In our previous article we have discussed about the “Payload Processing Rule in Burp Suite Series – (Part 1) “, and the topics have covered on that Part are Add prefix, Add suffix, Match / Replace, Substring, Reverse substring, Modify case.
Now in this part we are going to cover Encode, Decode, Hash, Add raw payload, Skip if matches regex, Invoke Burp extension Payload Processing Rule in the Burp suite.
So let’s start…
Encode
The processing rule can be used to encode a payload using a variety of schemes such as URL, HTML, Base64, ASCII hex, or built-in strings.
For example we want to encode username and password in Base 64.
First, ensure that Burp is correctly configured with your browser.
Follow the steps.
To configure Burp Suite demonstrate.
First Go to your browser settings and in the search box type proxy, then select open proxy settings > In connection tabs > Lan settings > Tick Use a proxy server for your LAN > (127.0.0.1 port number 8080) then Click ok.

Now open Burp Suite.
In the Burp Proxy tab, ensure “Intercept is off” and visit the login page of the application, which you are testing in your browser.

Turn on Intercept

Demonstrate Link Web For Pentester II for testing
In your browser, enter the default username and wrong password, then submit the request to intercept the browser request using a burp suite.

This is a example of Web For Pentester II authentication example 1 where authorization is basic level in this username:password is encoded in base64
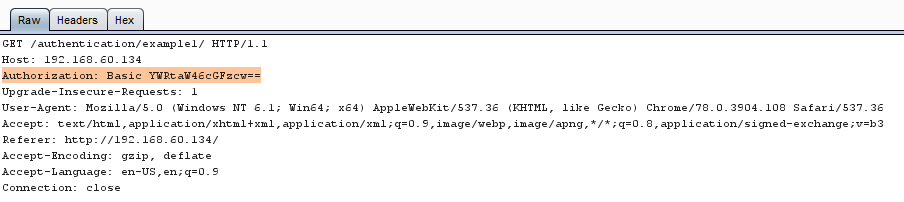
Right click on the request to bring up the context menu and click “Send to Intruder.”
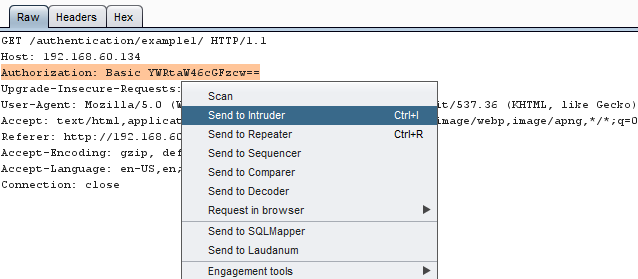
Then select the Positions tab and follow the below steps:
- Change the attack to “Sniper” using the “Attack type” drop down menu.
- Clear the pre-set payload positions by using the “Clear” button on the right of the request editor and click add for set payload.
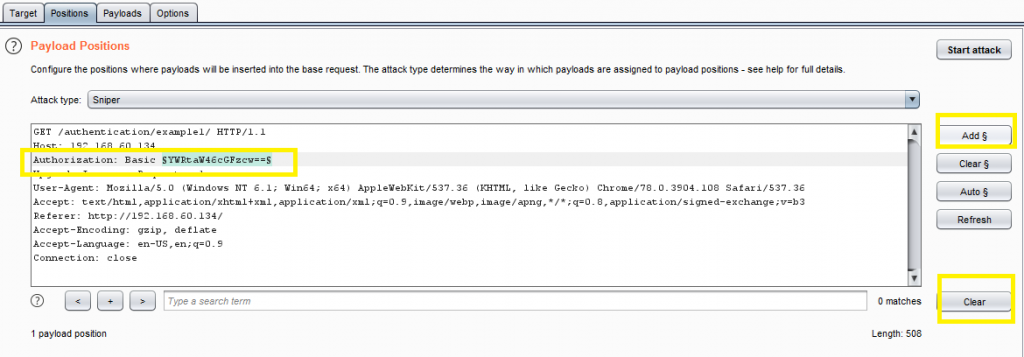
Go to the “Payloads” tab. In the “Payload sets” settings, ensure “Payload set” is “1” and Payload type as Simple list, where we have added a dictionary by clicking on Load button.
Here, we can either load the dictionary or manually add input strings using the Add button in the payload options.
The base 64 encode value of authentication is a combination of username and password.
so created username and password like
admin:password
admin:password123
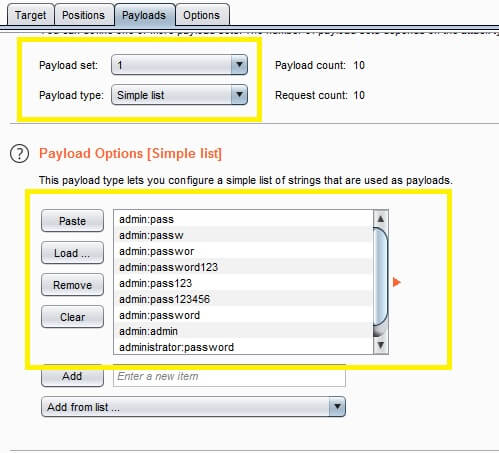
Now click on add payload processing rule.The payload processing rule is encoded for the payload type and we chose the “base 64 encode” scheme because we know that the web application is taking the value in base 64 and then click ok.

After that Select Start Attack in the Intruder menu.
In the “Intruder attack” window, you can sort the results using the column headers.
In this example sort by “Length” and by “Status.”
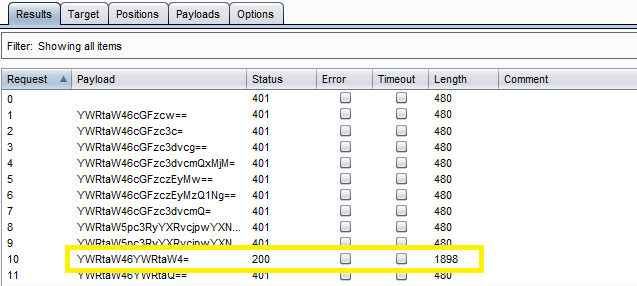
The above image is confirm the username and password matched, we will give the password in the Web application Login Page, which will successfully logged in as a admin.
Decode
This processing rule can be used to decode the payload using various schemes: URL, HTML, Base64 or ASCII hex. As we know, decoding is nothing but reverse encoding. It can be used in the opposite way of carrying out encoding. it’s same as the previous example main difference is it decode the encoded value.
Hash
This processing rule can be used to perform hashing operations on the payload. There are 7 types of hashing algorithms available in this payload processing clause, which is SHA, SHA-224, SHA-256, SHA-384, SHA-512, MD2, MD5.
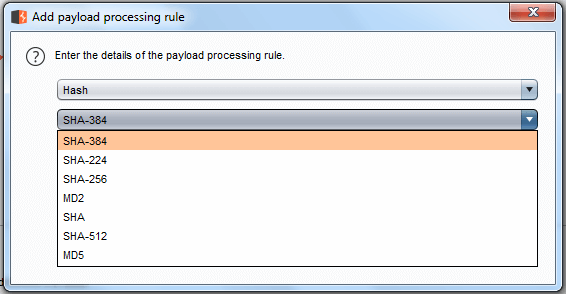
Example by applying process rule md5 viewing the response in the attack window, we can see that request 1982 is log us in.
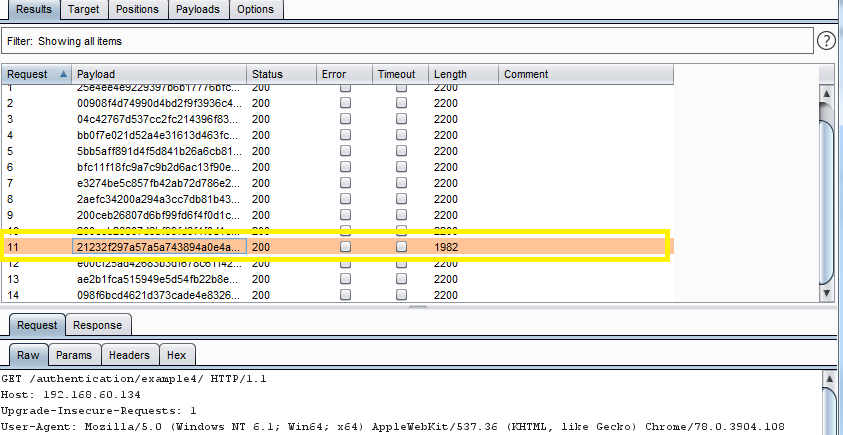
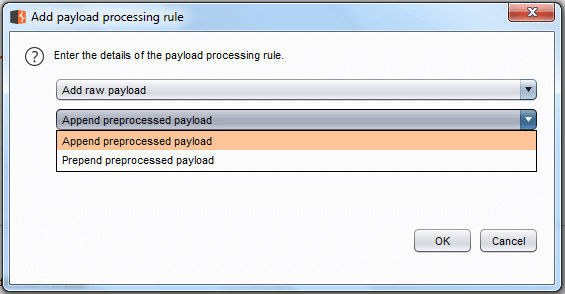
Add Raw Payload
This processing rule can be used to add a raw payload value before or after the current processing value.
For example, this payload is useful, whenever you want to submit the same payload in raw and hash form.
Example of append preprocessed payload
user to useruser
admin to adminadmin
pass to passpass
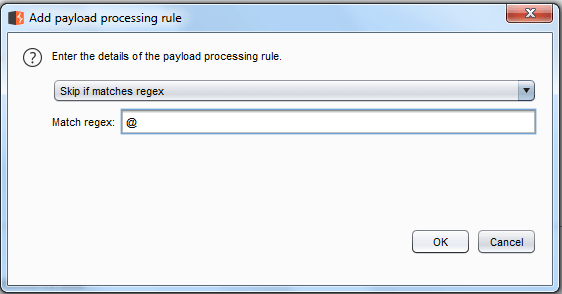
Skip if Matches Regex
This processing rule is used to match the current expression value with the specified regular expression, and if it matches, it skips the payload and moves on to the next one. For example, suppose we have a parameter value that is a minimum length and is less than the minimum length that we want to define the values in the list.
Example: The payload processing rule for payload type is Skip if it matches the regex, where we have given the input of {@} of in the match regex field. As a rule, any input in a dictionary with input strings is omitted and passed on to the next one and the output will be like:
- [email protected] to skaufman
- [email protected] to fraser
- [email protected] to loscar
- [email protected] to adillon
- [email protected] to andersbr
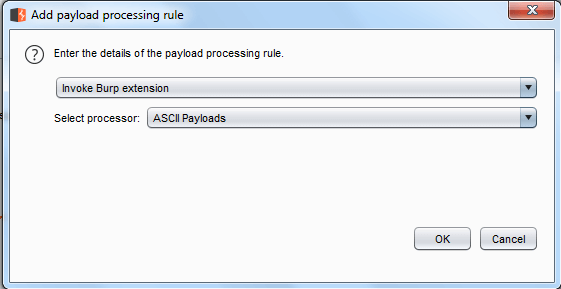
Invoke Burp extension
source : portswigger.net
This invokes a Burp extension to process the payloads. The extension must have registered an Intruder payload processor. You can select the required processor from the list of available processors that have been registered by currently loaded extensions.
Burp Extender lets you use Burp extensions, to extend Burp’s functionality using your own or third-party code. You can load and manage extensions, view details about installed extensions, install extensions from the BApp Store, view the current Burp Extender API, and configure options for how extensions are handled.
Watch Video Tutorial