Today, we are going to demonstrate to bypass Captcha of a web application.
So, let’s start. You can also check the POC Video at the end of the article.
What is Captcha?
A CAPTCHA is a type of challenge-response test used in computing to determine whether the user is human or not.
Why is captcha used?
- To protect our website from bot, CSRF, etc.
- Protecting CSRF with Captcha is not recommended, captcha can be bypassed easily, no matter how hard it is.
Requirements
- Burpsuite for temper the request.
- Web For Pentester II for testing.
Let’s have a look, how a cyber-attacker can Bypass Captcha. For testing, I have used Web For Pentester II . It’s a vulnerable web application for penetration testing. When attacking Captcha, and before starting some hardcore coding, make sure there is no logic flaws or some predictability.
What is Web For Pentester II?
Web For Pentester II exercise is a set of the most common web vulnerabilities like
SQL injections,Authentication, Captcha, Authorization, Mass Assignment, Randoms issues, Mango DB injection.
The First step is to go to the website pentesterlab.com for download and run Web For Pentester II.
pentesterlab > exercise > category: free > Web For Pentester II > File >ISO
Download from pentesterlab.com
After download create new virtual machine
virtual machine > file > new virtual machine > typical> locate the ISO file (Web For Pentester II ) > next > finish
Now start Virtual Machine Web For Pentester II
Type ifconfig for IP address note down the IP address
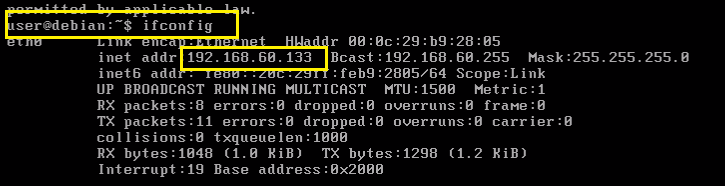
Type the IP address in your browser which you get from Web For Pentester II and hit enter.
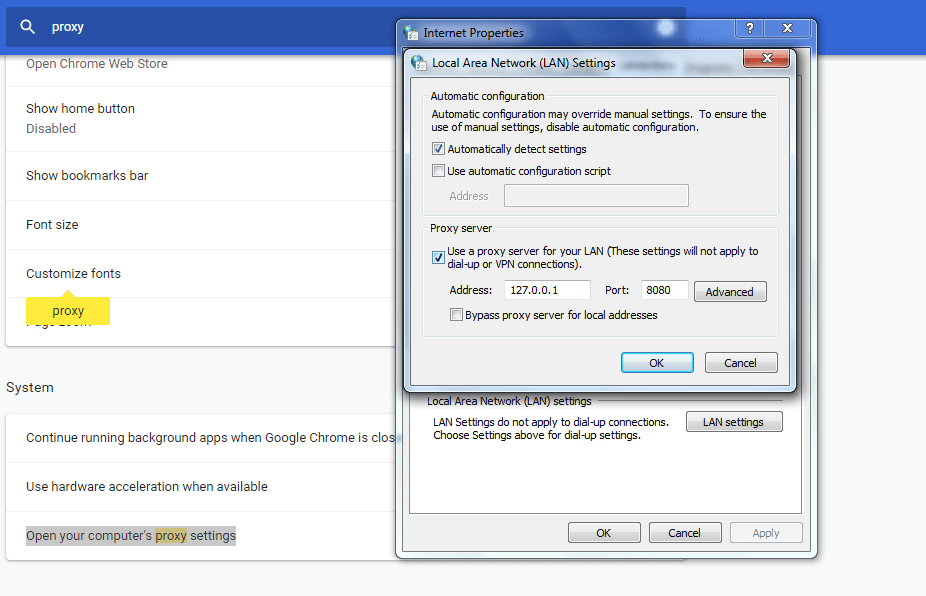
Now next step is to configure Burpsuite
Go to Browser settings and in the search box type proxy then select open proxy settings > In connection tabs > Lan settings > Tick Use a proxy server for your LAN > (127.0.0.1 port number 8080) then Click ok.
Now open Burp Suite.
In the Burp Proxy tab, ensure “Intercept is off” and visit the Captcha Example 1.
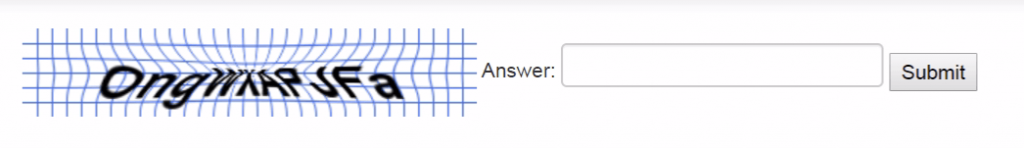
Example 1 This script is a common issue with badly implemented captcha. To avoid the error message, the developer checks that a captcha parameter exists before ensuring that its value is correct.
Turn on Intercept and then enter the random character in field box and see the interruption.
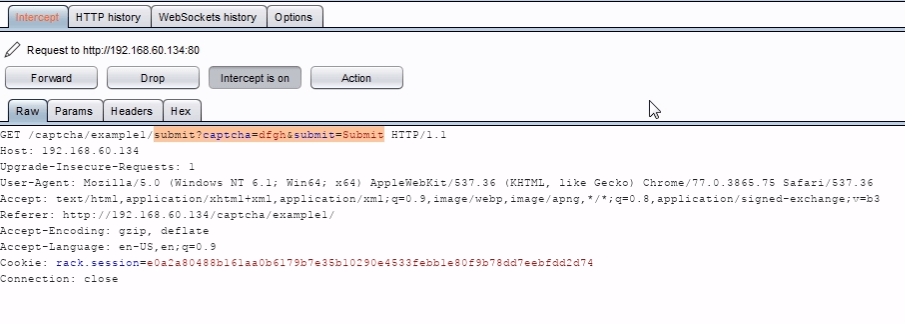
Now just delete the captcha=…& and forward the request, you will get a success feedback from the server.
URL: http://192.168.60.134/captcha/example1/submit?submit=Submit

Example 2 In this example, the answer is leaked by the application. By inspecting the source of HTML page returned, you should be able to write a script that can automatically break this captcha.
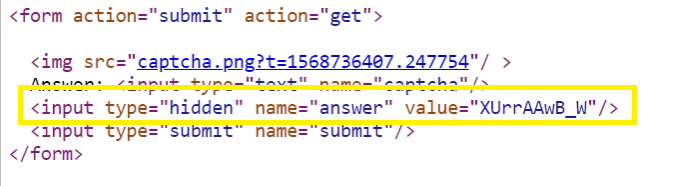
Or just delete the captcha=…&answer=…& you will get a success feedback from the server.
http://192.168.60.134/captcha/example2/submit?submit=Submit
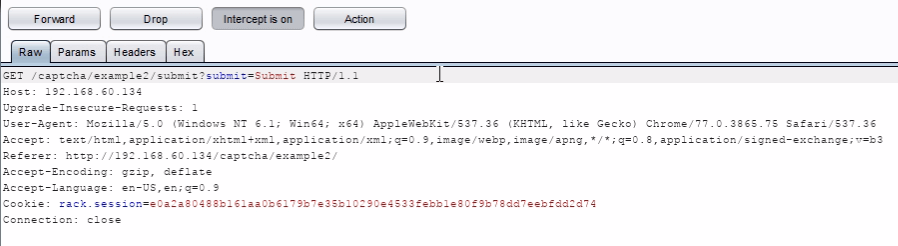
Example 3 In this example, the answer is leaked by the application.
By inspecting the response sent back by the server, you should be able to write a script that can automatically break this captcha.
Captcha solution is passed in the cookies, for working, you need to write a simple script to retrieve the cookie value and send it back as a response.
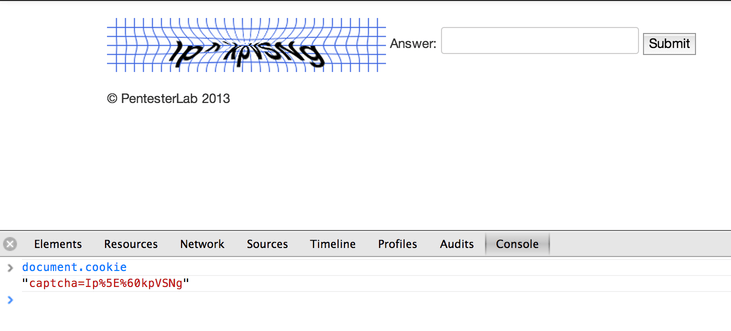
You can also retrieve the captcha from the cookie using the JavaScript console and call document.cookie
inspect>console >document.cookie
Script code for Example 3
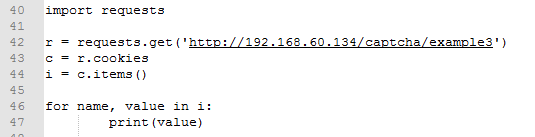
script capcha3 python https://github.com/kaushaljangid/captcha/blob/master/captcha3.py
Example 4 This example is a token flaw problem. If you solve the captcha once you refresh the page, the info will be sent again and again. When you try to crack a captcha, make sure that answer can only be used once.
This exercise will always tell you success and keep sending requests to the server.
This means that you can write a script to re-send the same info multiple times, creating a possible denial of service attack.
Example 5 – This is database flaw, the database has a small number of images, and can be exploited by running a script that downloads the image, checks its MD5 checksum and compares it to a preset checksum table.
script capcha5 python https://github.com/kaushaljangid/captcha/blob/master/captcha5.py
Example 6 – In this exercise you can retrieve the captcha answer by using a OCR tool like tesseract. You need to create a script to download the image and then run tesseract with the following code: tesseract imagefile.png out this will create a out.txt file withe the answer to the captcha.
Once again You can create a script to automate the process.
Example 7 – This is an iteration of the previous example, here you will have to remove the blue lines in the image, to do so you can change the value of the threshold on the image, this can be achieved by using the same method as above but running the following code:
convert imagefile.png -white-threshold 1% imagefile.png tesseract imagefile.png out
Example 8 – This is another version of the examples above, the difference here is that the image is imploded, to get the word out from the image run this code:
convert imagefile.png -white-threshold 20% imagefile.png convert imagefile.png -implode -0.5 imagefile.png tesseract imagefile.png out
Example 9 – This captcha relies on asking the client to perform a simple arithmetic operation, it’s really simple to crack. You can just eval the string provided (probably not a good idea) or you can write a simple parser to do the arithmetic operation for you.
These kind of protection will protect from really dumb bots but is really easy to bypass for anyone who can do a bit of scripting.
However, if we see the source code we will see that both the numbers and the operators are passed in text, not as images:
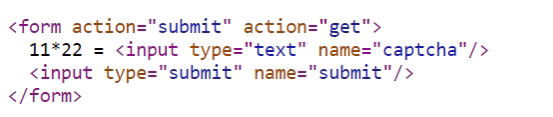
Therefore create a script that reads the source code and extracts the information (numbers and operator), calculate the arithmetic operation and pass it on the form.
script capcha9 python https://github.com/kaushaljangid/captcha/blob/master/captcha9.py
Watch POC
If you have any question then please comment in the box.
Disclaimer: This tutorial is knowledge purpose only.