Today, we are going to teach you about DNSRECON which is use for DNS Information gathering.
It is using to enumerate the standard records of a domain like A, NS, SOA, MX etc.
Its provides the ability to perform :
- Check all NS Records for Zone Transfers.
- Enumerate General DNS Records for a given Domain (MX, SOA, NS, A, AAAA, SPF and TXT).
- Perform common SRV Record Enumeration. Top Level Domain (TLD) Expansion.
- Check for Wildcard Resolution.
- Brute Force subdomain and host A and AAAA records given a domain and a wordlist.
- Perform a PTR Record lookup for a given IP Range or CIDR.
- Check a DNS Server Cached records for A, AAAA and CNAME Records provided a list of host records in a text file to check.
- Enumerate Common mDNS records in the Local Network Enumerate Hosts and Subdomains using Google.
what we are going to perform today are follow:
- Top level domain Expansion
- Reverse Lookup against IP range
- Domain Brute Force Enumeration
- Cache Snooping
- Standard Records Enumeration
- Zone Walking
So lets start..
dnsrecon is installed in kali linux by default.
Top level domain Expansion
A top-level domain (TLD) is one of the domains at the highest level in the hierarchical Domain Name System of the Internet for example “.com” is the top level domain. The extension is usually for websites that use country codes as their top level domains: .in, .uk, .au etc. As the name suggests Top level domain Expansion means to expand your domain from one region to other which is also known as Zone Transfer.
The security problem with DNS zone transfer is that when a user is trying to transfer a zone, it sends a DNS query to list DNS servers such as name servers, host names. MX and CNAME records, zone serial numbers, live records, etc.
dnsrecon – A powerful DNS enumeration script
root@kali:~# dnsrecon -h usage: dnsrecon.py [-h] [-d DOMAIN] [-n NS_SERVER] [-r RANGE] [-D DICTIONARY] [-f] [-t TYPE] [-a] [-s] [-g] [-b] [-k] [-w] [-z] [--threads THREADS] [--lifetime LIFETIME] [--tcp] [--db DB] [-x XML] [-c CSV] [-j JSON] [--iw] [-v]
Optional arguments:
-h, --help show this help message and exit -d DOMAIN, --domain DOMAIN Target domain. -n NS_SERVER, --name_server NS_SERVER Domain server to use. If none is given, the SOA of the target will be used. -r RANGE, --range RANGE IP range for reverse lookup brute force in formats (first-last) or in (range/bitmask). -D DICTIONARY, --dictionary DICTIONARY Dictionary file of subdomain and hostnames to use for brute force. Filter out of brute force domain lookup, records that resolve to the wildcard defined IP address when saving records. -f Filter out of brute force domain lookup, records that resolve to the wildcard defined IP address when saving records. -t TYPE, --type TYPE Type of enumeration to perform. -a Perform AXFR with standard enumeration. -s Perform a reverse lookup of IPv4 ranges in the SPF record with standard enumeration. -g Perform Google enumeration with standard enumeration. -b Perform Bing enumeration with standard enumeration. -k Perform crt.sh enumeration with standard enumeration. -w Perform deep whois record analysis and reverse lookup of IP ranges found through Whois when doing a standard enumeration. -z Performs a DNSSEC zone walk with standard enumeration. --threads THREADS Number of threads to use in reverse lookups, forward lookups, brute force and SRV record enumeration. --lifetime LIFETIME Time to wait for a server to response to a query. --tcp Use TCP protocol to make queries. --db DB SQLite 3 file to save found records. -x XML, --xml XML XML file to save found records. -c CSV, --csv CSV Comma separated value file. -j JSON, --json JSON JSON file. --iw Continue brute forcing a domain even if a wildcard records are discovered. -v Enable verbose
Working Example’s
However DNSRecon provides the ability to perform Zone Transfers and we can use following commands to perform Zone transfer:
dnsrecon -d (example.com) -a
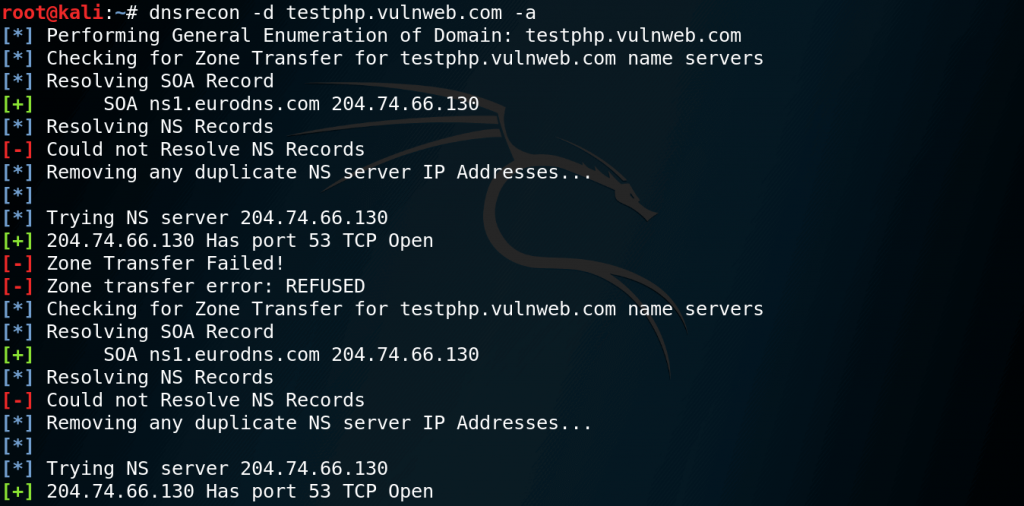
or
dnsrecon -d (example.com) -t axfr
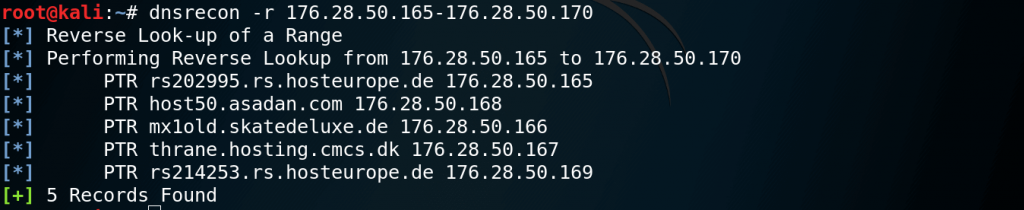
Reverse Lookup against IP range
DNSRecon can perform a reverse lookup for PTR (Pointer) records against IPv4 and IPv6 address ranges. Command for reverse lookup IP range :
dnsrecon -r (startIP)-(endIP)
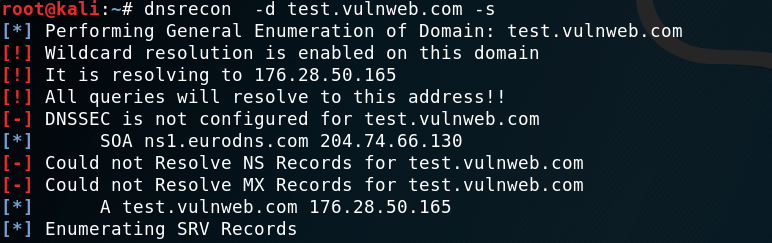
Also reverse lookup can be performed against all ranges in SPF records with the command :
dnsrecon -d (example.com) -s
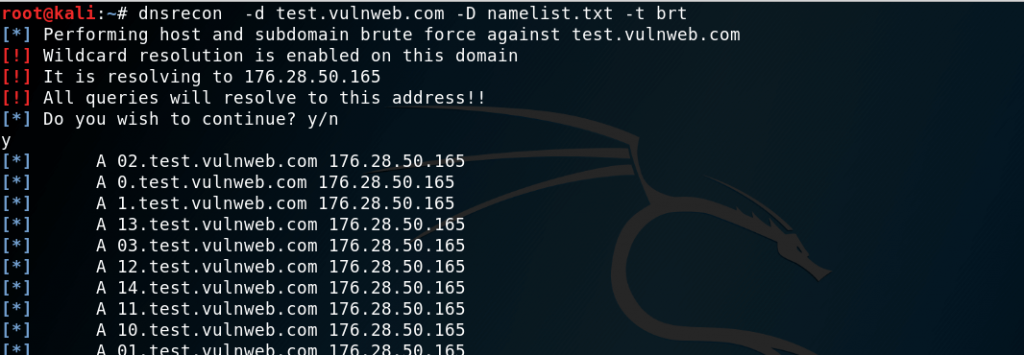
Domain Brute Force Enumeration
For performing Domain Brute force technique, we have to give a name list and it will try to resolve the A,AAA and CNAME records against the domain by trying each entry one by one.
In order to perform domain brute force attack user needs to type below command:
dnsrecon -d (example.com) -D (namelist.txt) -t brt
or we can use predefined namelist.txt available in /usr/share/wordlists/dnsmap.txt
Cache Snooping against name servers
DNS cache snooping happens when the DNS server has a specific DNS record cached. This DNS record will often reveal plenty of information about the name servers and other DNS information. However DNS cache snooping does not happen quite often because servers normally do not cache DNS records.
Command for cache snooping againt name servers:
dnsrecon -t snoop -n (server) -D (namelist.txt)
or we can use predefined namelist.txt available in /usr/share/wordlists/dnsmap.txt
![]()
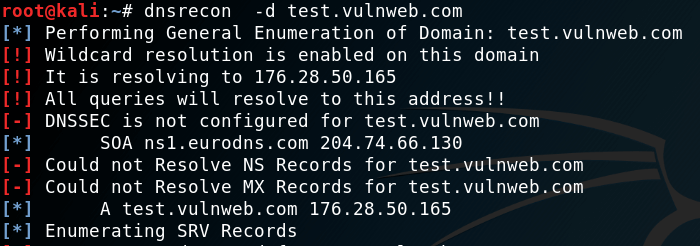
Standard Records Enumeration
Standard Enumeration is generally used to gather information about NameServers,SOA and MX records. Command for perform standard enumeration:
dnsrecon -d (example.com)
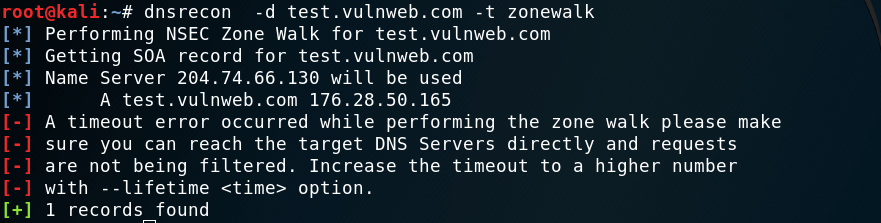
Zone Walking
If Zone Transfer are not correctly configured we can extract almost all internal records of a domain which is known as Zone Walking. The information that can be obtained can help us to map network hosts by enumerating the contents of a zone command for zone walking :
dnsrecon -d (example.com) -t zonewalk