[UPDATE]
Wireless Internet Browser (WIB) SIM Kit Also Leads To SimJacker Attacks
Vulnerabilities in WIB Simcard-browsers can let attackers globally control the victim mobile phone, make a phone, Send SMS and send victim’s location.
According to Ginno Security Lab, the Wireless Internet Browser (WIB) is specified by SmartTrust and is oe of the market leading solution for SIM toolkit based browsing. The affection of the vulnerabilities at WIB spreads worldwide and causes serious harm to millions of telecom subscribers.
Ginno Security Lab, researched security in simcard and discovered the vulnerability in both WIB simcard-browser and S@T simcard-browser, that cause serious harm to hundreds of millions of telecom subscribers worldwide in 2015. Vulnerability in WIB has not ever been published yet.
By sending a malicious SMS to victim phone number, attacker can abuse the vulnerabilities in the WIB sim browser to remotely take control of the victim mobile phone to perform harmful actions such as: send sms, make phone call, get victim’s location, launch other browsers (e.g WAP browser), get victim’s IMEI, etc.
The affection of the vulnerability in WIB spreads worldwide and puts hundreds of millions of telecom subscribers worldwide at risk. The security vulnerability comes from sim card, depends neither on mobile phone devices nor on mobile phone Operating System, so every mobile phone is affected.
The security researchers found a critical vulnerability in SIM Cards.
It could allow cyber attackers to Espionage Mobile phone without victim knowledge, just by sending an SMS.
SimJacker can track phone location of Vulnerable Subscribers.
The SIMJACKER vulnerability found by AdaptiveMobile security researchers. The vulnerability is currently being actively exploited by a specific private company that works with governments to monitor individuals.
Over One Billion global phone users potentially exposed. All makes and models of the mobile phone may be open to attack. It could be potentially exploited to perform Denial of Service attack, Call Interception and Espionage.
How does it Work?
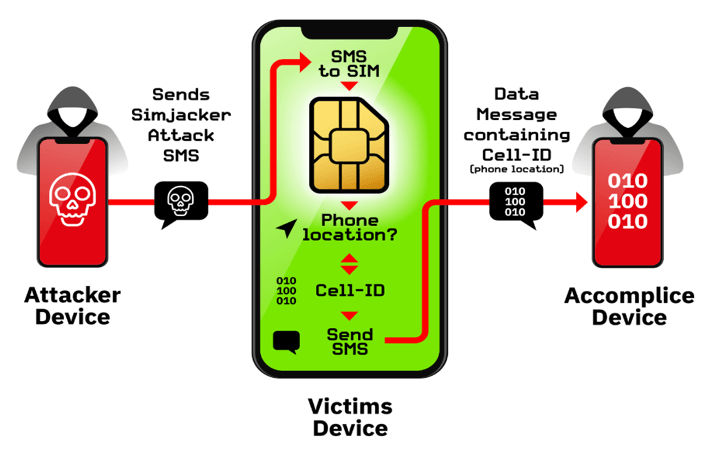
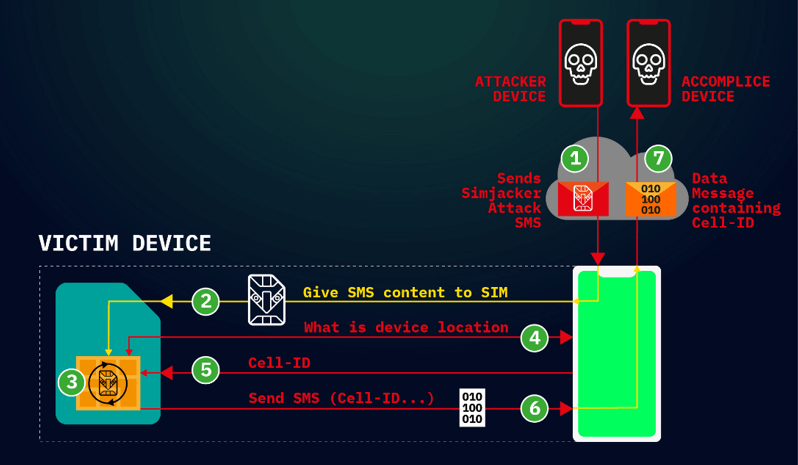
Simjacker attack involves an SMS containing a specific type of spyware-like code being sent to a mobile phone, which then instructs the UICC (SIM Card) within the phone to ‘take over’ the mobile phone, to retrieve and perform sensitive commands.
The location information of thousands of devices has obtained over time without the knowledge or consent of the targeted mobile phone users.
The attack begins when an SMS – that we term the Simjacker ‘Attack Message’ – is sent to the targeted handset. This Simjacker Attack Message, sent from another handset, a GSM Modem or an SMS sending account connected to an A2P account, contains a series of SIM Toolkit (STK) instructions and is specifically crafted to be passed on to the UICC/eUICC (SIM Card) within the device.
Also See- Android Ransomware Spreading Through SMS
For these instructions to work, the attack exploits the presence of a particular piece of software, called the S@T Browser – that is on the UICC. Once the UICC receives the Simjacker Attack Message, it uses the S@T Browser library as an execution environment on the UICC, where it can trigger logic on the handset.
For the main attack observed, the Simjacker code running on the UICC requests location and specific device information (the IMEI) from the handset.
Once this information is retrieved, the Simjacker code running on the UICC then collates it and sends the combined information to a recipient number via another SMS (we call this the ‘Data Message’), again by triggering logic on the handset. This Data Message is the method by which the location and IMEI information could exfiltrated to a remote phone controlled by the attacker.
The Simjacker vulnerability could extend to over 1 billion mobile phone users globally, potentially impacting countries in the Americas, West Africa, Europe, Middle East and indeed any region of the world where this SIM card technology is in use.
The researchers said they had observed real-attacks against users with devices from nearly every manufacturer, including Apple, ZTE, Motorola, Samsung, Google, Huawei, and even IoT devices with SIM cards.
“Simjacker represents a clear danger to the mobile operators and subscribers. This is potentially the most sophisticated attack ever seen over core mobile networks,” said Cathal McDaid, CTO, AdaptiveMobile Security in a press release.
“It’s a major wake-up call that shows hostile actors are investing heavily in increasingly complex and creative ways to undermine network security. This compromises the security and trust of customers, mobile operators, and impacts the national security of entire countries.”