Today, BurpSuite a new community edition 2.1.01 released for Penetration Tester.
Many Infosec people are using BurpSuite for personally and corporate level. Using Burp to Test for the OWASP Top Ten vulnerabilities.
Burp Suite is a graphical suite for testing Web application security and written in Java and developed by PortSwigger Web Security.
In this new BurpSuite Community Edition 2.1.01 release adds support for WebSockets in Burp Repeater.
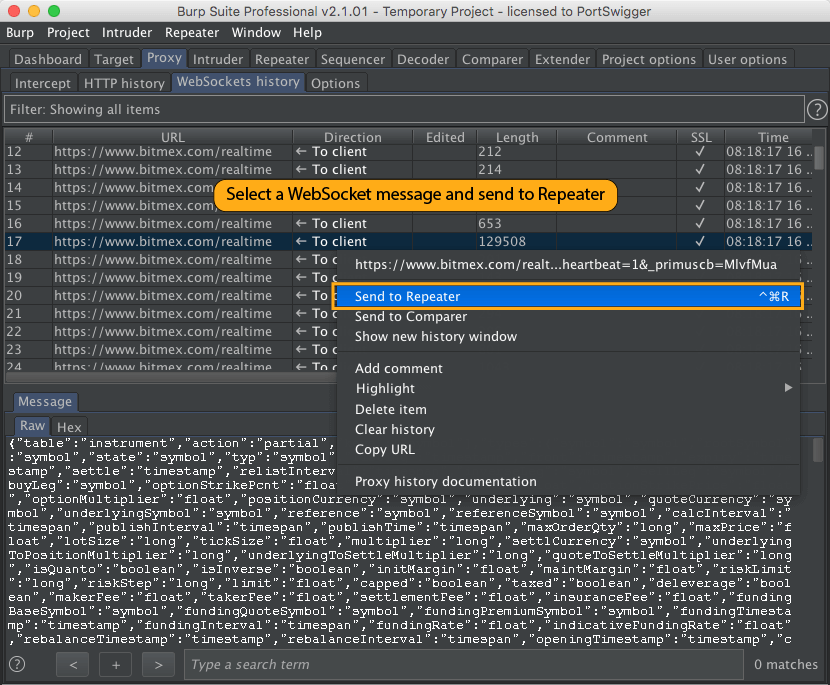
You can select a WebSocket message in the Proxy history or intercept tab, and choose “Send to Repeater” from the context menu:
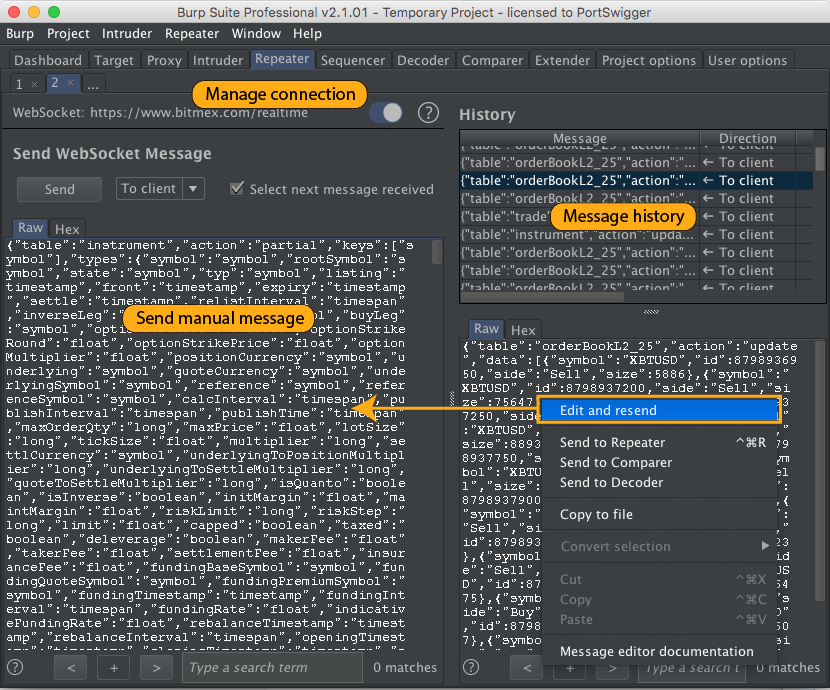
Each message you send to Repeater opens in a new tab. Here, you can manually edit and send the message, view the full message history, pick a message from the history and manually edit and resend it, and manage the WebSocket connection:
Burp Suite has three editions.
- A Community Edition that can be downloaded free.
- A Professional Edition and an Enterprise edition that can be purchased after a trial period.
- The Community edition has significantly reduced functionality.
It was developed to provide a comprehensive solution for web application security checks. In addition to basic functionality, such as proxy server, scanner and intruder, it also contains more advanced options such as a spider, a repeater, a decoder, a comparer, an extender and a sequencer.
Also Read- Top Vulnerability And Assessment Suite Lists
The company behind Burp Suite has also developed a mobile application containing similar software applications compatible with iOS 8 and above.
Burp Suite Features are as follow-
- HTTP Proxy – It operates as a web proxy server, and sits as a man-in-the-middle between the browser and destination web servers. This allows the interception, inspection and modification of the raw traffic passing in both directions.
- Scanner – A web application security scanner, used for performing automated vulnerability scans of web applications.
- Intruder – It can perform automated attacks on web applications and offers a configurable algorithm that can generate malicious HTTP requests. The intruder can test and detect SQL Injections, Cross Site Scripting, parameter manipulation and vulnerabilities susceptible to brute-force attacks.
- Spider – It is for automatically crawling web applications. It can be used in conjunction with manual mapping techniques to speed up the process of mapping an application’s content and functionality.
- Repeater – A simple function that can be used to manually test an application. It can be used to modify requests to the server, resend them, and observe the results.
- Decoder – For transforming encoded data into its canonical form, or for transforming raw data into various encoded and hashed forms. It is capable of intelligently recognizing several encoding formats using heuristic techniques.
- Comparer – For performing a comparison (a visual “diff”) between any two items of data.
- Extender – Allows the security tester to load Burp extensions, to extend Burp’s functionality using the security testers own or third-party code (BAppStore)
- Sequencer – For analyzing the quality of randomness in a sample of data items. It can be used to test an application’s session tokens or other important data items that are intended to be unpredictable, such as anti-CSRF tokens, password reset tokens, etc.