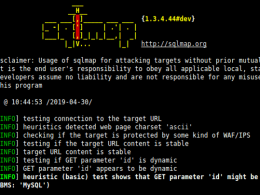
The OWASP Mobile Top 10 provides a roadmap for developers and security professionals to identify and mitigate the most critical risks facing applications. As a developer or security enthusiast, understanding these vulnerabilities is crucial for building secure mobile applications.
Let’s delve into the latest OWASP Mobile (as of 2023) and equip you with the knowledge to safeguard your mobile apps. In this comprehensive tutorial, we’ll explore each of the OWASP Mobile Top 10 risks in detail:
1. Improper Credential Usage (M1)
- Description: This risk involves mishandling of credentials, leading to unauthorized access.
- Mitigation: Implement secure credential storage, avoid hardcoding secrets, and use proper authentication mechanisms.
2. Inadequate Supply Chain Security (M2)
- Description: Supply chain attacks can compromise your app through third-party components.
- Mitigation: Vet third-party libraries, monitor dependencies, and ensure secure supply chain practices.
3. Insecure Authentication/Authorization (M3)
- Description: Weak authentication and authorization mechanisms expose sensitive functionality.
- Mitigation: Implement strong authentication, proper session management, and role-based access controls.
4. Insufficient Input/Output Validation (M4)
- Description: Lack of input validation can lead to injection attacks.
- Mitigation: Validate user inputs, sanitize data, and prevent injection vulnerabilities.
5. Insecure Communication (M5)
- Description: Weak encryption or improper handling of sensitive data during transmission.
- Mitigation: Use secure communication protocols (e.g., HTTPS), avoid hardcoding secrets, and protect data in transit.
6. Inadequate Privacy Controls (M6)
- Description: Privacy violations due to improper handling of user data.
- Mitigation: Obtain user consent, minimize data collection, and follow privacy regulations.
7. Insufficient Binary Protections (M7)
- Description: Lack of protections against reverse engineering and tampering.
- Mitigation: Apply code obfuscation, integrity checks, and anti-tampering techniques.
8. Security Misconfiguration (M8)
- Description: Misconfigured settings can expose sensitive information.
- Mitigation: Regularly audit configurations, follow security guidelines, and minimize attack surfaces.
9. Insecure Data Storage (M9)
- Description: Storing sensitive data insecurely (e.g., plaintext, weak encryption).
- Mitigation: Encrypt data at rest, use secure storage APIs, and avoid storing sensitive data unnecessarily.
10. Insufficient Cryptography (M10)
- Description: Weak cryptographic practices can lead to data exposure.
- Mitigation: Use strong encryption algorithms, manage keys securely, and follow best practices.
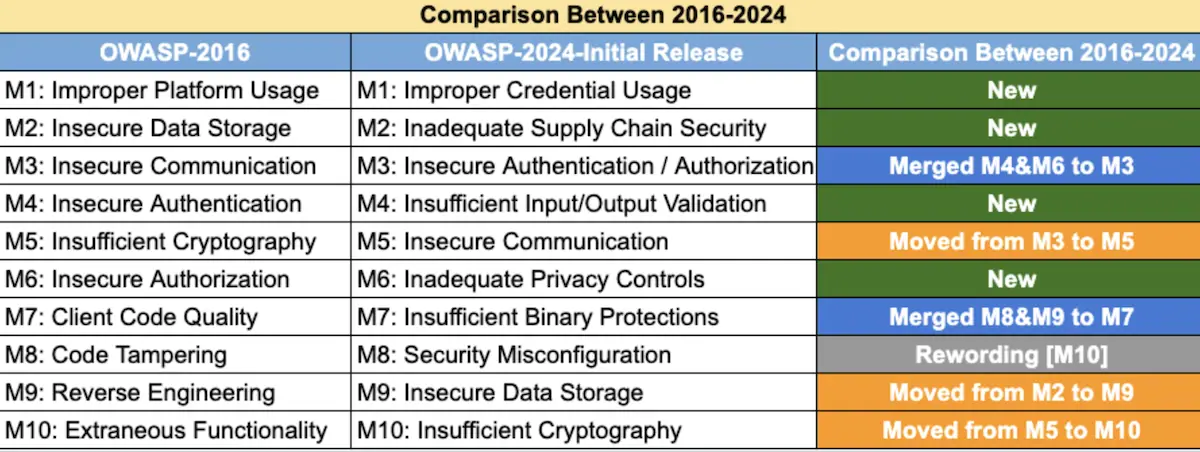
Remember that mobile security is an ongoing process. Regularly assess your app for these vulnerabilities, stay informed about security updates, and adopt secure coding practices.
Also See: OWASP Top 10 Web Lists