The Security Researcher found Malicious App on Google Play Store
The ESET Mobile Security Researcher ‘LUKAS STEFANKO’ found Android banking Trojan available on Google play store with 10,000 installs.
This malicious app can bypass Two-factor authentication via SMS. After analysis, he found that the app mostly targeted German, Polish and Czech banks.
According to the statement of Bank, there are clients who were affected and lost approx 10,000 Euro.
The Czech Banking Association (CBA) on Tuesday said in a press release that some Czech banks have faced several attempts to alienate their clients in recent days. Clients lost hundreds to millions of crowns. The case is being investigated by the police. Czech Google did not want to comment on the incident, but CBA says it is deleting the app from Google Play.
Malware Analysis
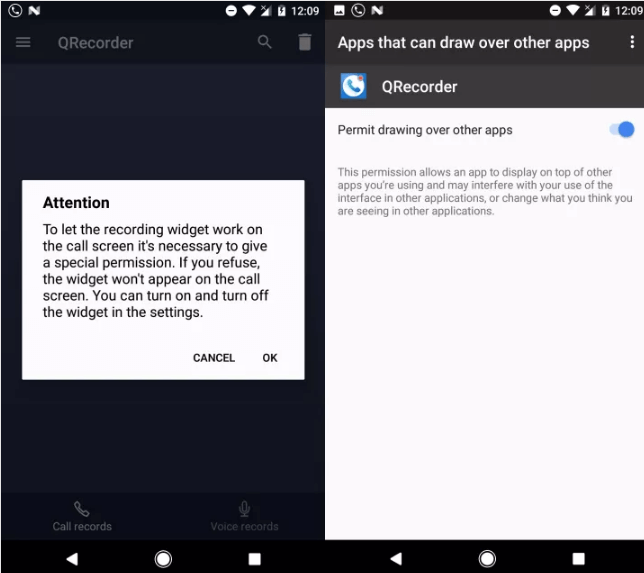
The Banking Trojan installed in QRecorder Android App, it is the automatic call recorder tool as well as Voice recorder.
Once it is installed, it would prompt a user to allow it to draw over other apps as necessary function for an app to work properly. So this functionality mainly helps the malware to control what is displayed to the user.
Cyber criminal can get access to SMS, which is the most important control for money transfer. After bypassing the security, the cyber attacker can send the money remotely without Victim’s knowledge.
How does it Work?
In the first phase, the malicious code detects whether the application is installed on the phone or not.
The banking Trojan sends the credentials to the attacker server, but the malicious functionality needs an activation command from the attacker and downloads the exploit code on the request.
Before the download, the malicious payload, the app would ask the victim to activate the accessibility to gain the process of malware injection.
“We were able to capture the QRecorder Call Recorder. Based on our internal analysis, we can say that the originally legitimate application has been so-called “degraded”. This means that after one of the last updates, the QRecorder became a trojan, ” said Miroslav Dvořák, technical director of ESET.
” It allows attackers to download dangerous content to the Android smartphone, which is also happening,” he adds.
How To Protect?
If you have installed QRecorder, then you must uninstall the app immediately from your smartphone.
Czech Police updated that the malicious app had five victims and stole approx 78,000 euros from their bank accounts. Police have identified the cyber-criminal from one of the Prague ATM.











