New services which present productivity improvements in cybersecurity are always good news. Spyse is a search engine, who have recently combined all their products into a single unit entirely overseeing the data gathering and reconnaissance process.
Tailored towards cybersecurity specialists, pentesters, and bug bounty hunters, Spyse gives a hand in quickly identifying network vulnerabilities and mitigating threats. They boast some smart features for illustrating relationships between collected data, and promise to automate all the tedious work security engineers have to do when working with bulks of data.
Topped off with one of the biggest databases on the web, Spyse promises new possibilities and improved workflows for anyone working in cybersecurity. Let’s take a closer look.
Spyse Constantly Collects Data
Lots of efforts have been made to put cybersecurity experts above hackers in the cybersecurity race. Spyse’s solution is: instead of having users perform regular scans, they pre-gather data to give users instant results. This hastens the process of creating protective measures and sealing off network vulnerabilities before they’re exposed.
Spyse have developed a unique scanning technique which implements over ten self-developed scanners, to create a process of uninterrupted data gathering. The scanners gather data from several resources to ensure authenticity by comparison. For example: when getting DNS records, the request is sent to 3 DNS servers at once to clarify the validity of the data.
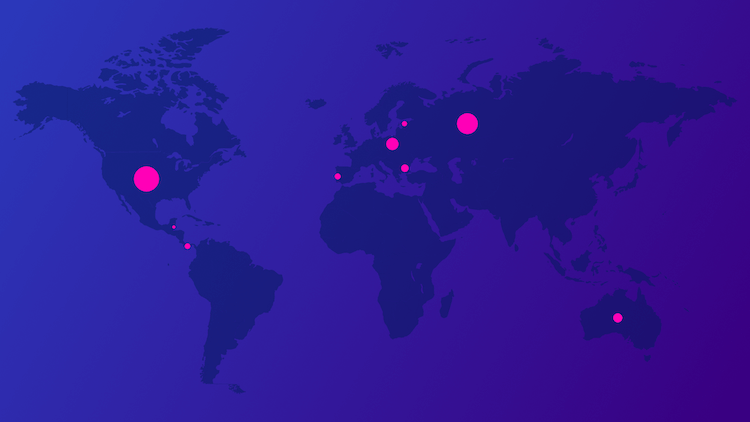
Spyse uses their global fifty-server distribution system to scan all around the world, bypassing location scanning restrictions and ISP blocking. With this system, Spyse can offer unique data which is hard to find elsewhere.
I’ll Take Database Over New Scans Any Day
A key feature of Spyse is its database, which removes the monotone work of doing manual scans and establishing relationships between data. Working with a database awards security specialists time to focus on sealing vulnerabilities and blocking security threats.
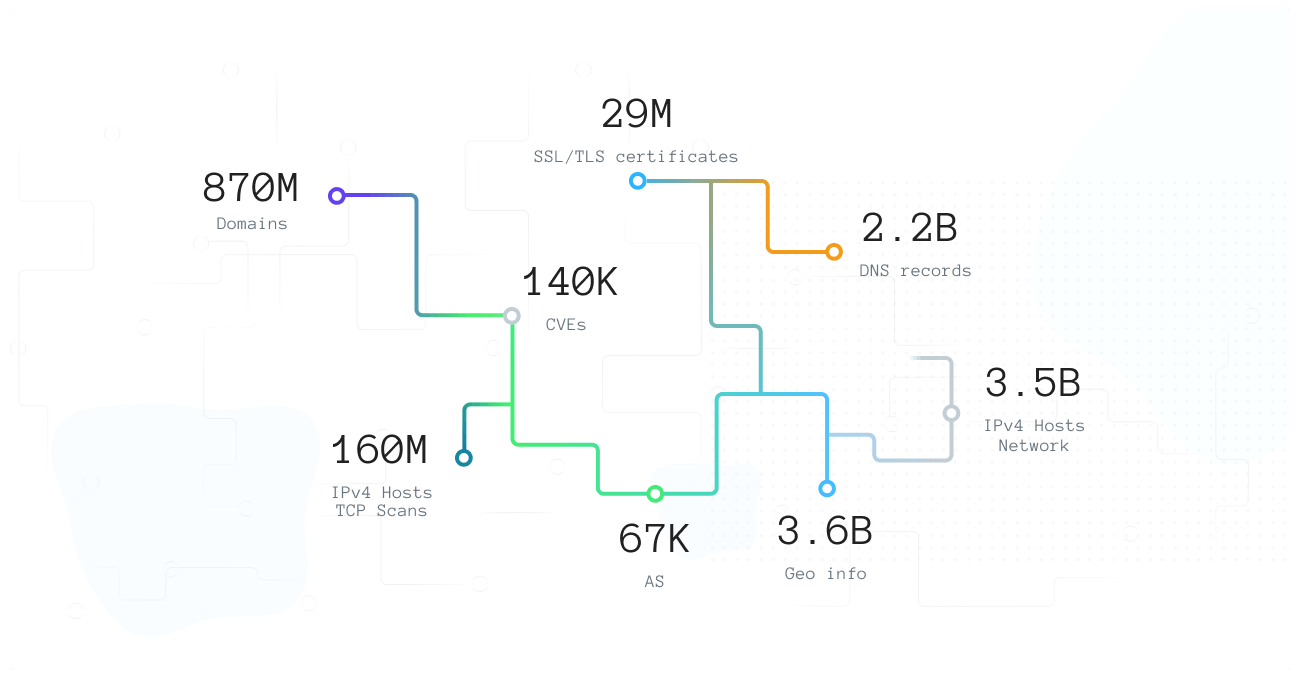
Spyse stores only hot data, employing fifty highly productive, fast, and expensive servers with about seven billion documents broken up into 250+ shards. This makes for five terabytes of instant access data. The data is stored so that it can be connected to help the user visualise a full picture of any target infrastructure.
With this kind of database available, a user can map infrastructures quickly, and track malicious behavior on their server. Well-trained, cybersecurity-aware employees using a service like this, will certainly be a force to be reckoned with.
Presentation of the Data
There are two ways that Spyse gives you data: through the web interface, and the API.
The web interface displays aggregated and structured information in a format which sees the data organized into tables. The information inside these tables can be edited to suit the user’s needs. After having found all the necessary data, users can download it for offline access.
Data can also be obtained using the API. With an expanded Swagger documentation, the API is extremely flexible in its application and can be freely integrated into any users’ tools or services. Every method for extracting information is shown in detail, which makes this API a pleasure to work with. The team has yet to reveal their CLI, but they do have a Python wrapper made by outsourced developer zer0pwn, which can also be a great alternative.
Additional Tools
A large portion of this service is tailored towards speeding up the workflow of cybersecurity personnel. Spyse scoring and advanced search are among the tools which help with searching for and filtering information for the most precise scans. Find out what your business partners are having for dinner.
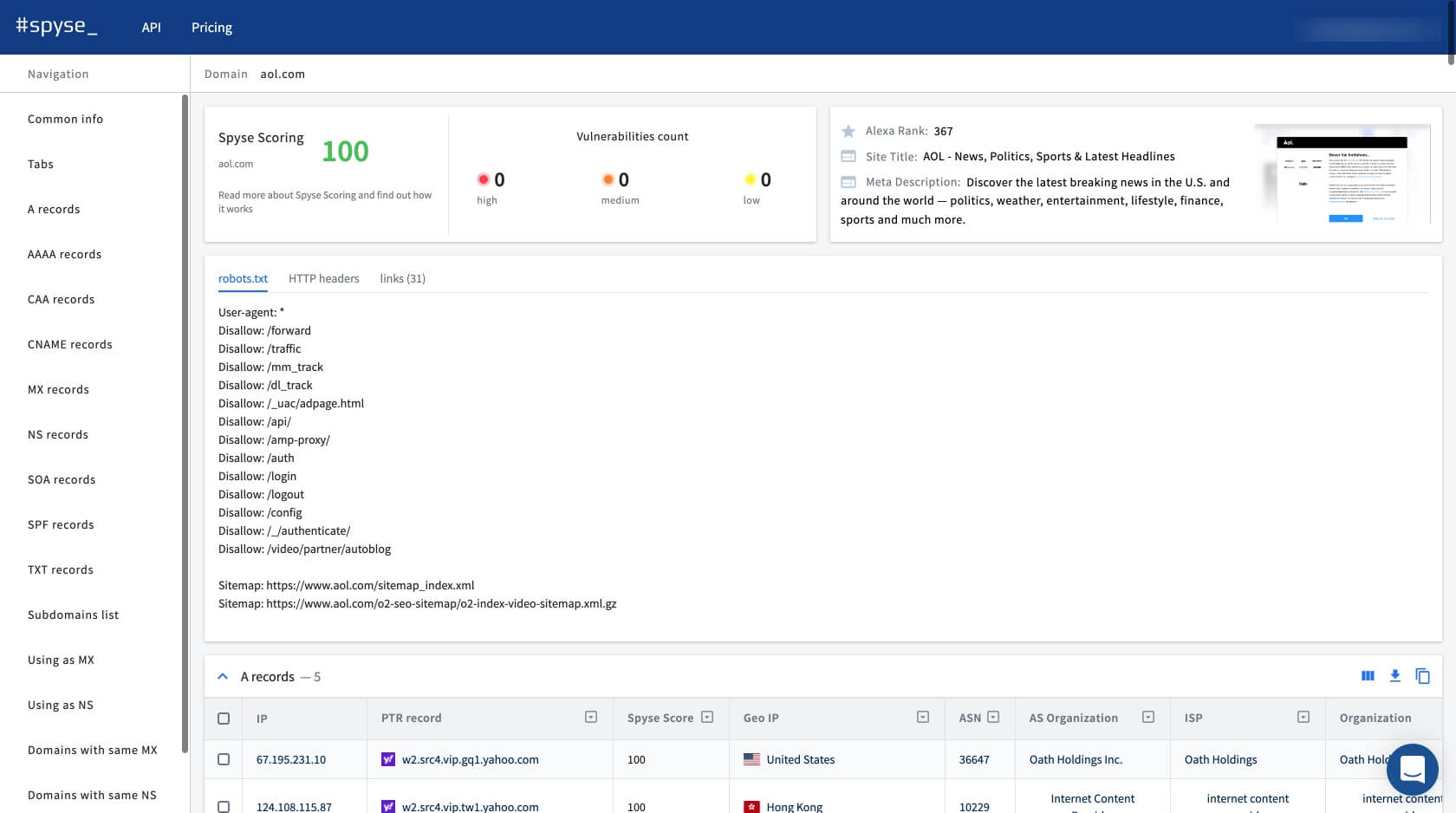
The Security Scoring quickly analyzes any given network for errors, bugs, loopholes, and anything which can be identified as a vulnerability. The network then receives an overall security score of 0-100, with the possibility to view expanded data on each found vulnerability. This is handy for performing quick and thorough network analyses to uncover gaps and identify weaknesses. A handy feature for bug bounty hunters who need to make a target list asap.
Advanced search, which dramatically accelerates the search process by enabling users to find concrete target information. It acts like a live filter which allows users to apply 5 search parameters to a query to narrow down data. For example: by using just 3 parameters, you can find all sites with domain response 200, what company they belong to, and what vulnerabilities that company has on their servers.
Who Can Use Spyse
Spyse enables system administrators to continuously monitor their cyber-infrastructure and attain information straight from the database. This can be done both manually and by writing a few simple scripts. Additionally, Spyse lets sysadmins quickly analyze levels of security in any infrastructure, finding weak points and potential points of entry swiftly.
This service is also of great benefit to pentesters and bug bounty hunters, as it completely oversees the process of finding target information and can help quickly create a target list. Spyse helps avoid most problems related to the information gathering process, like spending time and resources on developing new infrastructures for scanning, avoiding rate limits, and the necessity to stay invisible while finding information. Spyse is a great OSINT resource when others are forbidden to use by contract or bug bounty agreement.
Spyse fully oversees the process of reconnaissance, saving large amounts of time and resources used in investigation.