Following tutorial related to Exploiting Authentication Issues of a Web application.
You can also check the POC Video at the end of the article.
In this tutorial, we will learn about the issues in Web Authentication pages because, it is the process by which the identity of a user is verified, usually by means of a password. Once validated, the server must handle the user’s session in order to continue interacting with it. Sessions must be maintained with a unique and unpredictable identifier.
Vulnerabilities related to authentication and session management are critical because they allow an attacker to impersonate a user’s identity and, therefore, have their access privileges.
Requirements
- Burpsuite for temper the request
- Web For Pentester II for testing
- Python for Script running
- Thc-hydra for window or Kali Linux Hydra tool for brute-force
Also See – How to Install Web for Pentester II
What is Hydra?
Hydra is a fast and flexible login cracker which supports numerous protocols to attack.
Example 1 : –
Predictable passwords are probably the easiest and most common way to authenticate yourself.
To start just try the same password as the username admin or may be Developers create accounts with standard passwords like admin, administrator, password, try hopefully you will login in.
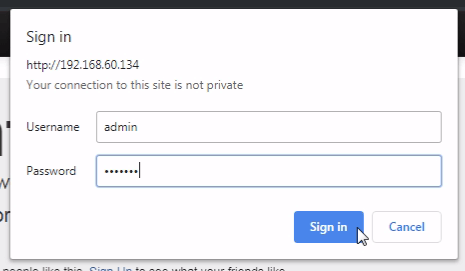

or you can try hydra for brute-force for same username and password
The query for hydra windows and Kali Linux are same
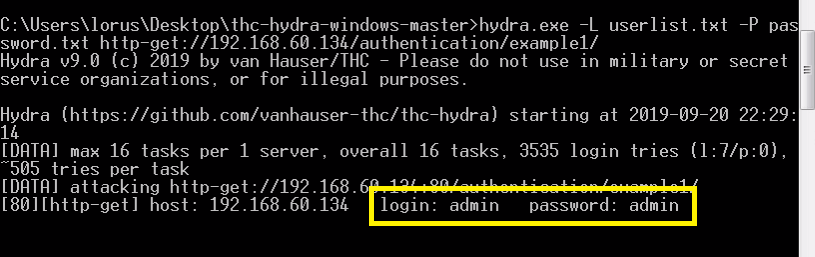
>hydra -L (location of user list) -P (location of password list) http-get://192.168.60.134/authentication/example1/

Result: we get the username and password
Example 2:-
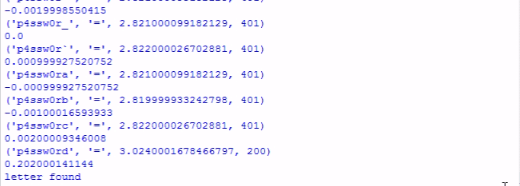
This example is an exaggerated version of a non-time-constant string comparison vulnerability. This means that the web page will analyze the string entered character by character until it finds an error, since the programmer is not bothered to include some type of code to randomize or standardize the time, which it takes for the page to analyze the data.
If we register the time it takes for a certain char to be analyzed, we can see if it’s right or wrong (the right will take more time to retrieve an error since its going to pass to the next character before finding an error).
To exploit this, you can create a script that shows the time it took from submitting the form until the error message appears, or simply view the time manually (wireshark).
Created a simple Python script to check the character of the password by registering an increase in the response:
Download from here
Response result with time it’s a brute-force method
Example 3 :-
In this example, you can log in as user1. Your goal is to get logged in as admin. To do so, you need to carefully look at the response sent back by the server.
Its a cookie manipulation exploit, when you login the server will set up a cookie named user1 with a value user1.
For cookie manipulation just right click > inspect
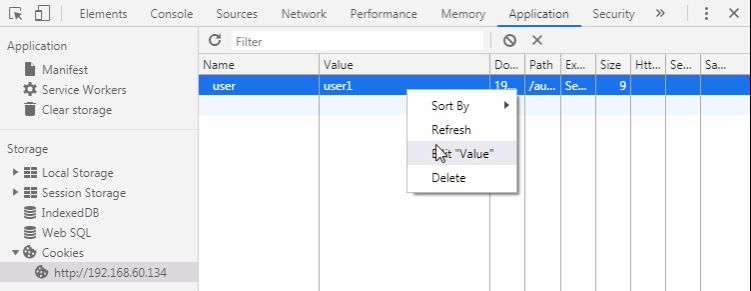
In the Application tab, click cookies and edit the value user1 to admin
application > cookies and edit “value”
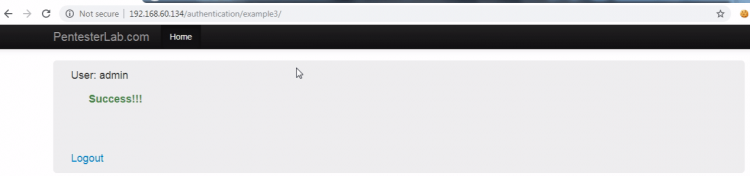
Just re-enter example 3 and we are inside as a admin
Example 4:-
This example is the same as the previous one cookie manipulation exploit only the difference, it’s value is encrypted.
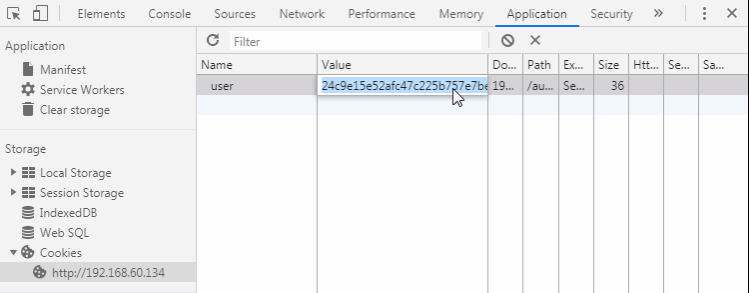
On decrypting the value we get
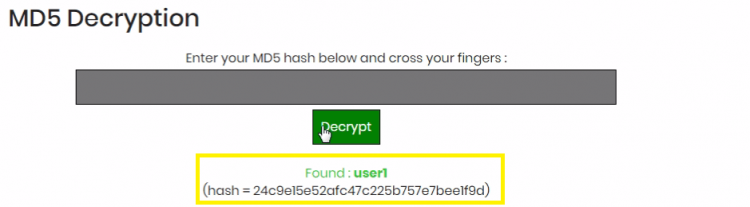
On encrypting the admin we get
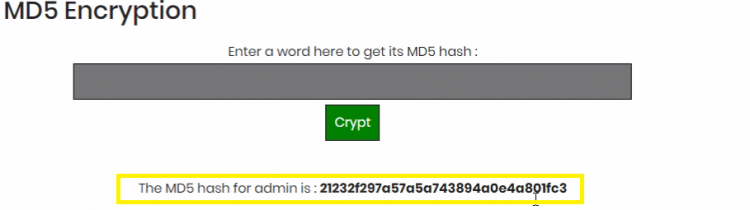
Now we have to replace the user1 encrypted value with admin encrypted value and re-enter example 4 and we can enter as admin.
Example 5:-
In this example, we see that login screen also have the option to register a new user.
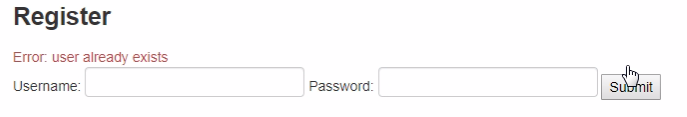
So we are trying to create the admin user, but the user already exists as seen in below image.
 But here is a bug and it seems that we can create the user “admin” by capitalizing a letter “Admin“:
But here is a bug and it seems that we can create the user “admin” by capitalizing a letter “Admin“:
![]()
And that time of validation does not take into account its case insensitive
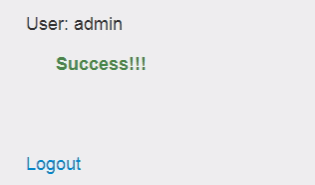
Which means, when we creating the user in the web application, it is case sensitive, but in the database info is registered, and it does not assume the difference between lower and upper case. Finally we just login as a admin.
Example 6:-
As seen the previous issue, the developer decided to use a case sensitive algorithm to filter the data registered on the database but he still forgot that MySQL takes into account space, but its registration page doesn’t. We can still bypass this by creating a user “admin “ by using space after admin.