GDA (GJoy Dex Analyzer) – Android Reverse Engineering Suite
- Android Malware Static Analysis
- File loading and decompiling
- Variable Trace
- XML decoder
Fully self-implemented decoding function can bypass the Anti-decoding technology, successfully parse XML.
GDA, a new Dalvik bytecode decompiler, is implemented in C++, which has the advantages of faster analysis and lower memory and disk consumption and an stronger ability to decompiling the APK, DEX, ODEX, OAT files(supports JAR, CLASS and AAR files since 3.79).
GDA is completely self-independent and works without Java VM and installation, so it works well in any newly installed windows system and virtual machine system without additional configuration.
GDA is also a powerful and fast reverse analysis platform. Which does not only supports the basic decompiling operation, but also many excellent functions like Malicious behavior detection, Privacy leaking detection, Vulnerability detection, Path solving, Packer identification, Variable tracking analysis, Deobfuscation, Python& Java scripts, Device memory extraction, Data decryption and encryption etc.
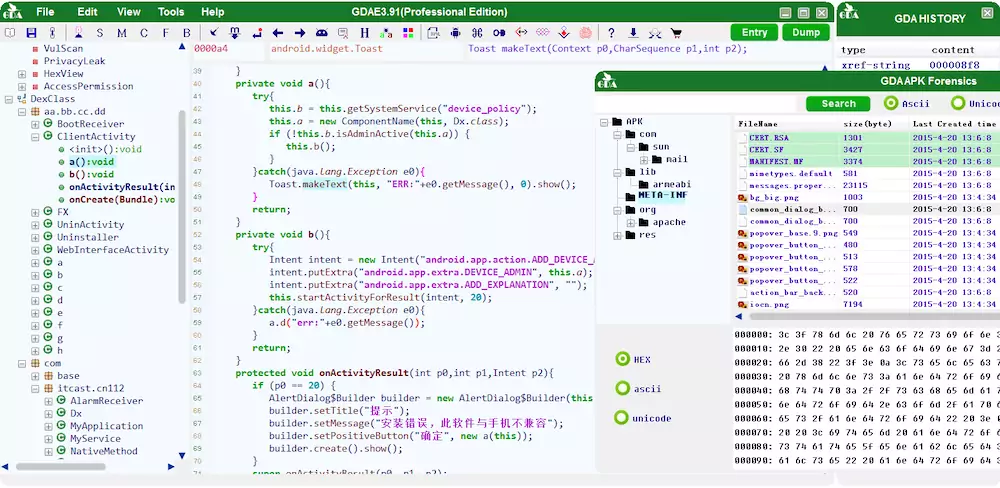
In addition, GDA has more excellent features as follows:
Interactive operation:
1. Cross-references for strings, classes, methods and fields
2. Searching for strings, classes methods and fields
3. Comments for java code
4. Rename for methods, fields and classes
5. Save the analysis results in gda db file
Utilities for Assisted Analysis:
- Extracting DEX from ODEX;
- Extracting DEX from OAT;
- XML Decoder (Component filter);
- Algorithm tool(Support rolling encryption and almost all popular encryption algorithms);
- Device memory dump(Dump so, odex, dex, oat file);
- Path solving;
- Static vulnerability scanner;
New features:
1. Brand new dalvik decompiler in c++ with friendly GUI;
2. Support python script and Java script;
3. Packers Recognition;
4. Multi-DEX supporting;
5. Making and loading signature of the method;
6. Malicious Behavior Scanning by API chains;
7. Taint analysis to preview the behavior of variables;
8. Taint analysis to source the variables;
9. De-obfuscate;
10. API view with x-ref;
11. Association of permissions with modules;
12. Extract all the urls in APK.
13. Apk Forensics Analysis.
14. Static vulnerability scanner based on stack state machine and dynamic rule interpreter..
15. Smart Rename.
16. Support for .jar files, .class files and .aar files.
17. Dual decompiler mode.
18. Deep URL extraction.
19. Multi-DEX Merge.
20. Personalized and Customizable UI.
21. Privacy leaking scanning.
22. Path solving based on low-level intermediate representation(LIR).
23. Support Frida to hook and call the selected method or class.
24. Support call-graph view.
GDA shortcut key
- F5 Switch java to smali, pressing it again for back to java
- F Trace the args and return value by dataflow analysis
- X Cross-referencing, locating callers (of strings, classes, methods, field, Smali, Java)
- Esc/<-/Backspace Back to the last visit
- -> Forward to the next visit
- G Jump to somewhere by you inputting offset
- N Rename the variable/method/class name
- S Search for all the elements by the given string
- C Comments. Only supports the Java code
- DoubleClick The cursor’s placed at the method/str/field/class, and double-click to access objects
- M the cursor’s placed at the Smali line and pressing the key ‘M’ to edit the instruction
- UP Press ‘up’ key to access the up-method in the tree control
- Down Press “down” key to access the down-method in the tree control
- D Dump the binary data of methods, only supports the Smali window
- Enter The modification of edit boxes take effect
- H Show data in Hex
- Ctr+H Pop searching history window
- Ctr+A Select all
- Ctr+C Copy
- Ctr+V Paste, only for editable boxes
- Ctr+X Cut
- Ctr+F Find out the string of the current window
- Ctr+S Save the modifications into the GDA database file
Installing
Not yet, just double-click the bin and you can enjoy it form GDA – Android Reverse Engineering Suite.
MAIN WINDOWS
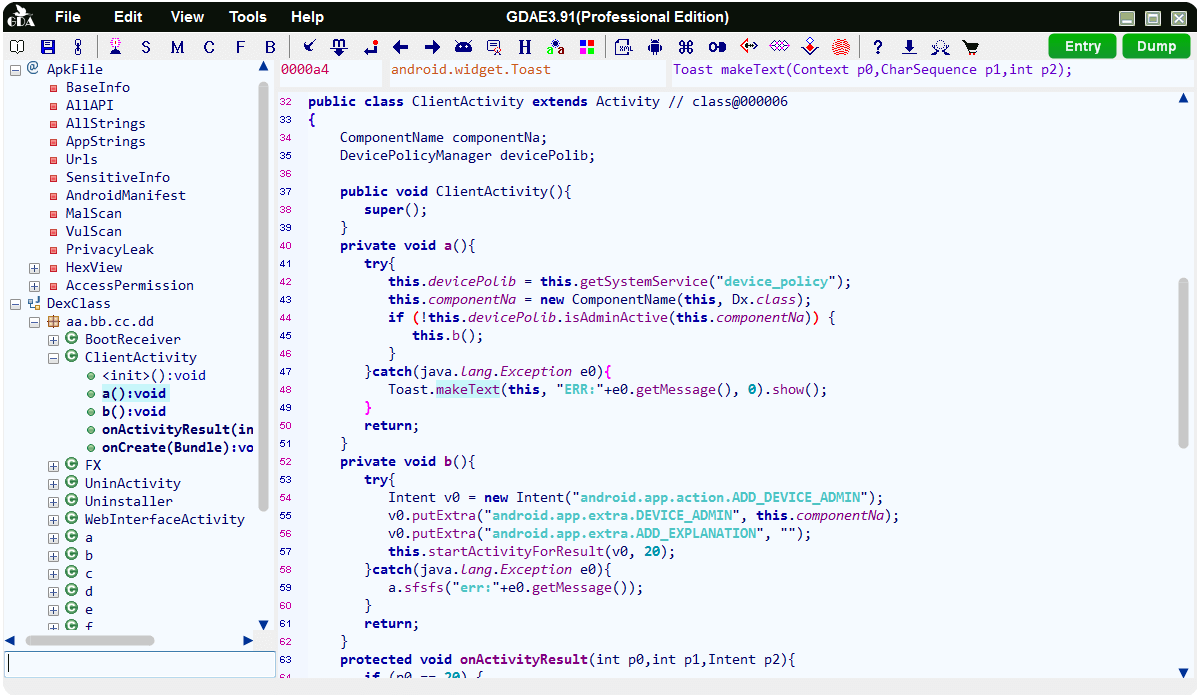
Open GDA and drag the APK file you want to analyze to the software UI:
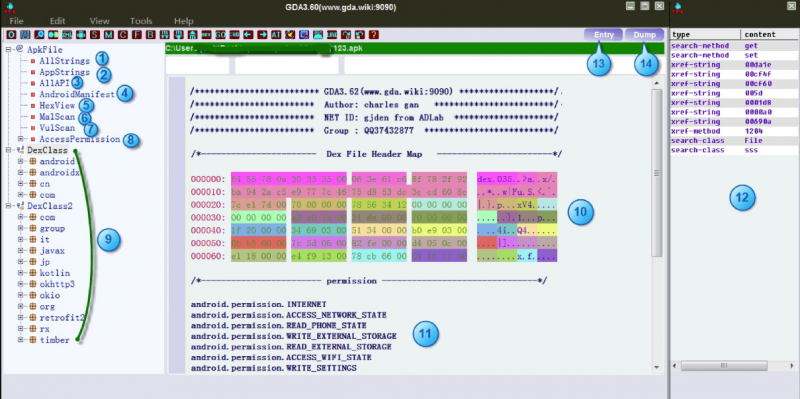
1. View all strings in DEX.
2. View all the strings used by all the methods.
3. View all APIs used by methods.
4. View AndroidManifest files.
5. Show data by Hexadecimal way.
6. Suspicious (malicious behavior analysis).
7. Vulnerability static scanning (to be implemented).
8. Expanding permissions and viewing the method which the permissions belong to.
9. Classes and methods, if there are more DexClass*, indicating that APK uses multi-dex.
10, DEX head, click on “DexClass*” item to display the corresponding head, each color block represents a different area of the head. the prompt will be shown when the mouse moves over on it. right-clicking in the area that is offset and jump to reference location.
11. Overview of the permissions applied by the application.
12. Double-click to view historical access.
13. Click to enter the entry function (method).
14. Connect the Android device for the memory dump.
If the APP is packed, GDA will automatically recognize and show the packer between the Dex header and the APK permission. Otherwise, nothing. As shown in the figure:
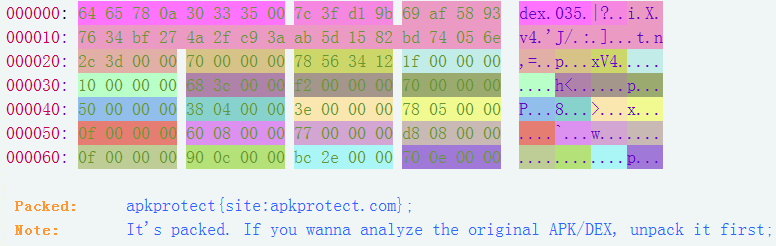
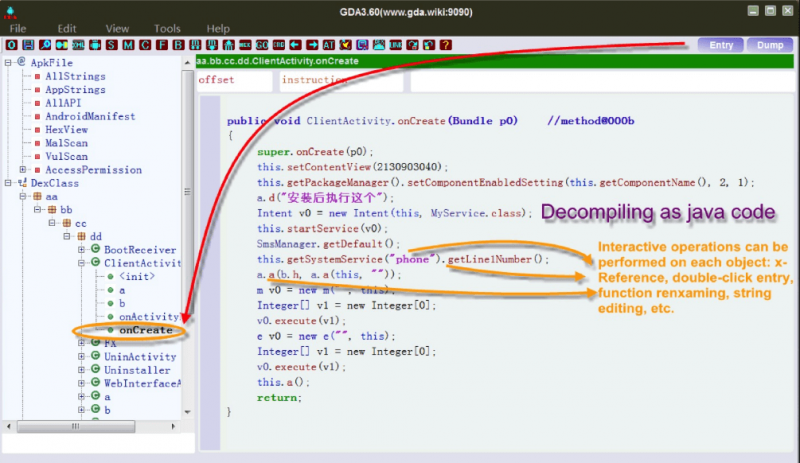
The DEX Header is just for fun, you can see the tip that shows the field of the header by moving the cursor over. Click the right mouse button and you can enter the subheader or offset table. Then, click the Entry button on the right-top to enter the APK entry function (usually onCreate of the main Activity):
Supported platforms
GDA Android Reverse Engineering suite is for windows.
Usage:
Drag file into GDA, if you wanna analyze .jar/.class/.aar file, please convert the jar/class/aar to DEX by dx tool in android sdk path android-sdk/build-tools/{sdkversion}/
dx --dex --output=<target.dex> <origin.jar>
Example of Android Malware Static Analysis – Click here
Download GDA (GJoy Dex Analyzer)