Microsoft ICS Forensics framework is an open source forensic framework for analyzing Industrial PLC metadata and project files.
It enables investigators to identify suspicious artifacts on Industrial Control Systems (ICS) environment for detection of compromised devices during incident response or manual check. Open source framework, which allows investigators to verify the actions of the tool or customize it to specific needs.
Getting Started
These instructions will get you a copy of the project up and running on your local machine for development and testing purposes.
git clone https://github.com/microsoft/ics-forensics-tools.gitPrerequisites
Install Python >= 3.9: https://www.python.org/downloadsInstalling
Install python requirements
pip install -r requirements.txtUsage
General application arguments:
| Args | Description | Required / Optional |
|---|---|---|
-h, --help | show this help message and exit | Optional |
-s, --save-config | Save config file for easy future usage | Optional |
-c, --config | Config file path, default is config.json | Optional |
-o, --output-dir | Directory in which to output any generated files, default is output | Optional |
-v, --verbose | Log output to a file as well as the console | Optional |
-p, --multiprocess | Run in multiprocess mode by number of plugins/analyzers | Optional |
Specific plugin arguments:
| Args | Description | Required / Optional |
|---|---|---|
-h, --help | show this help message and exit | Optional |
--ip | Addresses file path, CIDR or IP addresses csv (ip column required). add more columns for additional info about each ip (username, pass, etc…) | Required |
--port | Port number | Optional |
--transport | tcp/udp | Optional |
--analyzer | Analyzer name to run | Optional |
Also See :
Executing
Executing examples in the command line
python driver.py -s -v PluginName --ip ips.csv
python driver.py -s -v PluginName --analyzer AnalyzerName
python driver.py -s -v -c config.json --multiprocessImport as library example
from forensic.client.forensic_client import ForensicClient
from forensic.interfaces.plugin import PluginConfig
forensic = ForensicClient()
plugin = PluginConfig.from_json({
"name": "PluginName",
"port": 123,
"transport": "tcp",
"addresses": [{"ip": "192.168.1.0/24"}, {"ip": "10.10.10.10"}],
"parameters": {
},
"analyzers": []
})
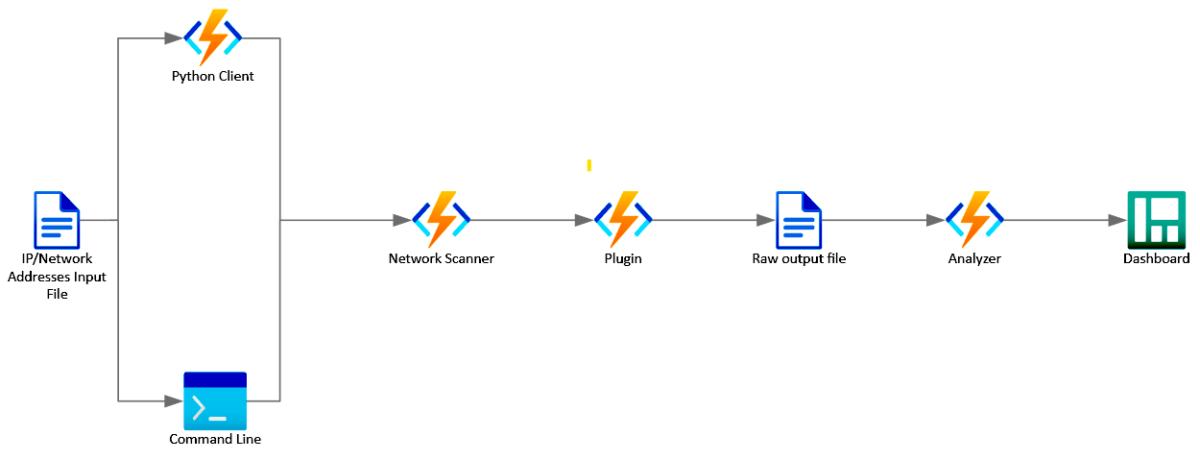
forensic.scan([plugin])Architecture
Adding Plugins
When developing locally make sure to mark src folder as “Sources root”
- Create new directory under plugins folder with your plugin name
- Create new Python file with your plugin name
- Use the following template to write your plugin and replace ‘General’ with your plugin name
from pathlib import Path
from forensic.interfaces.plugin import PluginInterface, PluginConfig, PluginCLI
from forensic.common.constants.constants import Transport
class GeneralCLI(PluginCLI):
def init(self, folder_name):
super().init(folder_name)
self.name = "General"
self.description = "General Plugin Description"
self.port = 123
self.transport = Transport.TCPdef flags(self, parser):
self.base_flags(parser, self.port, self.transport)
parser.add_argument('--general', help='General additional argument', metavar="")class General(PluginInterface):
def init(self, config: PluginConfig, output_dir: Path, verbose: bool):
super().init(config, output_dir, verbose)def connect(self, address):
self.logger.info(f"{self.config.name} connect")
def export(self, extracted):
self.logger.info(f"{self.config.name} export")- Make sure to import your new plugin in the init.py file under the plugins folder
- In the PluginInterface inherited class there is ‘config’ parameters, you can use this to access any data that’s available in the PluginConfig object (plugin name, addresses, port, transport, parameters).
there are 2 mandatory functions (connect, export).
the connect function receives single ip address and extracts any relevant information from the device and return it.
the export function receives the information that was extracted from all the devices and there you can export it to file. - In the PluginCLI inherited class you need to specify in the init function the default information related to this plugin.
there is a single mandatory function (flags). - In which you must call base_flags, and you can add any additional flags that you want to have.
Adding Analyzers
- Create new directory under analyzers folder with the plugin name that related to your analyzer.
- Create new Python file with your analyzer name
- Use the following template to write your plugin and replace ‘General’ with your plugin name
from pathlib import Path
from forensic.interfaces.analyzer import AnalyzerInterface, AnalyzerConfig
class General(AnalyzerInterface):
def init(self, config: AnalyzerConfig, output_dir: Path, verbose: bool):
super().init(config, output_dir, verbose)
self.plugin_name = 'General'
self.create_output_dir(self.plugin_name)def analyze(self):
passMake sure to import your new analyzer in the init.py file under the analyzers folder
Resources and Technical data & solution:
Microsoft Defender for IoT is an agentless network-layer security solution that allows organizations to continuously monitor and discover assets, detect threats, and manage vulnerabilities in their IoT/OT and Industrial Control Systems (ICS) devices, on-premises and in Azure-connected environments.
Download Microsoft ICS Forensics Framework