All The Tools Are Used For Computer Security And Internet Security..!!
SSL Configuration Tool SSLyze v 0.6
SSLyze is a Python tool that can analyze the SSL configuration of a server by connecting to it. It is designed to be fast and comprehensive, and should help organizations and testers identify misconfigurations affecting their SSL servers.
Features
- SSL 2.0/3.0 and TLS 1.0/1.1/1.2 compatibility
- Performance testing: session resumption and TLS tickets support
- Security testing: weak cipher suites, insecure renegation, CRIME and THC-SSL DOS attacks
- Server certificate validation
- Support for StartTLS with SMTP and XMPP, and traffic tunneling through an HTTPS proxy
- Client certificate support for servers performing mutual authentication
- Scan results can be written to an XML file for further processing
Download:
Linux/OSX – sslyze-0.6_src.zipsslyze-0.6_src.zip
Windows 7/Python 32-bit – sslyze-0.6_Windows7_Python32.zip
Windows 7/Python 64-bit – sslyze-0.6_Windows7_Python64.zip
Joomla Security Scanner:
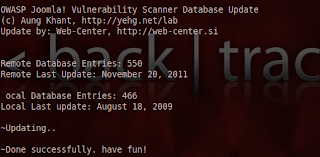
Joomscan Security Scanner updated recently with new database have 550 vulnerabilities. Detects file inclusion, sql injection, command execution vulnerabilities of a target Joomla web site. Last update for this tool was in August, 2009 with 466 vulnerabilities.
Download for Windows (141 KB)
Download for Linux (150 KB)
Process Explorer:
ProcessExplorer for keeping an eye on the files and directories open by any process.
CCleaner:
CCleaner is a freeware system optimization, privacy and cleaning tool. It removes unused files from your system – allowing Windows to run faster and freeing up valuable hard disk space. It also cleans traces of your online activities such as your Internet history. Additionally it contains a fully featured registry cleaner. But the best part is that it’s fast (normally taking less than a second to run) and contains NO Spyware or Adware! 🙂
VeraCrypt: Open Source Free Disk Encryption:
It adds enhanced security to the algorithms used for system and partitions encryption making it immune to new developments in brute-force attacks.
This is acceptable to the legitimate owner but it makes it much more harder for an attacker to gain access to the encrypted data.
VeraCrypt storage format is INCOMPATIBLE with TrueCrypt storage format. Hidden volume (steganography) and hidden operating system. Read more
Comodo Internet Security:
Comodo claim that their firewall is unique in that it passes all known leak tests to ensure the integrity of data entering and exiting your system. Comodo has put firewall through all kinds of sophisticated tests to ensure its firewall powerful enough to ward off these attacks with default settings. No other firewall has had to work this hard.
Features:-
- Secures against internal and external attacks
- Blocks internet access to malicious Trojan programs
- Safeguards your Personal data against theft
- Delivers total end-point security for Personal Computers and Networks
HiJackThis:
Trend Micro HijackThis is a free utility that generates an in depth report of registry and file settings from your computer. HijackThis makes no separation between safe and unsafe settings in its scan results giving you the ability to selectively remove items from your machine. In addition to this scan and remove capability HijackThis comes with several tools useful in manually removing malware from a computer.
HijackThis inspects your computers browser and operating system settings to generate a log file of the current state of your computer. Using HijackThis you can selectively remove unwanted settings and files from your computer. Because the settings identified in a HijackThis log file can belong to both legitimate software and unwanted malware, it is important to use extreme caution when choosing to removing anything using HijackThis.
HijackThis also comes with a process manager, HOSTS file editor, and alternate data stream scan.
Rootkit Hunter – Rootkit scanning tool
Rootkit scanner is scanning tool to ensure you for about 99.9%* you’re clean of nasty tools. This tool scans for rootkits, backdoors and local exploits by running tests like:
– MD5 hash compare
– Look for default files used by rootkits
– Wrong file permissions for binaries
– Look for suspected strings in LKM and KLD modules
– Look for hidden files
– Optional scan within plaintext and binary files




