This list highlights the most critical security risks faced by web applications. As a developer or security enthusiast, understanding these risks is essential for secure software development.
Here’s a comprehensive tutorial on each of the OWASP Top 10 Web List vulnerabilities:
OWASP Top 10:2021
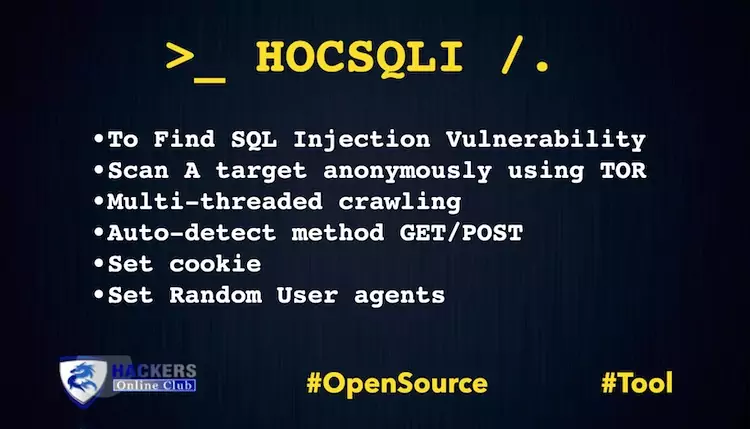
Also See: OWASP IoTGoat - To Find IoT Vulnerabilities
1. Broken Access Control (A01:2021)
- Description: This risk involves inadequate access controls that allow unauthorized users to access restricted functionality or data.
- Root Cause: Poorly implemented authorization mechanisms.
- Impact: Unauthorized access, data leaks, privilege escalation.
- Mitigation: Implement proper access controls, validate user permissions, and avoid direct object references.
2. Cryptographic Failures (A02:2021)
- Description: This category focuses on cryptographic weaknesses leading to sensitive data exposure.
- Root Cause: Flaws in encryption, key management, or random number generation.
- Impact: Data leaks, system compromise.
- Mitigation: Use strong encryption algorithms, manage keys securely, and follow best practices.
3. Injection (A03:2021)
- Description: Injection flaws occur when untrusted data is executed as code.
- Root Cause: Lack of input validation and escaping.
- Impact: Data manipulation, code execution.
- Mitigation: Sanitize inputs, use prepared statements, and avoid dynamic queries.
4. Insecure Design (A04:2021)
- Description: This new category emphasizes design flaws that undermine security.
- Root Cause: Poor threat modeling, lack of secure design patterns.
- Impact: Irremediable security issues.
- Mitigation: Prioritize threat modeling, adopt secure design principles, and follow reference architectures.
5. Security Misconfiguration (A05:2021)
- Description: Misconfigurations occur due to improper settings in software components.
- Root Cause: Neglected configurations, default credentials, unnecessary services.
- Impact: Unauthorized access, data exposure.
- Mitigation: Regularly audit configurations, follow security guidelines, and minimize attack surfaces.
6. Vulnerable and Outdated Components (A06:2021)
- Description: Using outdated or vulnerable components poses significant risks.
- Root Cause: Ignoring component security updates.
- Impact: Exploitable vulnerabilities.
- Mitigation: Keep components up-to-date, monitor for vulnerabilities, and use secure libraries.
7. Identification and Authentication Failures (A07:2021)
- Description: Weak authentication mechanisms lead to unauthorized access.
- Root Cause: Insufficient authentication, weak passwords, session management flaws.
- Impact: Account compromise, data breaches.
- Mitigation: Implement strong authentication, enforce password policies, and manage sessions securely.
8. Software and Data Integrity Failures (A08:2021)
- Description: This category covers integrity issues in software and data.
- Root Cause: Lack of integrity checks, tampering.
- Impact: Data corruption, system compromise.
- Mitigation: Validate data integrity, use checksums, and protect against tampering.
9. Security Logging and Monitoring Failures (A09:2021)
- Description: Inadequate logging and monitoring hinder threat detection.
- Root Cause: Insufficient logging, lack of monitoring.
- Impact: Delayed incident response, undetected attacks.
- Mitigation: Implement robust logging, monitor critical events, and set up alerts.
10. Server-Side Request Forgery (SSRF) (A10:2021)
- Description: SSRF occurs when an attacker manipulates server requests.
- Root Cause: Lack of input validation in server-side requests.
- Impact: Data exposure, internal network access.
- Mitigation: Validate input, restrict allowed URLs, and use whitelists.
Remember to stay informed about security best practices, keep your software updated, and follow secure coding guidelines. The OWASP Top 10 serves as a roadmap for building resilient applications. Happy coding!
Source: OWASP