Browsing Tag
Network
67 posts
Microsoft ICS Forensics Framework
Microsoft ICS Forensics framework is an open source forensic framework for analyzing Industrial PLC metadata and project files.…
November 29, 2023
Exploring VPN Alternatives: Secure Solutions
Exploring VPN Alternatives: Secure Solutions For Safer Online Experience. In a time where online privacy is increasingly scrutinized,…
November 28, 2023
SSE vs. Traditional Security Models – The Variances
In today’s hyper-connected digital world, cybersecurity stands as a paramount concern, with organizations seeking robust solutions to protect…
November 20, 2023
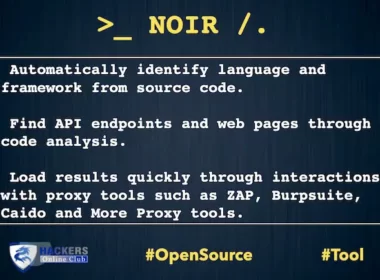
NOIR Network Attack Surface Detector From Source Code
Noir An Network Attack Surface Detect and Analysis From Source Code Key Features Automatically identify language and framework…
September 7, 2023
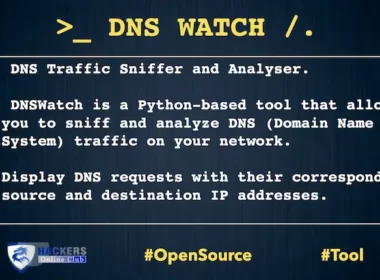
DNSWatch – DNS Traffic Sniffer And Analyzer
DNSWatch is a Python-based tool that allows you to sniff and analyze DNS (Domain Name System) on your…
September 1, 2023
Online Security Essentials For A Start-Up
Starting a new business venture brings with it an exciting array of challenges and opportunities. In the digital…
July 20, 2023
Empowering Secure And Reliable Data Collection With Backconnect Proxies
With e-commerce booming and digital marketing becoming the dominant mode of building customer engagement, more and more companies…
June 29, 2023
Zero-Trust Security: The Future of Data Protection
In today’s interconnected AI world, where cyber threats constantly evolve, traditional security measures are no longer sufficient to…
June 10, 2023
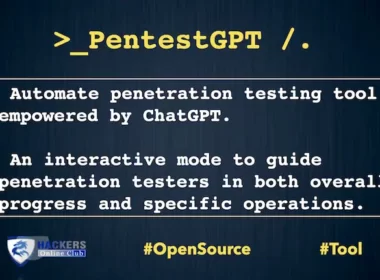
PentestGPT – Automate Penetration Testing Empowered by ChatGPT
PentestGPT Automate Penetration Testing for OSCP-like machine: HTB-Jarvis. This is the first part only. PentestGPT on HTB-Lame. This…
May 15, 2023
3 IoT Security Vulnerabilities To Be Aware Of
If an organization is targeted by hackers in 2023, the incident will highly likely involve poorly protected IoT…
May 9, 2023