Bad month for security people in companies dealing with email marketing campaigns.
The Security researcher Bob has shared the detail with us. He found the information by scanning the database server and find the right path to access the data. He explained in the following article.
On Monday morning, Sept 17th, I have discovered a huge customer database containing 11 million records that included personal details, such as email, full name, gender, physical address (zip code, state, city of residence).
The data was available from an unprotected MongoDB instance set up on Grupo-SMS hosting infrastructure, and could be accessed by anyone from Sept 13th on (when Shodan last indexed it).
The 43.5GB large dataset contained 10,999,535 email addresses, all Yahoo-based. Apart from customer personal information, the database also included DNS details about the email status (sent successfully or not), that showed if the email went through, and server response.
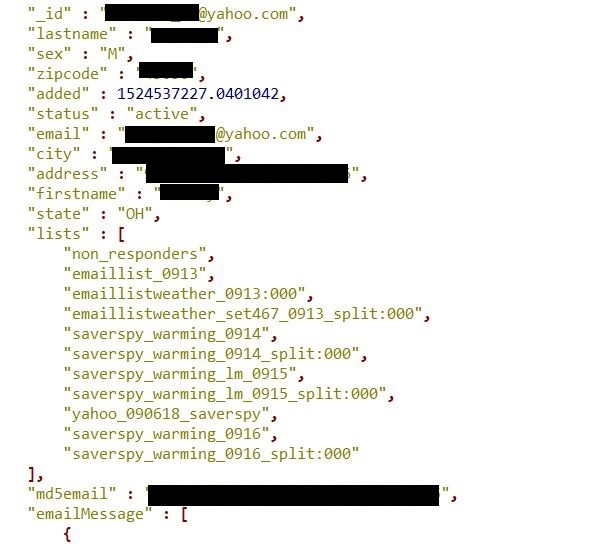
The origin of data remains unknown, as database name itself did not give any clues as of potential owner.
Also, data did not contain any administrator emails, system logs or host information. One hint was given in the description of the lists in which a particular email was part of – “Yahoo_090618_ SaverSpy”.
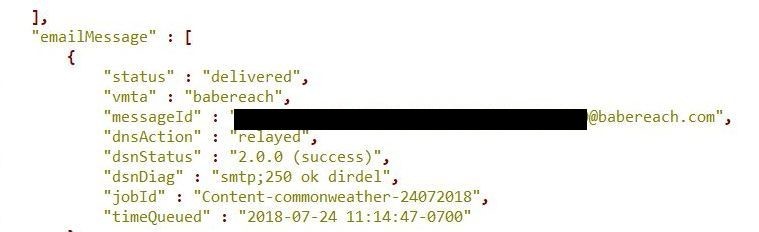
SaverSpy (powered by Coupons.com) are websites that provide printable and digital discount coupons for a wide range of products.
I have tried to contact both organizations about the potential data breach but received no answer by the time of publishing. However, database has been taken offline shortly after notification email sent and now unreachable.
Interestingly, that MongoDB in question has already been tagged as ‘Compromised’ in Shodan and contained ‘Warning’ database with ‘Readme’ collection and ransom note demanding 0.4 BTC for recovering the data. However, at the time of discovery, all data were intact. I assume this is a result of failed script scenario used by crooks (and pure luck for the database owners).
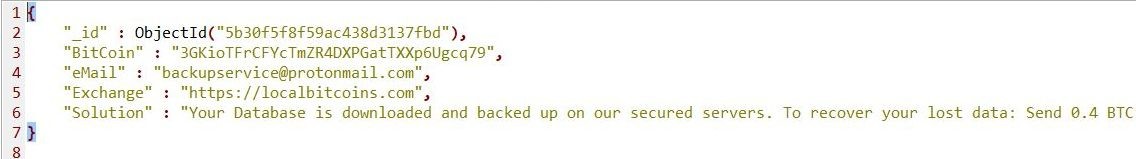
Like in my previous discovery of Veeam, the information from database (e-mails with personal details) was a pure gold for malicious actors such as spammers, scammers, phishers of all kinds – surfaced online due to a human error or default settings misconfiguration (which is for me the same kind of a mistake).
This article is written by BOB Diachenko, he is an PR Consultant and Communications Expert, Journalist, Independent Security Researcher. You can contact him via LinkedIn and Twitter











