Security Researcher Omar Espino found LFI Vulnerability on Google Production Server.
He shared the Proof of Concept (POC) for Hackersonlineclub readers as following
GOOGLE BUG BOUNTY: LFI ON PRODUCTION SERVERS IN “SPRINGBOARD.GOOGLE.COM” – $13,337 USD
Hi everyone It’s been a while from my last post but I’m back , I want to tell you a short story about my greatest find so far (My first P1), It was in Google VRP program and why you can always check for dirs in 301 / 302 / 403 / 404 status pages because you will surprise that some times some directories listing will work:
FIRST ROUND
Title: Auth bypass in springboard.google.com Product / URL: springboard.google.com/REDACTED_DIR
Report sent via google VRP program https://goo.gl/vulnz
Summary:
Authorization bypass in https://springboard.google.com/REDACTED_DIR and see “OnContent Debug for” mini dashboard
POC:
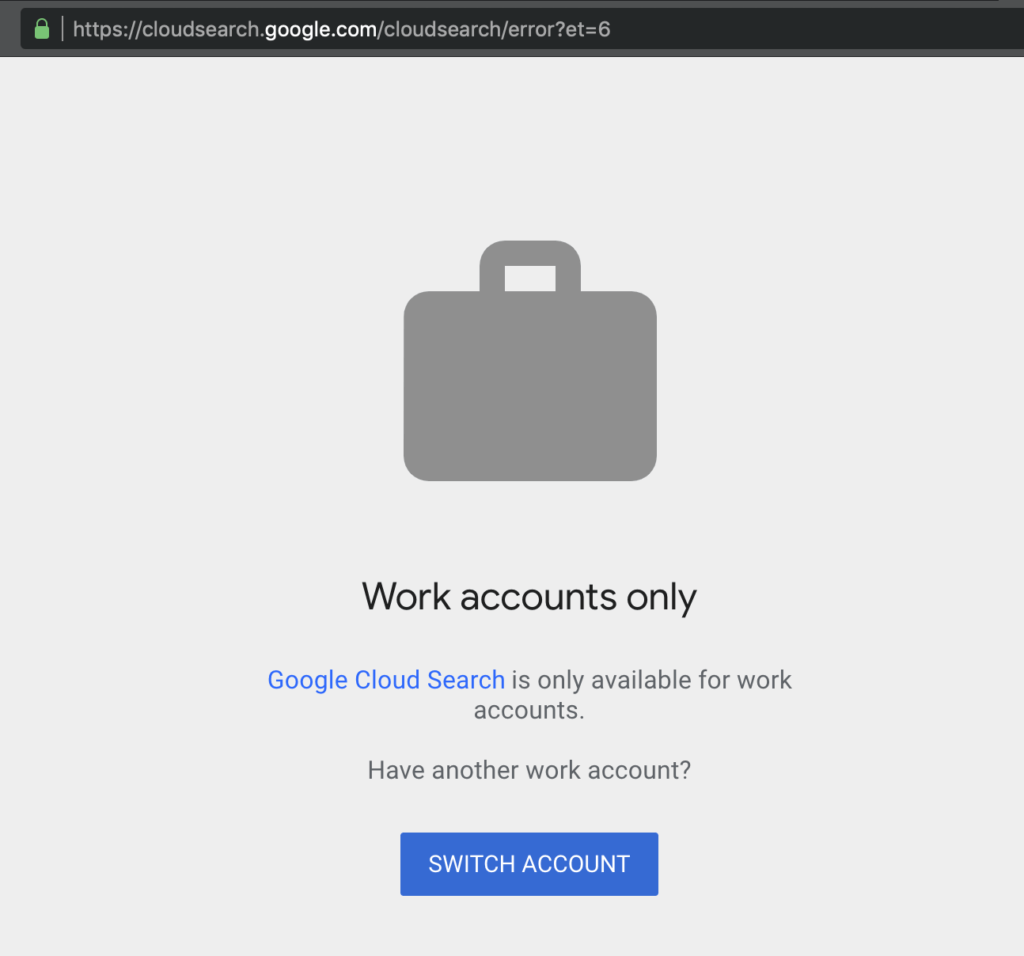
1.- Go to https://springboard.google.com/ and got redirected to https://cloudsearch.google.com/cloudsearch/error?et=6 and see the message
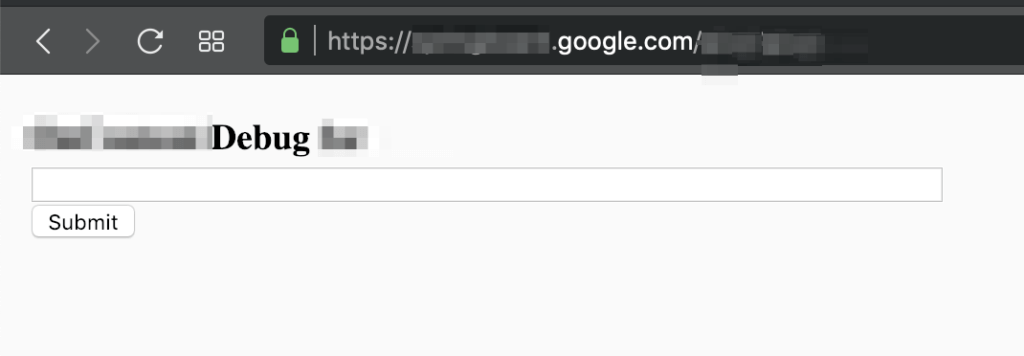
2.- Then navigate to https://springboard.google.com/REDACTED_DIR and see a mini dashboard with the form:
3 days after that I got a message:
At first glance, this might not be severe enough to qualify for a reward, though the panel will take a look shortly.
Spoiler:
Unfortunately, after a week, I got the reply that from google VRP Panel:
“As a part of our Vulnerability Reward Program, we decided that it does not meet the bar for a financial reward“
SECOND ROUND
Since the bug probably won’t be elegible to get a financial reward, I started thinking to go deeper on that “Auth bypass”, I mean, for some reason is not suppoused to be open, so I decided to try again, then after some new dir enumeration with wfuzz, I got something really really interesting, I was able to escalate that simple Auth bypass bug to LFI on production servers as admin in google production servers.
Title: LFI on production servers in the same subdomain Product / URL: springboard.google.com/REDACTED_DIR/ANOTHER_DIR
Summary:
I’ve able to escalate this auth bypass to LFI on google production servers as “gxx-xxxx” user (admin privileges)!
POC:
1.- First see that the dashboard panel of “Redacted status main” (FrameworkInfo) is open in https://springboard.google.com/REDACTED_DIR/ANOTHER_DIR
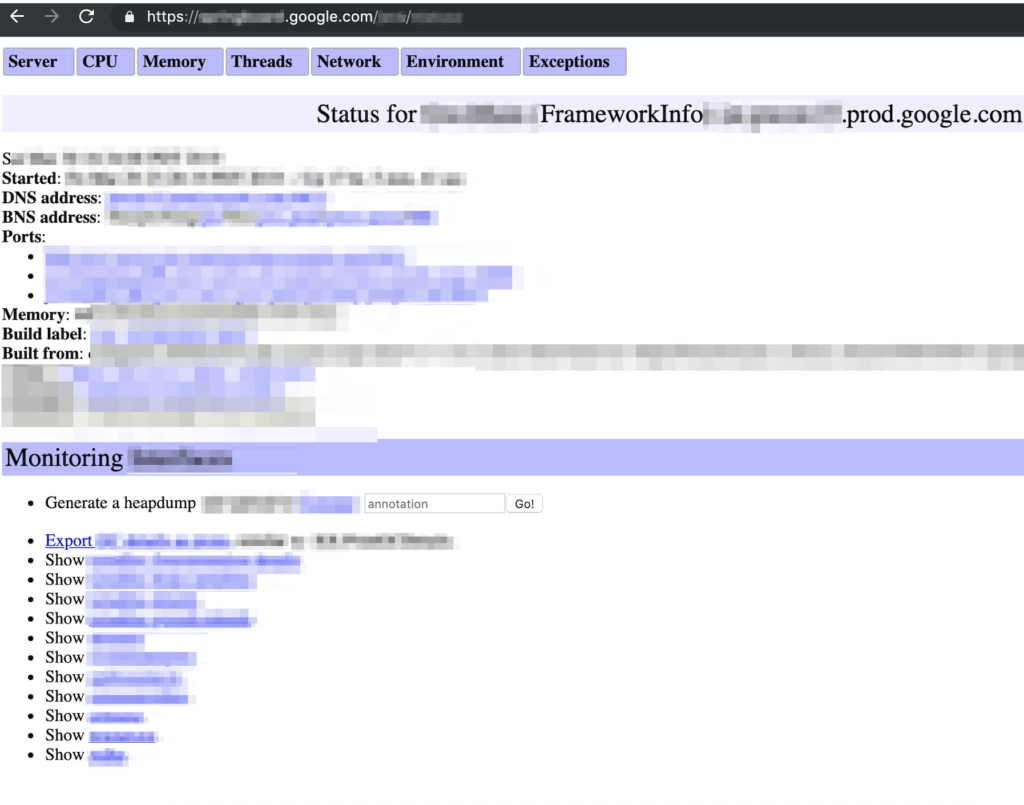
2.- Then if you navigate to “Show REDACTED” (The last option) you are going to be redirected to https://springboard.google.com/REDACTED_DIR/ANOTHER_DIR?file=/proc/self/environ and the /proc/self/environ will be loaded

3.- Just to be sure that was a full LFI working I tried to load another file and I checked with /proc/version and works just as expected!

Then my heart stopped for a second, I just got a LFI on google production servers as administrator (servers on plural because each time that I refreshed /proc/self/environ file the hostname changed)
To be honest I tried to escalate to RCE but I hadn’t any success, since apparently it was very hardened I wasn’t able to read /proc/*/fd, ssh keys, server keys or any logs.
Environment
Any browser (I used Google Chrome Lastest version)
No authentication or any Google account was needed
Google HOF (May 2019)
Vulnerability Reporting Timeline
- Mar 22, 2019: Sent the report to Google VRP (Just the bypass auth part)
- Mar 22, 2019: Got a message from google that the bug was triaged
- Mar 25, 2019: Bug Accepted
- Mar 25, 2019: Reply about that the bug was in revision in Googgle VRP panel
- Mar 30, 2019: I found the LFI and sent the new POC in the same report
- Apr 1, 2019: Got a message saying that they going to fill a another bug with this LFI information
- Apr 4, 2019: Got a message saying that the first bug wasn’t elegible for financial reward
- Apr 17 ,2019: Since the everything was happening in the same report and the bugs were fixed, I asked to the team if the 2 bugs wasn’t elegibles or what happened
- Apr 23, 2019: Got a message saying that sorry about the confusion and I just had to wait to a new reward decision for the LFI part.
- May 21 2019: $13,337 bounty and permission to publish this write up received
well that’s it, share your thoughts, what do you think about how they handle that security issue? if you have any doubt, comment or suggestion you can ask on twitter @omespino.
We would like to congratulate to Omar Espino for great find and Hall of Fame in Google
Omar Espino has received the Hall of Fame from top of the companies like Microsoft, Google, Facebook, Twitter, Telegram, Slack, Yahoo, Nokia, Atlassian, Sony. You can read his blog for other vulnerability research.