Browsing Tag
Information Security
60 posts
Sysreptor – Offensive Security Reporting Solution For Pentesters
SysReptor is a customizable offensive security reporting solution for security professionals, including pentesters and red teamers. You can…
April 17, 2024
Understanding LLM Security: Threats, Applications, and Everything In-Between
New technology called LLMs is making a big difference. These LLMs can have real conversations and write creative…
April 2, 2024
INDIA Fights Cybercrime with Two New Initiatives: Digital Intelligence Platform (DIP) And Chakshu
India has taken a significant step towards curbing cybercrime and financial fraud with the launch of two new…
March 7, 2024
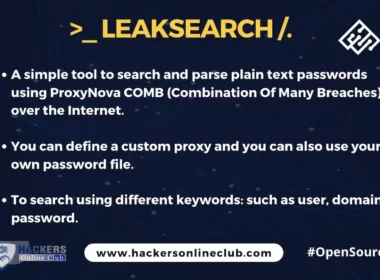
Leaksearch – To Search and Parse Plain Text Passwords Using ProxyNova
LeakSearch is a simple tool to search and parse plain text passwords using ProxyNova COMB (Combination Of Many…
March 5, 2024
US President Biden Signed Order To Protect Americans Personal Data
The U.S. government is blocking the mass transfer of American personal data to high-risk nations. This is being…
March 1, 2024
What is Application Security Testing (AST)?
Applications are the gateways to our data, systems, and even identities. With this growing reliance comes a heightened…
February 27, 2024
Google Magika: Open-Sourcing AI-Powered File Type Identification
Google has announced the open-sourcing of Magika, an AI-powered file type identification system. This move aims to empower…
February 21, 2024
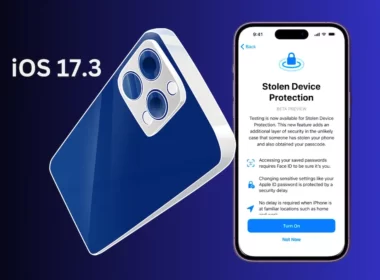
Apple Stolen Device Protection: A Shield For Your iPhone in Unexpected Hands
Apple has introduced a new security feature called iPhone Stolen Device Protection within iOS 17.3, aiming to empower…
January 25, 2024
Alert! Fake Recruiters on Facebook: Unmasking Remote Jobs SCAM – Protection
Attention! Beware of fake recruiters on Facebook who claim to offer remote jobs. The rise of remote work…
January 12, 2024
What to do if I think I’ve been hacked? Checklist
Uh-Oh, Hacked? Don’t Freak Out, Fix It! Think someone broke into your online life? It’s scary, but don’t…
January 9, 2024