
CryptoJacking: A Technique Using By Hackers To Mine Cryptocurrencies
[Update 17 August 2022]
The act of cryptojacking involves hijacking a computer systems for the purpose of mining cryptocurrencies, through websites, or without the user’s consent.
How does it Work?
- CryptoJackers are using JavaScript on a web-page to mine crypto coins.
- In browser mining, there is no need to install any software. They are just required to visit that particular website.
- There is no way to detect malicious link immediately, because it does not affect website performance.
- It runs silently.
CryptoJacking is on Rise
Last November, Adguard reported a 31 percent growth rate for in-browser cryptojacking. Its research shows 33,000 websites are running crypto mining scripts. Adguard estimated that those site had a billion combined monthly visitors. This February, The Bad Packet Report found 34,474 sites running Coinhive, the most popular JavaScript miner that is also used for legitimate crypto mining activity.
“Crypto mining is in its infancy. There’s a lot of room for growth and evolution,” says Marc Laliberte, threat analyst at network security solutions provider WatchGuard Technologies. He notes that Coinhive is easy to deploy and generated $300 thousand in its first month. “It’s grown quite a bit since then. It’s really easy money.”
Pro-Ocean new cryptojacking Malware was found by Palo Alto Networks security researchers.
Pro-Ocean uses known vulnerabilities to target cloud applications . In analysis, researchers found Pro-Ocean targeting Apache ActiveMQ (CVE-2016-3088), Oracle WebLogic (CVE-2017-10271) and Redis (unsecure instances).
In the case that the malware runs in Tencent Cloud or Alibaba Cloud, it will use the exact code of the previous malware to uninstall monitoring agents to avoid detection. Additionally, it attempts to remove other malware and miners including Luoxk, BillGates, XMRig and Hashfish before installation.
Once installed, the malware kills any process that uses the CPU heavily, so that it’s able to use 100% of the CPU and mine Monero efficiently.
The Process
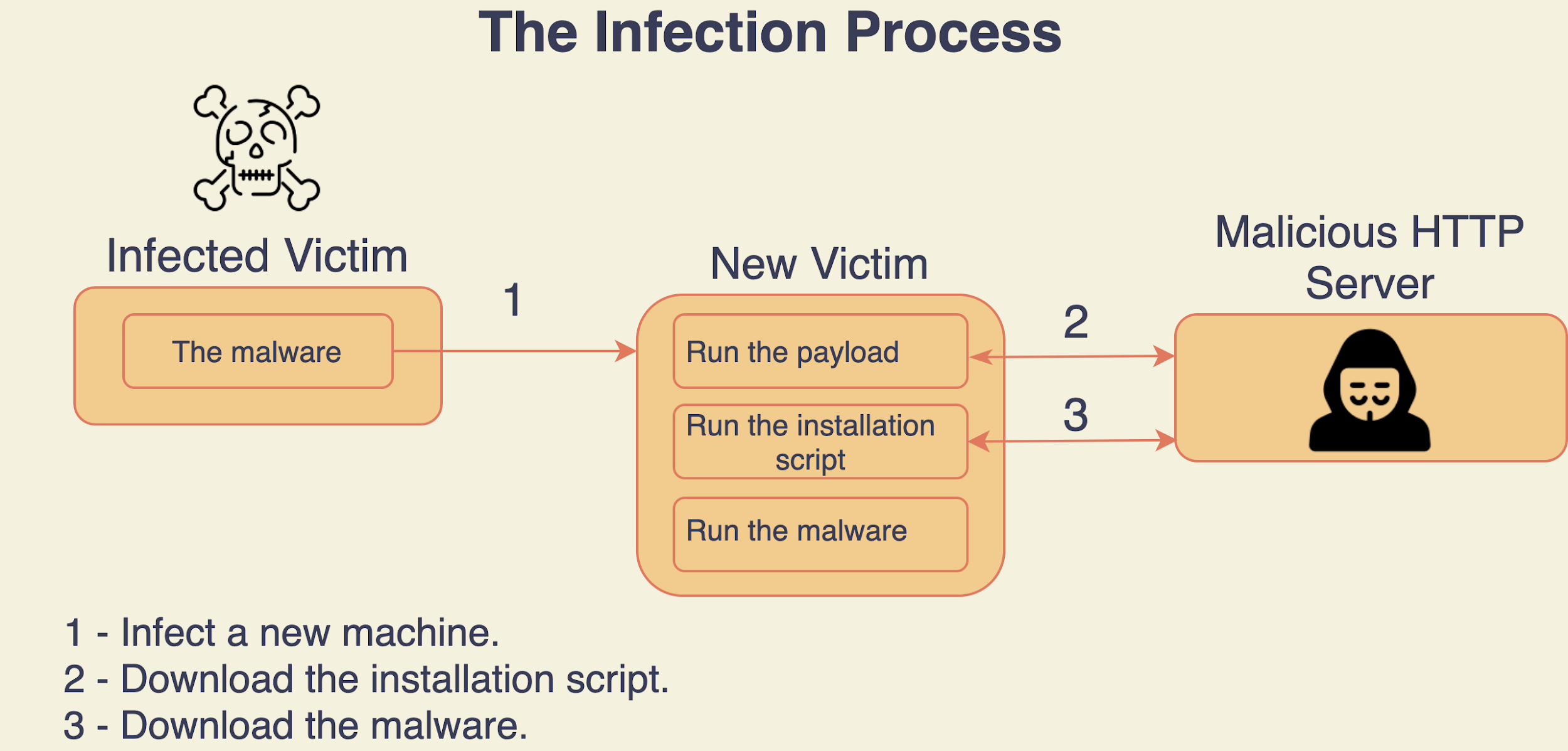
Pro-Ocean attempts to disguise itself as benign, it packs an XMRig miner, which is notorious for its use in cryptojacking operations. The miner seeks to hide using several obfuscation layers on top of the malicious code:
What is UPX in binary?
The binary is packed using UPX. This means that the actual malware is compressed inside the binary and is extracted and executed during the binary execution.
- Advanced static analysis tools can unpack UPX binaries and scan their content. However, in this case, the UPX magic string has been deleted from the binary, and therefore, static analysis tools cannot identify this binary as UPX and unpack it.
- The modules are gzipped inside the unpacked binary.
- The XMRig binary is inside one of the gzipped modules and is also packed by UPX and does not have the UPX magic string.
Pro-Ocean targets several typical cloud applications including Apache ActiveMQ, Oracle Weblogic and Redis, with an emphasis on cloud providers based in China including Alibaba Cloud and Tencent Cloud. It is written in Go and compiled to an x64 architecture binary. It contains four modules that deploy during execution — hiding, mining, infecting and watchdog. Each module contains some files written in various languages (C, Python or Bash) and a Bash script that executes it.
How many cryptojacking cases are there in 2018?
According to Kaspersky Lab Cryptojacking Cases Have Risen 40% in 2018, 13 million cryptojacking incidents in 2018. Also it might become larger in 2019.
CryptoJacking is the top Cybersecurity threat for mining cryptocurrencies in 2018. According to McAfee report, it grows approx 630 percent in the first quarter of 2018. The security researchers also found that, the fake Adobe Flash updates to push mining the cryptocurrencies through Malware.
As we all know Cryptocurrencies boom is on rise. In just few months, many cryptocurrencies have reached their all time high and given a hefty returns to their investors. So some of the Hackers are now finding ways to capitalizing these crypto coins by stealing it from user’s wallets. CryptoJacking is the process of using your computer silently to mine cryptocurrencies.
It’s quite similar to Ransomware. In Ransomware, your computer device infects through a file extension. But in Cryptojacking it infects your computer through a browser.
As we all know many Cryptocurrencies are Mineable. So Cybercriminals are using your computer to mine Cryptocurrency. Hackers are also trying to do some phishing via email by sending you a malicious link in the email that silently execute cryptomining code in your computer background. And by hijacking the website they could even insert malicious code in the victim’s browser.
CryptoJackers are now approaching Ad companies to insert malicious ad code to display it to a wide number of users.
CoinHive is the company which developed the script for Cryptojacking as a revenue alternative.
Cases in 2021
According to another study by SonicWall, 97.1 million cryptojacking attacks were recorded in 2021, the worst year on record for the category.
Cases in 2022
VMware Horizon servers were attacked by mining bots and backdoors using Log4J Vulnerability.
Cryptojacking attackers have taken advantage of the Log4Shell vulnerability in 2022.
The attempts to leverage Horizon, which continued and grew in number throughout January, were frequently associated with attempts to deploy cryptocurrency mining malware; others had less clear motives, and may be associated with initial access brokers or ransomware actors. These attacks continue, Sofos reported.
Cryptojacking issue
In organizations with a significant number of cryptojacked systems, it is a real concern.
As an example: An increase in the cost of electricity.
How to detect CryptoJacking?
There are some basic ways to detect cryptojacking in your Computer:
- If your computer is running very slow and giving poor performance.
- If CPU is heating excessively.
- We can also detect it via Network Monitoring tools.
- There are many artificial intelligence companies which analyzes network data to detect CryptoJacking.
According to report CryptoJacking attacks in UK have surged by 1200 percent in just few months. Earlier in Feburary, Information Commissioner’s office attacked by cybercriminals after insert a crypto mining scripts into a browser plugin.
More than 1400 currencies have existence in the crypto market. A privacy focuses cryptocurrency called Monero is commonly mined by Cryptojackers.
Recently Tesla was hacked for CryptoJacking, there are many open source plugins that allow without a password.
How can we Protect?
- Install Ad blocker and Cryptomining Protection Extensions in your Browser.
- In Chrome, there is a popular protection extension called No Coin to block Coinhive mining.
- Ad blocker plus has capability to detect cryptomining scripts.
- Keep strong Endpoint Protection.
- Always Keep your computer and browser updated.
- Use Anti-Ransomware protection softwares along with your Antivirus.




