NetworkMiner, it is an open source Network Forensic Analysis Software (NFAT) for Windows (yet additionally works in Linux/Mac OS X/FreeBSD).
NetworkMiner can be utilized as a detached organization sniffer/bundle catching apparatus so as to recognize working frameworks, meetings, hostnames, open ports and so forth without putting any traffic on the organization. It can likewise parse PCAP records for disconnected examination and to recover/reassemble communicated documents and declarations from PCAP records.
It is simple to perform progressed Network Traffic Analysis (NTA) by giving removed relics in a natural UI. The way data are presented not only makes the analysis simpler, it also saves valuable time for the analyst or forensic investigator.
It can extract files, emails and certificates transferred over the network by parsing a PCAP file or by sniffing traffic directly from the network.
Requirements
- NetworkMiner – Download here
- PCAP file from Wireshark
- Windows OS
NetworkMiner Tutorial
FIRST Step to Download and install NetworkMiner in Windows to run it.
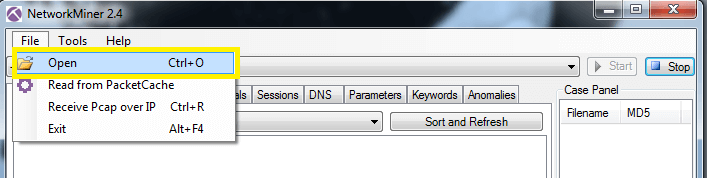
then Go to File > open > select .pcap file
Step 2: After load successfully.
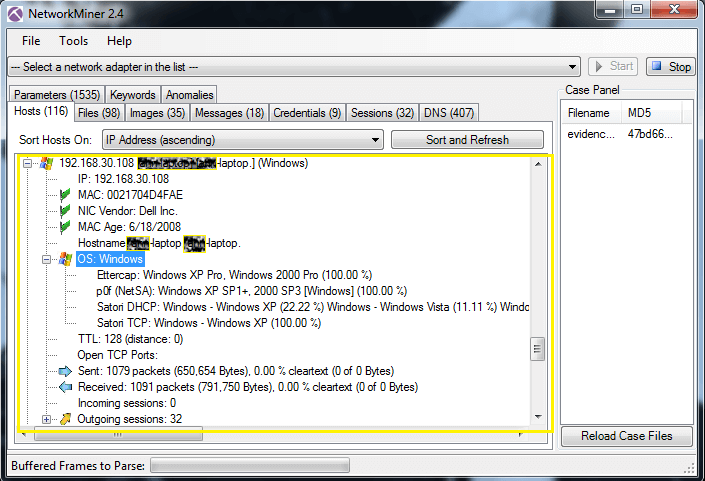
PCAP file want to see the host name, Mac, OS, etc. click on host tab and analysis the data
NetworkMiner showing extracted username
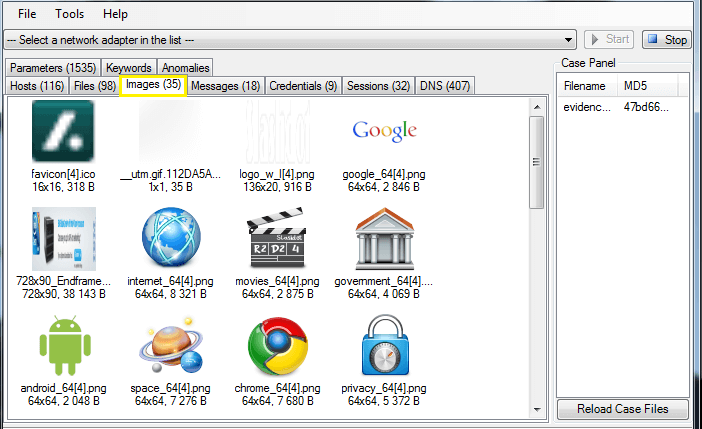
Step for analysis the images over network >image tab
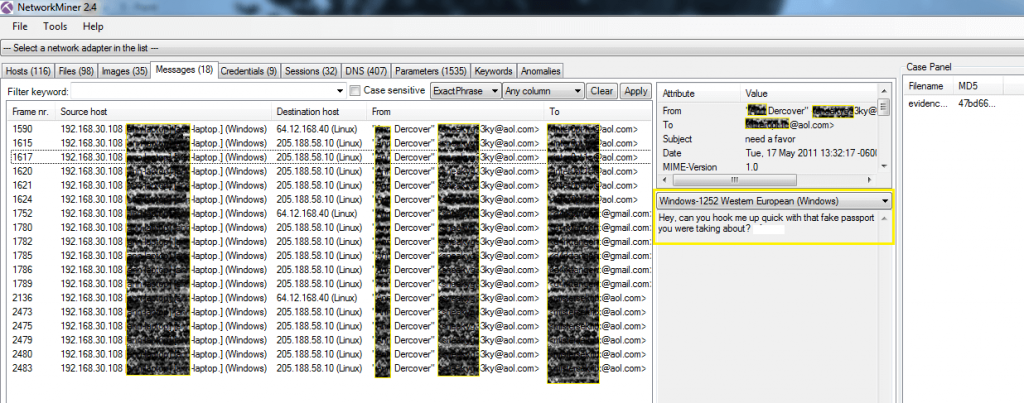
Step for analysis the communication /messages over network > Messages tab
Step for analysis the files over network>Files tab
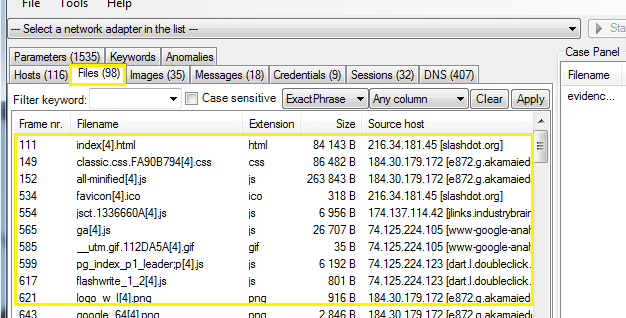
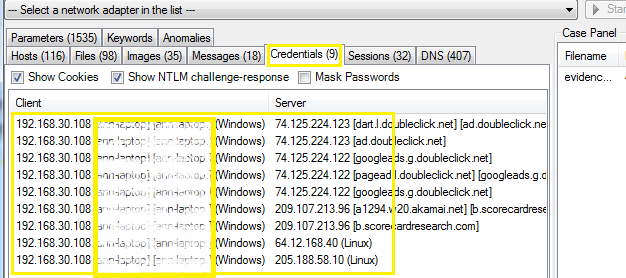
Step for analysis the credentials over network >Credentials tab
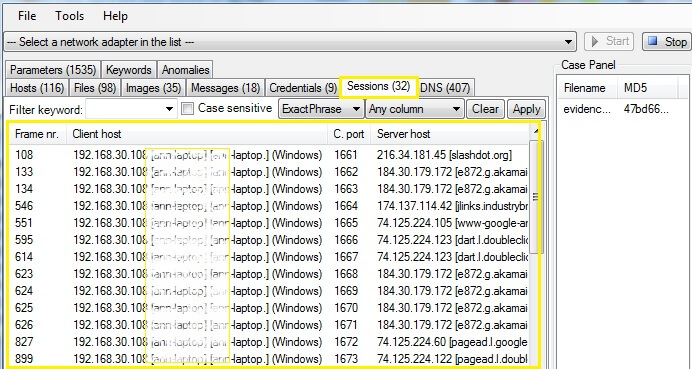
Step for analysis the sessions over network > Sessions
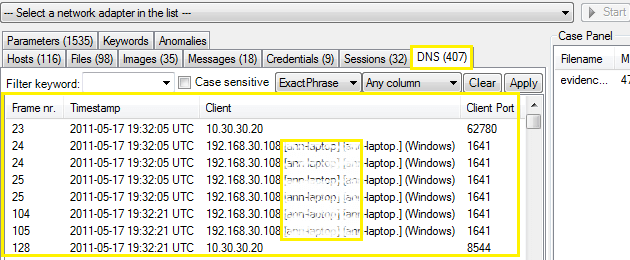
Step for analysis the DNS over network > DNS tab
Hope you will get to know how to use NetworkMiner and analysis the PCAP logs.