Anonymity is an interesting protective thing, whether inside or outside the computer network.
In this article I am going to use a VPN, Tor and ProxyChains together for more secure anonymity.
Let discuss the basics of VPN, Proxychains and Tor.
What is A VPN?
VPN stands for Virtual Private Network. This is a type of software that allows you to connect to the internet via an encrypted tunnel, which is routed through a server. It hides your IP address and masks your online identity so that all of your online actions are hidden.
Also See- Top 5 VPN For Lifetime Subscription
What are Proxychains?
This is an open source software for GNU/Linux systems.
proxychains – a tool that forces any TCP connection made by any given application to follow through proxy like TOR or any other SOCKS4, SOCKS5 or HTTP(S) proxy.
Supported auth-types: “user/pass” for SOCKS4/5, “basic” for HTTP.
proxyresolv – DNS resolving. Used to resolve host names via proxy or TOR.
What is Tor?
Tor is a software that enables you to hide your identity on the internet. It is an open network that helps defend against traffic analysis and grants you a high level of privacy.
System requirement
- ProtonVPN software for window
- Proxychains
- Tor
- Kali Linux
Let’s start…
I am using ProtonVPN so first we need to open a temp-mail.org website for temporary mail address.
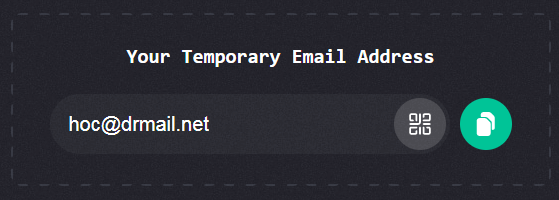
After creating temporary mail ID Login, download free ProtonVPN setup for Windows System from this link protonvpn.com
After install ProtonVPN login
Click connect with desire location
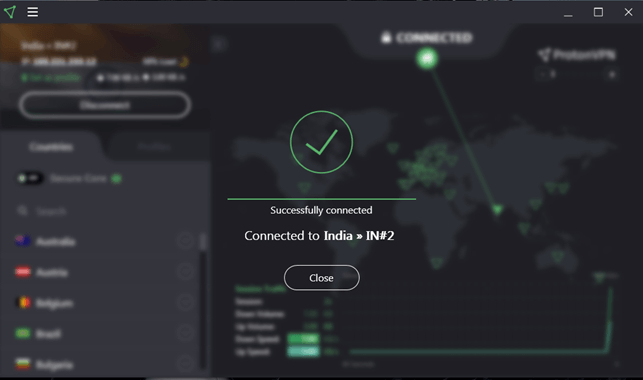
For check ip address Google > whatismyip
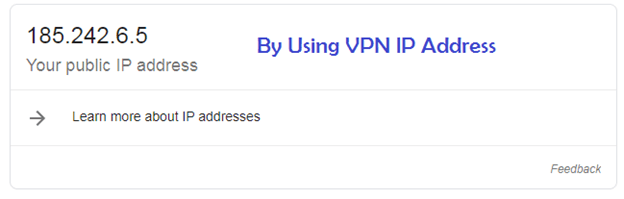
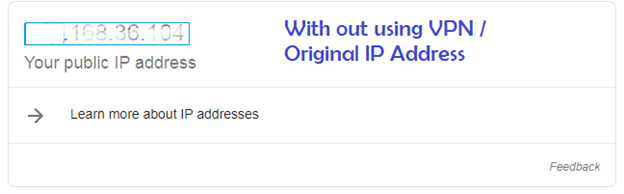
Now the next step, go to virtual machine in toolbar select VM >settings…
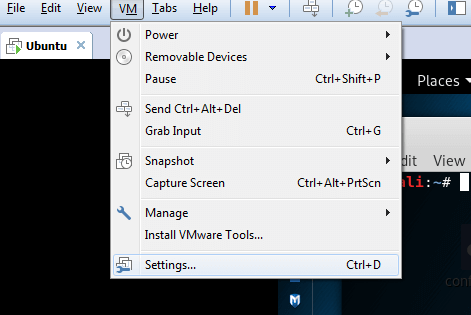
Click network adapter > select NAT: used to share the host’s IP Address > ok
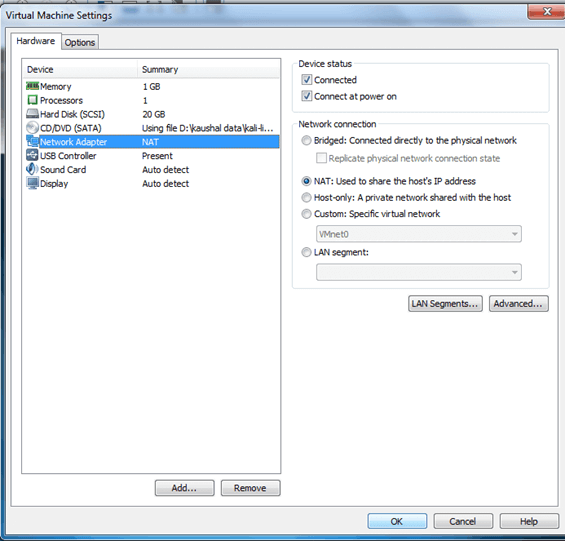
In Virtual Machine
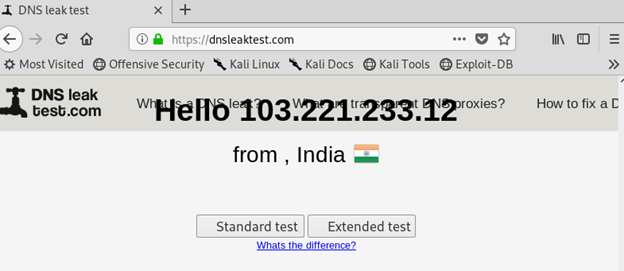
Open browser in Kali Linux and go to website dnsleaktest.com
Now we need to install and configure proxychains with tor
Proxychains is installed in kali linux by default but if there is a case not install
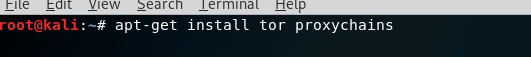
Following Command to install Proxychains and Tor
apt-get install tor proxychains
After installing the packages, we will configure Proxychains for a dynamic chain and add a line to the Socks5 protocol at the end of the file.
Locate the proxychains configuration file by opening a terminal and executing the locate proxychains command.
It should be located in /etc/proxychains.conf. For configuring Proxychains
![]()
Modify the configuration file with a file editor such as leafpad or nano.
Type the following command into terminal:
leafpad /etc/proxychains.conf
![]()
we will use the dynamic chain setting. Uncomment the dynamic chain line
- Delete the # sign before dynamic_chain.
- Put a # signal before the strict_chain function.
For prevent dns leaks uncomment the line where it starts with Proxy DNS requests no leak for DNS data.
Put the following Socks5 protocol statement on the last line: socks5 127.0.0.1 9050

Save the file > all done.
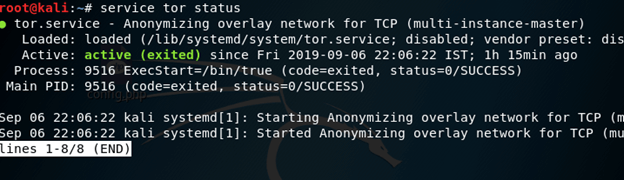
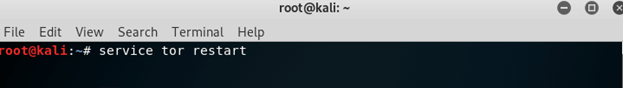
To start Tor service open terminal and type:
#service tor start
if Tor service is already start then type:
#service tor restart
For check status of tor open terminal and type
service tor status
Verify the Configuration
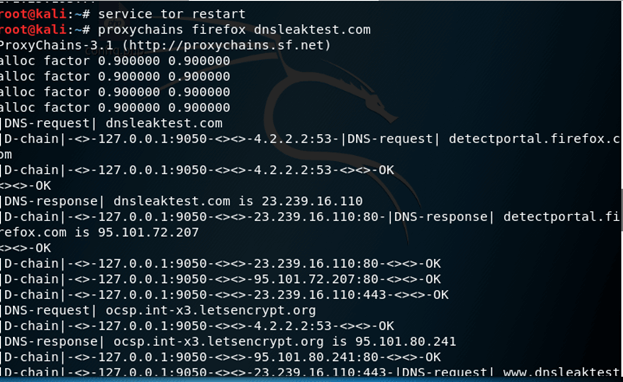
We can verify that the proxies are working by executing the proxychains curl icanhazip.com command.
Or
proxychains firefox www.dnsleaktest.com
![]()
Result
Result of Dnsleaktest.com
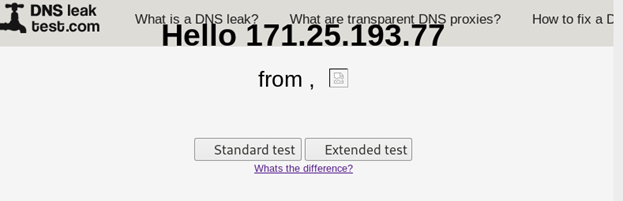
On clicking standard test

For any command you want to remain anonymous, use the following syntax:
proxychains [program] [argument]