A Security firm Intezer discovered a new, sophisticated malware named “HiddenWasp”, targeting Linux systems.
HiddenWasp malware is composed three dangerous components, such as Rootkit, Trojan and malicious script.
HiddenWasp server hosted in HongKong based company. The command of the Malware is automated.
Following system are working as threat actors.
- Local Filesystem Manipulation – The engine can be used to upload all kinds of file to the victim hosts or hijack any user data, including both personal and system information. This is particularly worrying as this can be used to lead to crimes such as financial theft and identity theft.
- Command Execution – The main engine can automatically launch all kinds of commands including ones with root permissions if such a security bypass is included.
- Additional Payload Delivery – The made infections can be used to install and launch other malware including ransomware and cryptocurrency miners.
- Trojan Operations –The HiddenWasp Linux malware can be used to take over control of the affected computers.
HiddenWasp Malware is undetectable on VirusTotal platform. See the following image.
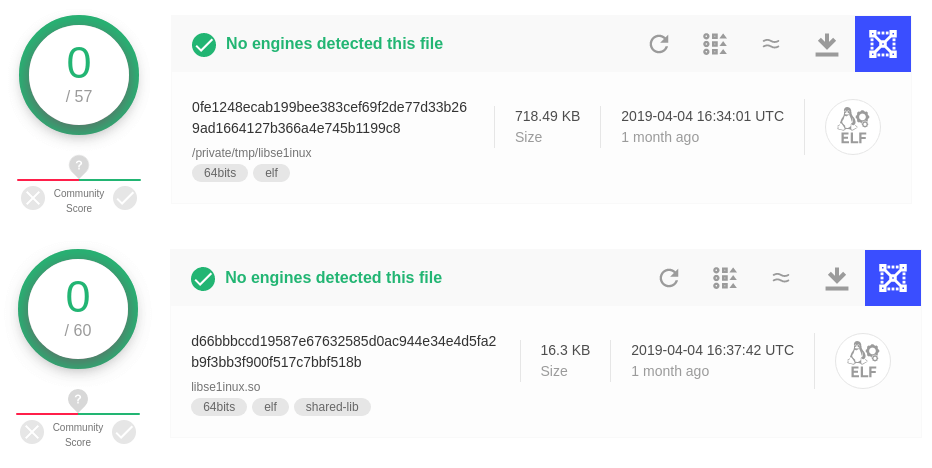
When the researchers have spotted these undetected files in VirusTotal it seemed that among the uploaded artifacts there was a bash script along with a trojan implant binary.
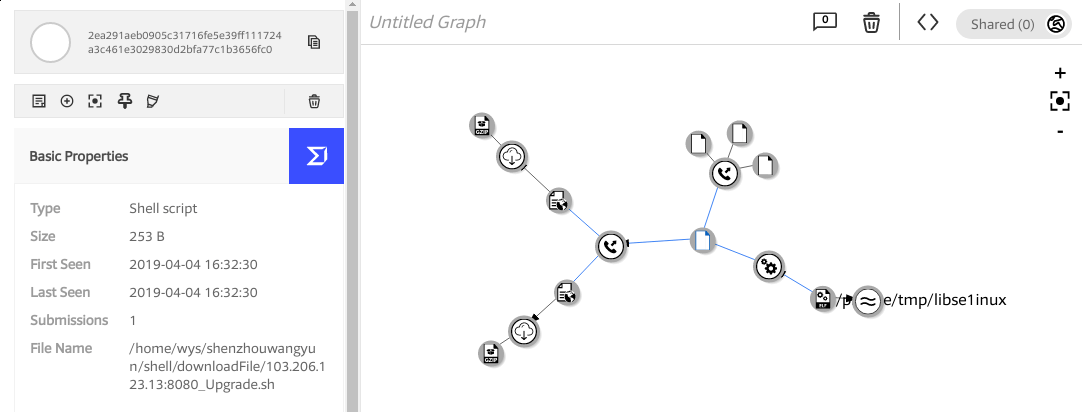
• The malware is still active and has a zero-detection rate in all major anti-virus systems.
• Unlike common Linux malware, HiddenWasp is not focused on crypto-mining or DDoS activity. It is a trojan purely used for targeted remote control.
• Evidence shows in high probability that the malware is used in targeted attacks for victims who are already under the attacker’s control, or have gone through a heavy reconnaissance.
• HiddenWasp authors have adopted a large amount of code from various publicly available open-source malware, such as Mirai and the Azazel rootkit. In addition, there are some similarities between this malware and other Chinese malware families, however the attribution is made with low confidence.
Prevention
In addition, in order to check if your system is infected, you can search for “ld.so” files — if any of the files do not contain the string ‘/etc/ld.so.preload’, your system may be compromised. This is because the trojan implant will attempt to patch instances of ld.so in order to enforce the LD_PRELOAD mechanism from arbitrary locations.
Conclusion
Linux malware may introduce new challenges for the security community that we have not yet seen in other platforms. The fact that this malware manages to stay under the radar should be a wake up call for the security industry to allocate greater efforts or resources to detect these threats.