reconftw – Simple Script For Full Recon
Summary
This is a simple script intended to perform a full recon on an objective with multiple subdomains.
ReconFTW automates the entire process of reconnaissance for you. It outperforms the work of subdomain enumeration along with various vulnerability checks and obtaining maximum information about your target.
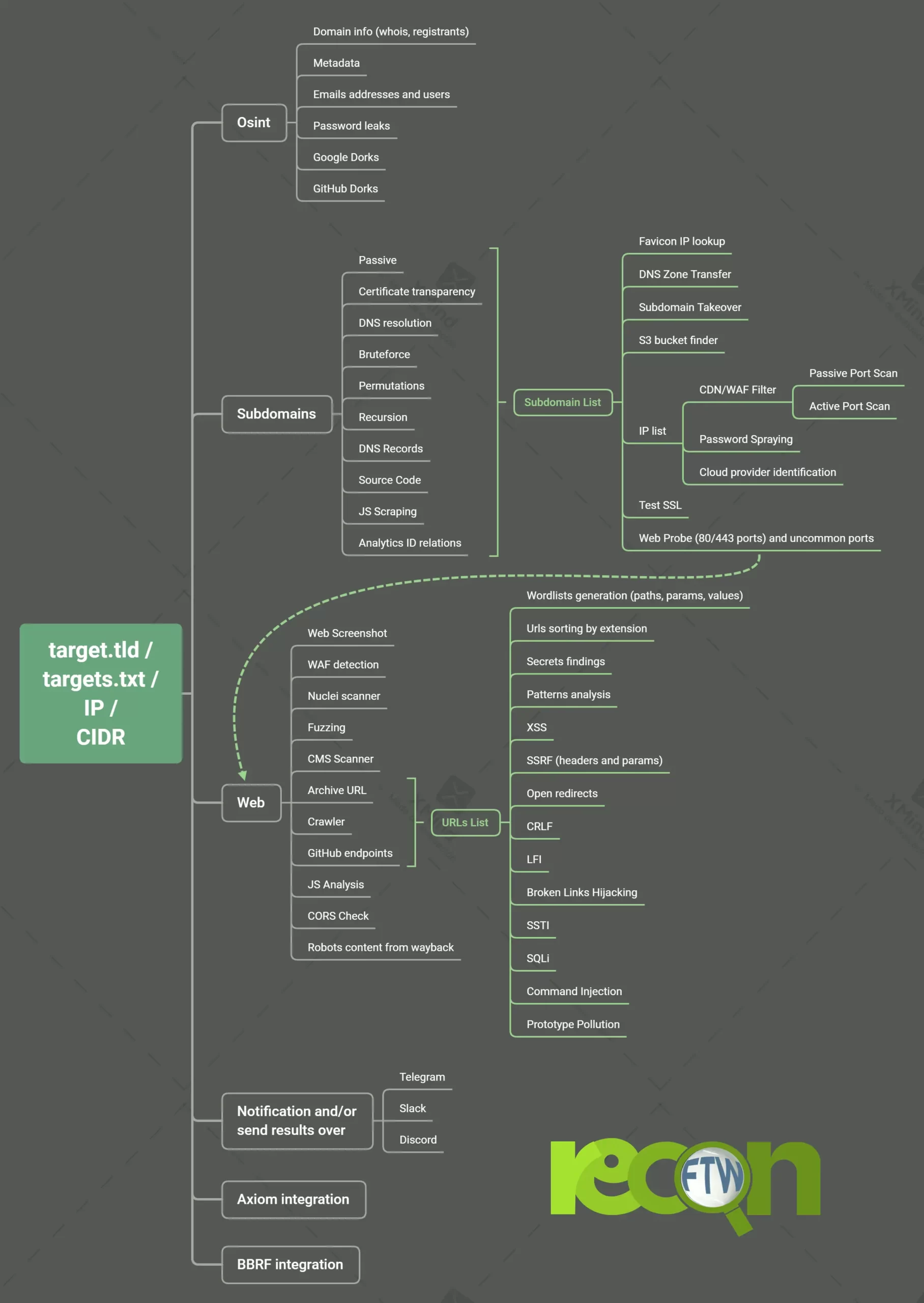
ReconFTW uses a lot of techniques (passive, bruteforce, permutations, certificate transparency, source code scraping, analytics, DNS records…) for subdomain enumeration which helps you to get the maximum and the most interesting subdomains so that you be ahead of the competition.
It also performs various vulnerability checks like XSS, Open Redirects, SSRF, CRLF, LFI, SQLi, SSL tests, SSTI, DNS zone transfers, and much more. Along with these, it performs OSINT techniques, directory fuzzing, dorking, ports scanning, screenshots, nuclei scan on your target.
Features
- Google Dorks (based on deggogle_hunter)
- Subdomain enumeration (passive, resolution, bruteforce and permutations)
- Sub TKO (subjack and nuclei)
- Web Prober (httpx)
- Web screenshot (aquatone)
- Template scanner (nuclei)
- Port Scanner (naabu)
- Url extraction (waybackurls, gau, hakrawler, github-endpoints)
- Pattern Search (gf and gf-patterns)
- Param discovery (paramspider and arjun)
- XSS (Gxss and dalfox)
- Github Check (git-hound)
- Favicon Real IP (fav-up)
- JS Checks (LinkFinder, SecretFinder, scripts from JSFScan)
- Fuzzing (ffuf)
- Cors (Corsy)
- SSL Check (testssl)
- Interlace integration
- Custom output folder (default under Recon/target.com/)
- Run standalone steps (subdomains, subtko, web, gdorks…)
- Polished installer compatible with most distros
Mindmap/Workflow
Requirements
- Requires Go
- Run ./install.sh before first run (apt, rpm, pacman compatible)
git clone https://github.com/six2dez/reconftw
cd reconftw
chmod +x *.sh
./install.sh
./reconftw.sh -d target.com -a
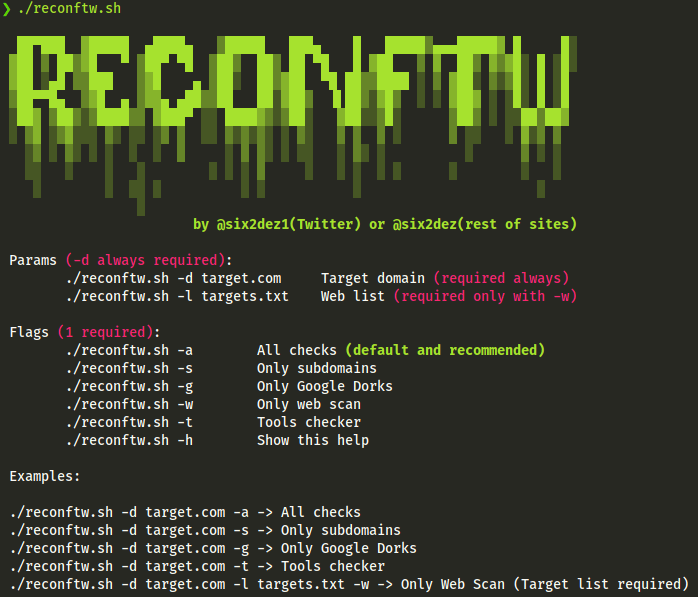
- Golang > 1.14 installed and env vars correctly set ($GOPATH,$GOROOT)
- Run ./install.sh
Installer is provided as is. Nobody knows your system better than you, so nobody can debug your system better than you. If you are experiencing some issues with the installer script I can help you out, but keep in mind that is not my main priority. - It is highly recommended, and in some cases essential, set your api keys:
amass (~/.config/amass/config.ini)
subfinder (~/.config/subfinder/config.yaml)
git-hound (~/.githound/config.yml)
github-endpoints.py (GITHUB_TOKEN env var)
favup (shodan init SHODANPAIDAPIKEY) - This script uses dalfox with blind-xss option, you must change to your own server, check xsshunter.com.
Usage examples
Full scan:
./reconftw.sh -d target.com -a
Subdomains scan:
./reconftw.sh -d target.com -s
Web scan (target list required):
./reconftw.sh -d target.com -l targets.txt -w
Dorks:
./reconftw.sh -d target.com -g
Improvement plan:
- Notification support (Slack, Discord and Telegram)
- CMS tools (wpscan, drupwn/droopescan, joomscan)
- Add menu option for every feature
- Any other interesting suggestion
- Open Redirect with Oralyzer
- Enhance this Readme
- Customize output folder
- Interlace usage
- Crawler
- SubDomainizer
- Install script
- Apt, rpm, pacman compatible installer
Also See – RecoX: Scripts For Web Application Reconnaissance