
What is Steganography?
Steganography is the art and science of hiding information by embedding messages within other, seemingly harmless images or other types of media.
The word steganography is of Greek origin and means “concealed writing”. The first recorded use of the term was in 1499 by Johannes Trithemius in his Steganographia, a treatise on cryptography and steganography disguised as a book on magic. Generally, messages will appear to be something else: images, articles, shopping lists, or some other covertext and, classically, the hidden message may be in invisible ink between the visible lines of a private letter.
It originated with the Greeks, and it means “covered writing”. It can be traced back for centuries, when messengers used to shave their heads, tattoo the message to their head, then wait until their hair grew back, travel to their destination, and finally shave their head again to reveal the message.
Another technique that was used was etching a message in a wooden tablet, and then covering it with was. They also used invisible ink, null ciphers, and microdots to convey messages. Steganography has come a long way since those days. Now, steganography is the altering of bits in either an image, sound document, or even another document, to hide a message.
Steganography has become increasingly popular in the past years, due to the explosion of the internet and multi-media use in general. Most of the attention has been drawn now because of the malicious use of the technique. It has been used for terrorism, fraud, espionage, etc.
It has become a threat not only to individuals and businesses, but to government agencies and homeland security, not just in the United States, but all across the world. This is why there is now a growing interest in steganalysis, which is the detection of embedded data. The problem is, there are so many methods to embed the information, it is hard to develop programs to distinguish between the different types.
There are over 100 free steganography programs, such as Outguess, available on the internet, and it is reported that there have been over 1 million downloads of this software, which goes to show how popular steganography is becoming. It is not always used in a malevolent manner, some people just like to keep their private information secret, or use it as another way to encrypt important information, but the fact is that it can be used in a criminal way, and that is what the concern is about.
What are some steganography programs?
Not only are there several programs that hide information, there are several different methods for doing so. There are three basic ways: injection, substitution, and generation. With injection, the idea is to find areas in the file that are not being used, like at the end of a song for example, and insert the data in that space.
Substitution finds the least significant bits, and places the hidden document there. Generation creates an entirely new file, based around the information that you want hidden, for example, creating an image of a painting based on the bits that are in the file.
There are also several different programs, with their own methods that all fall under one of the above mentioned categories. Outguess is one such program, it is a universal steganographic tool that allows the insertion of hidden information into the redundant bits of data sources.
It determines the maximum amount of information that can be inserted into a jpeg without changing the statistical counts, making it difficult to find using statistical tests. There are also several others such as S-tools.
Read this : Steganography- How To Use? Data That Hidden Behind Images [TUTORIAL]
What is Steganalysis?
Steganalysis is simply the detection of steganography by a third party. This is a relatively new field, since the new technology behind steganography is just becoming popular.
There are two main types of steganalysis: visual analysis and statistical (algorithmic) analysis.
Visual analysis tries to reveal the presence of hidden information through inspection with the naked eye or with the assistance of a computer, which can separate the image into bit planes for further analysis.
Statistical analysis is more powerful and successful, because it reveals the smallest alterations in an image’s statistical behavior. There are several statistical tests which can be run on an image: average bytes, variations of the bytes, skew, kurtosis, average deviation and differential values.
Technical Steganography
Technical steganography offers a broad variety of methods. It is nearly impossible to divide up all these methods. & Its uses scientific methods to hide a message, such as the use of invisible ink or microdots and other size-reduction methods.
Some methods of technical steganography are:
- Invisible Ink
One of the methods with the longest tradition. - Microdots
A method that can be used to hide up to one page in a dot. - Computer-based Methods
Uses redundant information in texts, pictures, sounds, videos, …
Linguistic Steganography
Linguistic steganography hides the message in the carrier in some nonobvious ways and is further categorized as semagrams or open codes.
Open Codes
The openly readable text is in the case of open codes mostly well constructed. It can contain certain words or sentences, certain letters can be on certain places in the text or words can be hidden in vertical or reversed position.
The main methods are:
Masking
In a text there could be sentences or words starting with certain letters, which have another meaning. There can also be metaphors, etc. In so far all kinds of jargons are in fact masking.
Cues
A certain word appearing in the text transports the message. This message is very often used in wartime to broadcast information to resistance groups in the enemy’s country.
Null-ciphers
The hidden text could be reconstructed by taking the first (second,…) letter of each word (or after the punctuation mark, etc.). Hidden messages could also be found vertically, diagonally or in reversed order. It could also be necessary to re-write the open text in other form (e.g. with a certain number of letters per line).
# Semagrams hide information by the use of symbols or signs. A visual semagram uses innocent-looking or everyday physical objects to convey a message, such as doodles or the positioning of items on a desk or Website. A text semagram hides a message by modifying the appearance of the carrier text, such as subtle changes in font size or type, adding extra spaces, or different flourishes in letters or handwritten text.
As an increasing amount of data is stored on computers and transmitted over networks, it is not surprising that steganography has entered the digital age. On computers and networks, steganography applications allow for someone to hide any type of binary file in any other binary file, although image and audio files are today’s most common carriers.
Steganography provides some very useful and commercially important functions in the digital world, most notably digital watermarking. In this application, an author can embed a hidden message in a file so that ownership of intellectual property can later be asserted and/or to ensure the integrity of the content.
An artist, for example, could post original artwork on a Website. If someone else steals the file and claims the work as his or her own, the artist can later prove ownership because only he/she can recover the watermark.
Although conceptually similar to steganography, digital watermarking usually has different technical goals. Generally only a small amount of repetitive information is inserted into the carrier, it is not necessary to hide the watermarking information, and it is useful for the watermark to be able to be removed while maintaining the integrity of the carrier.
Also See: Sherloq – Forensic Image Analysis Suite [TUTORIAL]
Top 10 Steganography Tools –
1. S Tools – It helps to detect the hidden message.
Also, it’s good illustration of different versions hiding in different media. These versions cover hiding in BMP, GIF, WAV, and even on unused floppy disk space.
Download:- http://www.spychecker.com/program/stools.html
2. MP3Stego.
which hides text files within larger text files, and lastly a tool that hides files in MP3s called MP3 Stego
Download:- http://www.petitcolas.net/fabien/steganography/mp3stego/index.html
3. Steganos Suite
Tested one commercial steganography product, Steganos Suite.
4. OpenStego
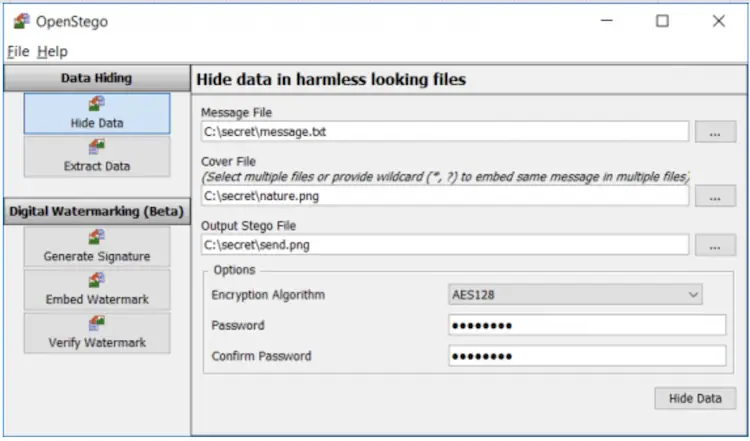
OpenStego provides two main functionalities:
Data Hiding: It can hide any data within a cover file (e.g. images).
Watermarking (beta): Watermarking files (e.g. images) with an invisible signature. It can be used to detect unauthorized file copying.
Download:- https://www.openstego.com/
5. Dmagic.
Hides files and folders on Windows systems
6. Hermetic Stego
by Peter Meyer, Hermetic Systems This program is capable of hiding in a BMP image or across multiple BMP images.
Download:- http://www.hermetic.ch/hst/hst.htm
7. jpeg-jsteg
DOS hides information in the DCT coefficients of JPEG’s JFIF image format.
Download:- http://www.nic.funet.fi/pub/crypt/steganography/
8. Snow
Snow (also variants include !SnowDOS, SnowJava, JSnow By Matthew Kwan is available in both DOS and JAVA executable formats. “snow exploits the steganographic nature of whitespace. Locating trailing whitespace in text is like finding a polar bear in a snowstorm. And it uses the ICE encryption algorithm, so the name is thematically consistent.
Download:- http://www.darkside.com.au/snow/index.html
9. Steghide
Source code is available and several ports are available for different operating systems. IMAGES: (BMP) AUDIO: (WAV, AU )
Download :- http://steghide.sourceforge.net/
10. wbStego
wbStego is a steganography to hide data in bitmaps, text files and HTML files.
Download:- http://www.8ung.at/wbailer/wbstego/
Also Read: How To Hide Files in Kali Linux?




