-
Site Isolation Feature update for all desktop users.
-
Site Isolation also offers more protection against a different type of browser security bug.
-
Meltdown and Spectre Bug protection uses 10 to 13 percent Desktop RAM
Google Updated its Chrome 67 Browser with a new security feature called ‘Site Isolation’ for all desktop users including Windows, Mac, Linux, and Chrome OS platforms.
It helps to protect against online threats including Spectre and Meltdown vulnerability. These vulnerabilities allow programs to steal data which is currently processed on the computer.
What is Site Isolation?
Site Isolation is a security feature in Chrome that offers additional protection against some types of security bugs. It makes it harder for untrustworthy websites to access or steal information from your accounts on other websites, according to the blog.
Site Isolation offers a second line of defense to make such attacks less likely to succeed. It ensures that pages from different websites are always put into different processes, each running in a sandbox that limits what the process is allowed to do. It will also make it possible to block the process from receiving certain types of sensitive data from other sites. As a result, a malicious website will find it more difficult to steal data from other sites, even if it can break some of the rules in its own process.
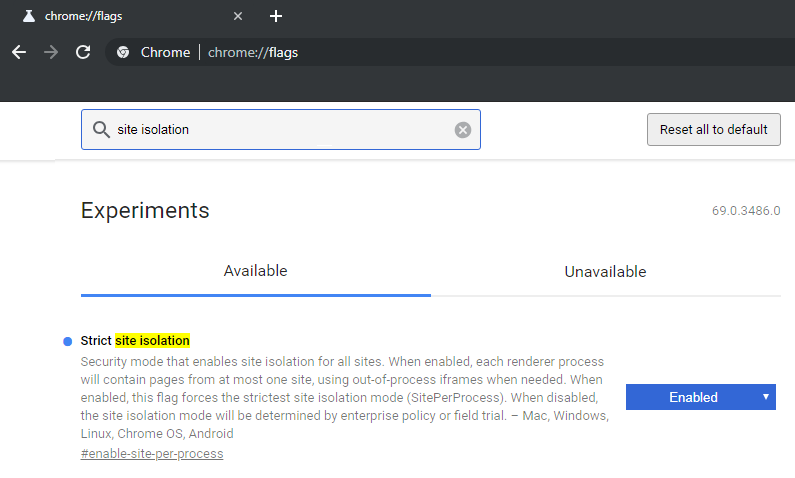
Just type >> chrome://flags on to your Browser.
Few issues still remains in a Desktop Chrome Browser
- Higher overall memory use in Chrome (about 10-13% in Chrome 67 when isolating all sites with many tabs open).
- Clicks on hidden cross-site iframes do not work. This is expected to be relatively uncommon in practice.
- Certain sites might have printing issues with cross-site subframes. Saving the page locally and then printing can work around the bug.
- A few additional clicking and scrolling issues may be observed on certain sites. Fixes for many of these are already in Chrome 68.
“Isolating All Sites” also works on Chrome for Android, but only via chrome://flags#enable-site-per-process.
Site Isolation reduces the amount of valuable cross-site information in a web page’s process, and thus helps limit what an attacker could access.
In addition, Site Isolation also offers more protection against a different type of browser security bug, called universal cross-site scripting (UXSS). Security bugs of this form would normally let an attacker bypass the Same Origin Policy within the renderer process though they don’t give the attacker complete control over the process. Site Isolation can help protect sites even when some forms of these UXSS bugs occur.
This protection is made possible by the following changes in Chrome’s behavior:
- Cross-site documents are always put into a different process, whether the navigation is in the current tab, a new tab, or an iframe (i.e., one web page embedded inside another).
- Cross-site data (specifically HTML, XML, and JSON files) is not delivered to a web page’s process unless the server says it should be allowed (using CORS).
- There is additional work underway to let Site Isolation offer protection against even more severe security bugs, where a malicious web page gains complete control over its process (also known as “arbitrary code execution”). These protections are not yet fully in place.