The Microsoft Threat Intelligence Center (MSTIC), NOBELIUM, the threat actor behind SolarWinds’ attacks, the SUNBURST backdoor, TEARDROP malware, GoldMax malware, and other related components. Allegedly been sending out malicious emails that target SolarWinds users on a mass scale.
Over 150 organizations were targeted in this wave of attacks, which affected over 3,000 email accounts. At least 24 countries have been targeted by targeted attacks, although the majority of attacks have targeted organizations in the United States. More than a quarter of the targeted organizations were involved in international development, humanitarian, and human rights work. Russia-based Nobelium was the same actor behind SolarWinds’ attacks in 2020.
Microsoft first spotted and tracked the campaign in January 2021, have observed the campaign evolve over several waves that illustrate significant experiments.
NOBELIUM has historically targeted government organizations, non-government organizations (NGOs), think tanks, military, IT service providers, health technology and research, and telecommunications providers. With this latest attack, NOBELIUM attempted to target approximately 3,000 individual accounts across more than 150 organizations, employing an established pattern of using unique infrastructure and tooling for each target, increasing their ability to remain undetected for a longer period of time.
The security firm Volexity published, On May 25, 2021, the company identified a phishing campaign targeting multiple organizations based in the United States and Europe. The following industries have been observed being targeted thus far:
- NGOs
- Research Institutions
- Government Agencies
- International Agencies
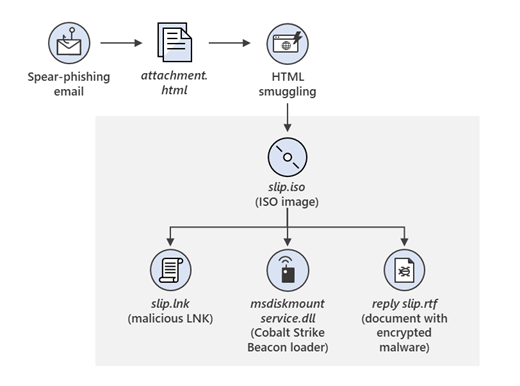
“The campaign’s phishing e-mails purported to originate from the USAID government agency and contained a malicious link that resulted in an ISO file being delivered. This file contained a malicious LNK file, a malicious DLL file, and a legitimate lure referencing foreign threats to the 2020 US Federal Elections.”
Once clicked, inserted a malicious file used to distribute the NativeZone backdoor. In addition to stealing data, this backdoor can also infect other computers on a network.
MSTIC observed NOBELIUM attempting to compromise systems through an HTML file attached to a spear-phishing email. When opened by the targeted user, a JavaScript within the HTML wrote an ISO file to disc and encouraged the target to open it, resulting in the ISO file being mounted much like an external or network drive. From here, a shortcut file (LNK) would execute an accompanying DLL, which would result in Cobalt Strike Beacon executing on the system.
This new wide-scale email campaign leverages the legitimate service Constant Contact to send malicious links that were obscured behind the mailing service’s URL (many email and document services provide a mechanism to simplify the sharing of files, providing insights into who and when links are clicked).
Due to the high volume of emails distributed in this campaign, automated email threat detection systems blocked most of the malicious emails and marked them as spam. However, some automated threat detection systems may have successfully delivered some of the earlier emails to recipients either due to configuration and policy settings or prior to detections being in place.