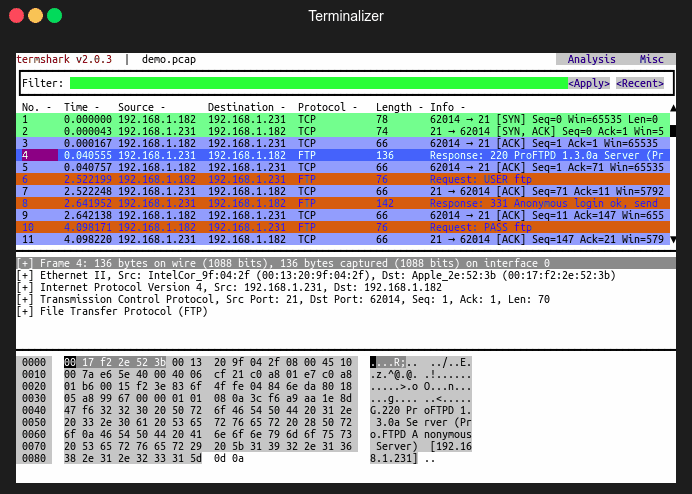
Termshark is a terminal User Interface (UI) for tshark, inspired by Wireshark.
It provides a terminal-based user interface for analyzing packet captures, and depends on tshark for all its intelligence.
Features
- Read pcap files or sniff live interfaces.
- Use Wireshark’s display filters.
- Reassemble TCP and UDP streams.
- View conversations by protocol.
- Written in Go – for Linux, macOS, FreeBSD, Android (termux) and Windows.
Termshark is run from the command-line and it is terminal user-interface for tshark.
What’s new in Termshark 2.1 version.
- Now provides a conversations view for the most common conversation types.
- Now supports multiple live captures/interfaces on the command-line e.g. termshark -i eth0 -i eth1
- Termshark’s packet hex view displays a scrollbar if the data doesn’t fit in the space available.
- Termshark can show a capture file’s properties using the capinfos binary (bundled with tshark).
- Now supports extcap interfaces by default.
The extcap interface is a versatile plugin interface that allows external binaries to act as capture interfaces directly in wireshark. It is used in scenarios, where the source of the capture is not a traditional capture model (live capture from an interface, from a pipe, from a file, etc). The typical example is connecting esoteric hardware of some kind to the main wireshark app.
Also See: Wireshark Commands Cheatsheet
Install Packages
Termshark is pre-packaged for Arch Linux, Debian (unstable), FreeBSD, Homebrew, Kali Linux, NixOS, SnapCraft, Termux (Android) and Ubuntu platforms.
Quick Start
Inspect a local pcap:
termshark -r test.pcap
Capture ping packets on interface eth0:
termshark -i eth0 icmp
Run termshark -h for options.
Usage
termshark [FilterOrFile]
Application Options:
- -i=<interfaces> Interface(s) to read.
- -r=<file> Pcap file to read.
- -d=<layer type>==<selector>,<decode-as protocol> Specify dissection of layer type.
- -D Print a list of the interfaces on which termshark can capture.
- -Y=<displaY filter> Apply display filter.
- -f=<capture filter> Apply capture filter.
- -t=<timestamp format>[a|ad|adoy|d|dd|e|r|u|ud|udoy] Set the format of the packet timestamp printed in summary lines.
- –tty=<tty> Display the UI on this terminal.
- –pass-thru=[auto|true|false] Run tshark instead (auto => if stdout is not a tty). (default: auto)
- –log-tty Log to the terminal.
- -h, –help Show this help message.
- -v, –version Show version information.
Arguments:
FilterOrFile: Filter (capture for iface, display for pcap), or pcap file to read.
If –pass-thru is true (or auto, and stdout is not a tty), tshark will be executed with the supplied command-line flags. You can provide tshark-specific flags and they will be passed through to tshark (-n, -d, -T, etc).
For example:
$ termshark -r file.pcap -T psml -n | less
Reading from an Interface
Launch termshark like this to read from an interface:
termshark -i eth0
You can also apply a capture filter directly from the command-line:
termshark -i eth0 tcp
Termshark will apply the capture filter as it reads, but the UI currently does not provide any indication of the capture filter that is in effect.
Termshark supports reading from more than one interface at a time:
termshark -i eth0 -i eth1
You can see the full working here
Download Termshark 2.1 Version here