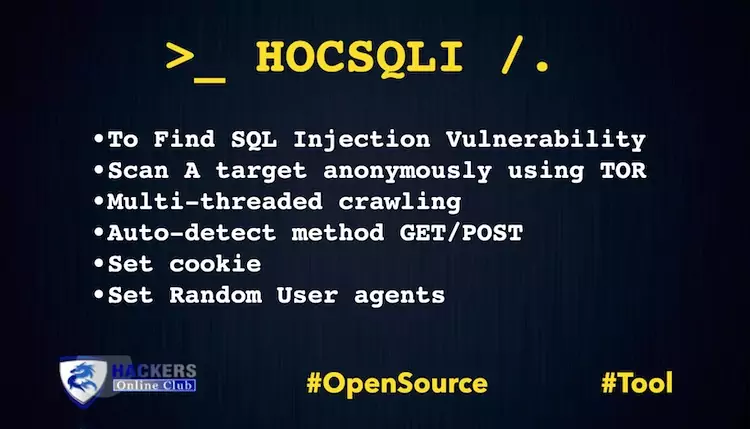
HOCSQLI Automatic SQL Injection Vulnerability Scanner
Today, we are presenting our own Cyber Intelligence suite HOCSQLI. An Automatic (SQL Injection) vulnerability scanner along with…
NetworkMiner – For Network Forensic Analysis
NetworkMiner, it is an open source Network Forensic Analysis Software (NFAT) for Windows (yet additionally works in Linux/Mac OS…
November 6, 2020
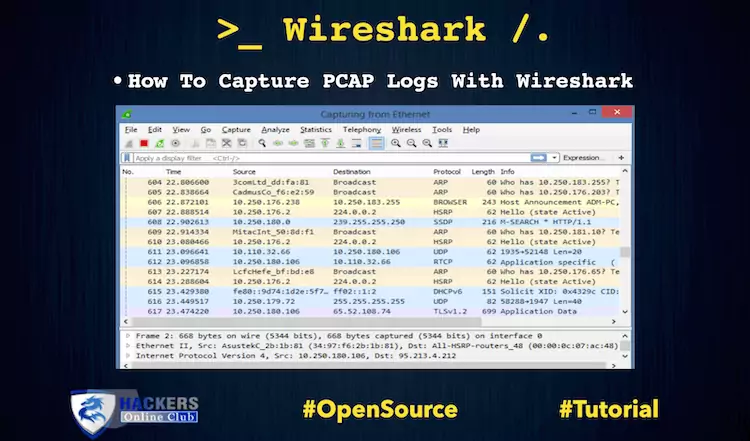
How To Capture PCAP Logs With Wireshark
Today, we are working to capture the PCAP LOGS with the help of Wireshark. Organization following logs are…
October 22, 2020
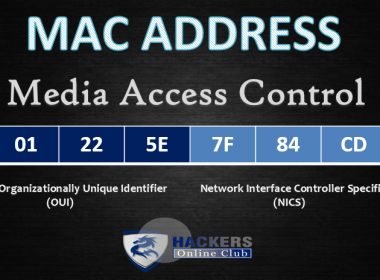
How To Spoof Mac Address
In this article we are going to discuss about manually and automatically method of mac spoofing over Linux…
HOCXSS Automatic Cross Site Scripting XSS Vulnerability Scanner
Today, we are presenting our own Intelligence HOCXSS Automatic (Cross Site Scripting) vulnerability scanner along with the complete…