Quark Engine – Android Malware Research Engineer System for API Penetration Testing.
- Quark Engine is also bundled with BlackArch.
- An Obfuscation-Neglect Android Malware Scoring System.
- A trust-worthy, practical software that’s ready to boost up your malware reverse engineering.
Why Quark?
Android malware analysis engine is not a new story. Every antivirus company has their own secrets to build it.
We have an order theory of criminal which explains stages of committing a crime. For example, crime of murder consists of five stages, they are determined, conspiracy, preparation, start and practice. The latter the stage the more we’re sure that the crime is practiced, developers said.
According to the above principle, Quark-Engine developed order theory of android malware in five stages to see if the malicious activity is being practiced.
They are:
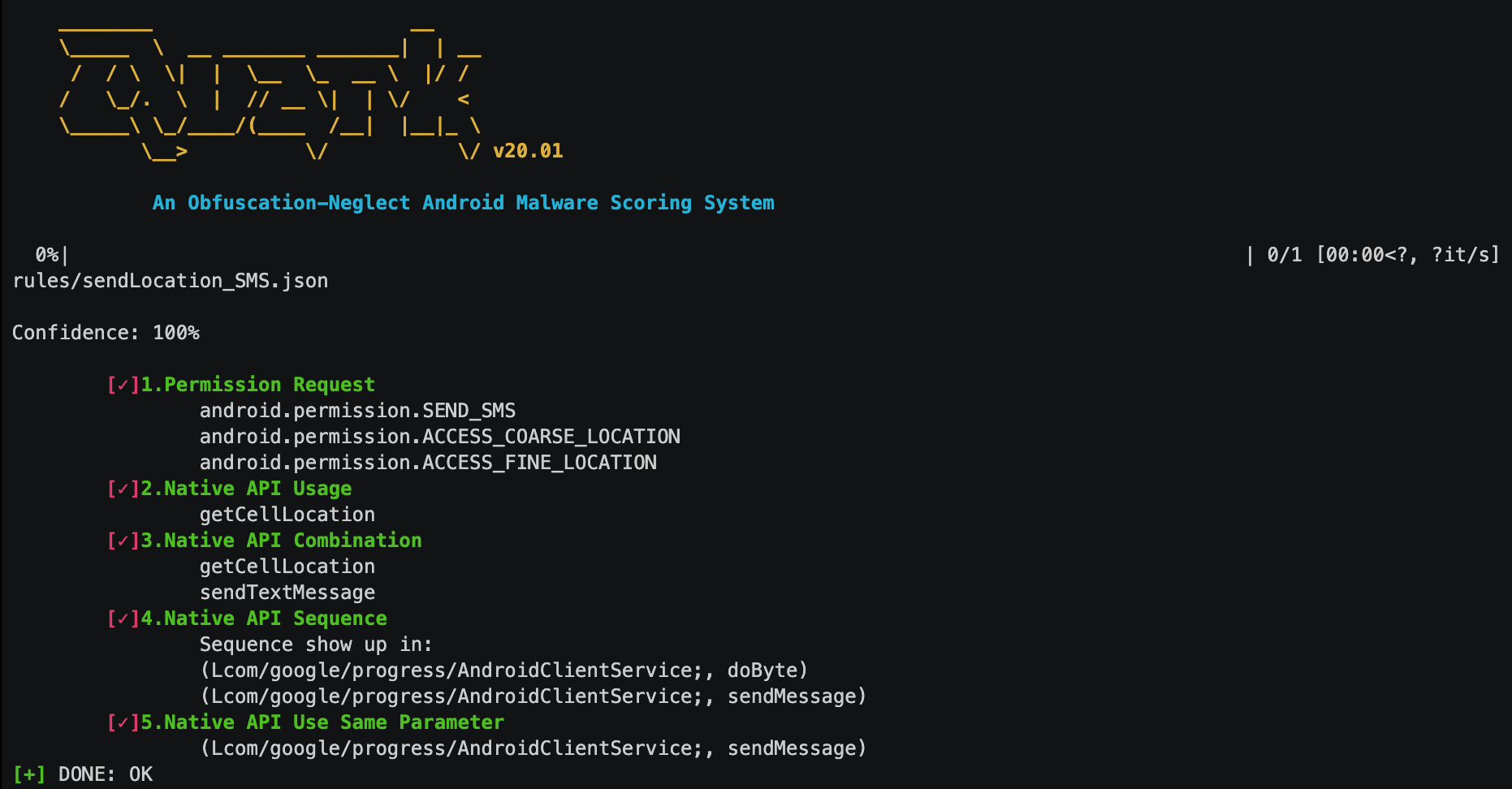
1. Permission requested.
2. Native API call.
3. Certain combination of native API.
4. Calling sequence of native API.
5. APIs that handle the same register.
We not only define malicious activities and their stages but also develop weights and thresholds for calculating the threat level of a malware.
Malware evolved with new techniques to gain difficulties for reverse engineering. Obfuscation is one of the most commonly used techniques. In this talk, we present a Dalvik bytecode loader with the order theory of android malware to neglect certain cases of obfuscation.
Our Dalvik bytecode loader consists of functionalities such as
1. Finding cross reference and calling sequence of the native API.
2. Tracing the bytecode register. The combination of these functionalities (yes, the order theory) not only can neglect obfuscation but also match perfectly to the design of our malware scoring system.
Easy to Use and Reading Friendly Report
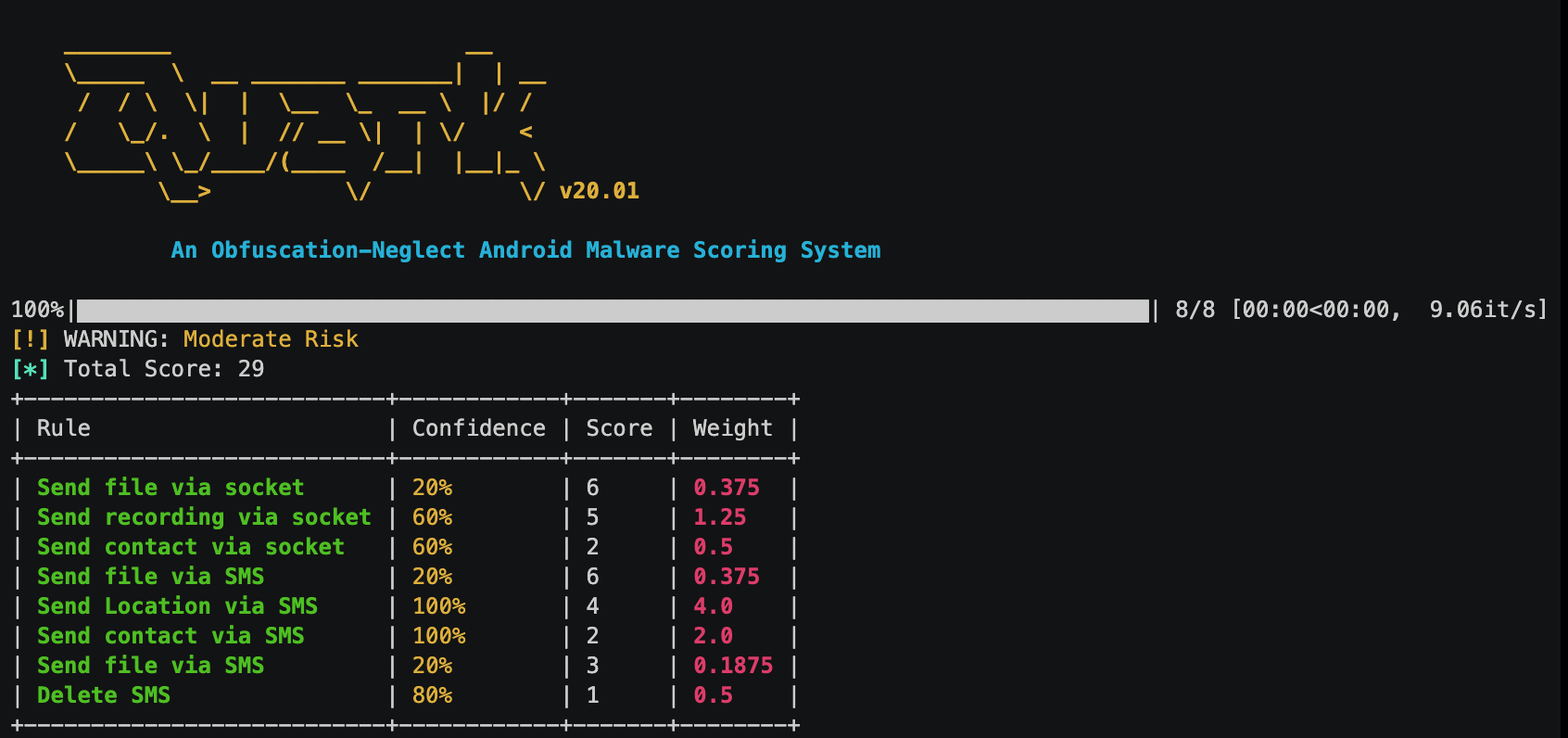
Quark is very easy to use and also provides flexible output formats. There are 3 types of output report: detail report, call graph, and summary report. Please see below for more details.
Detail Report
This is a how we examine a real android malware (candy corn) with one single rule (crime).
$ quark -a sample/14d9f1a92dd984d6040cc41ed06e273e.apk \ -r rules/ \ --detail
and the report will look like:
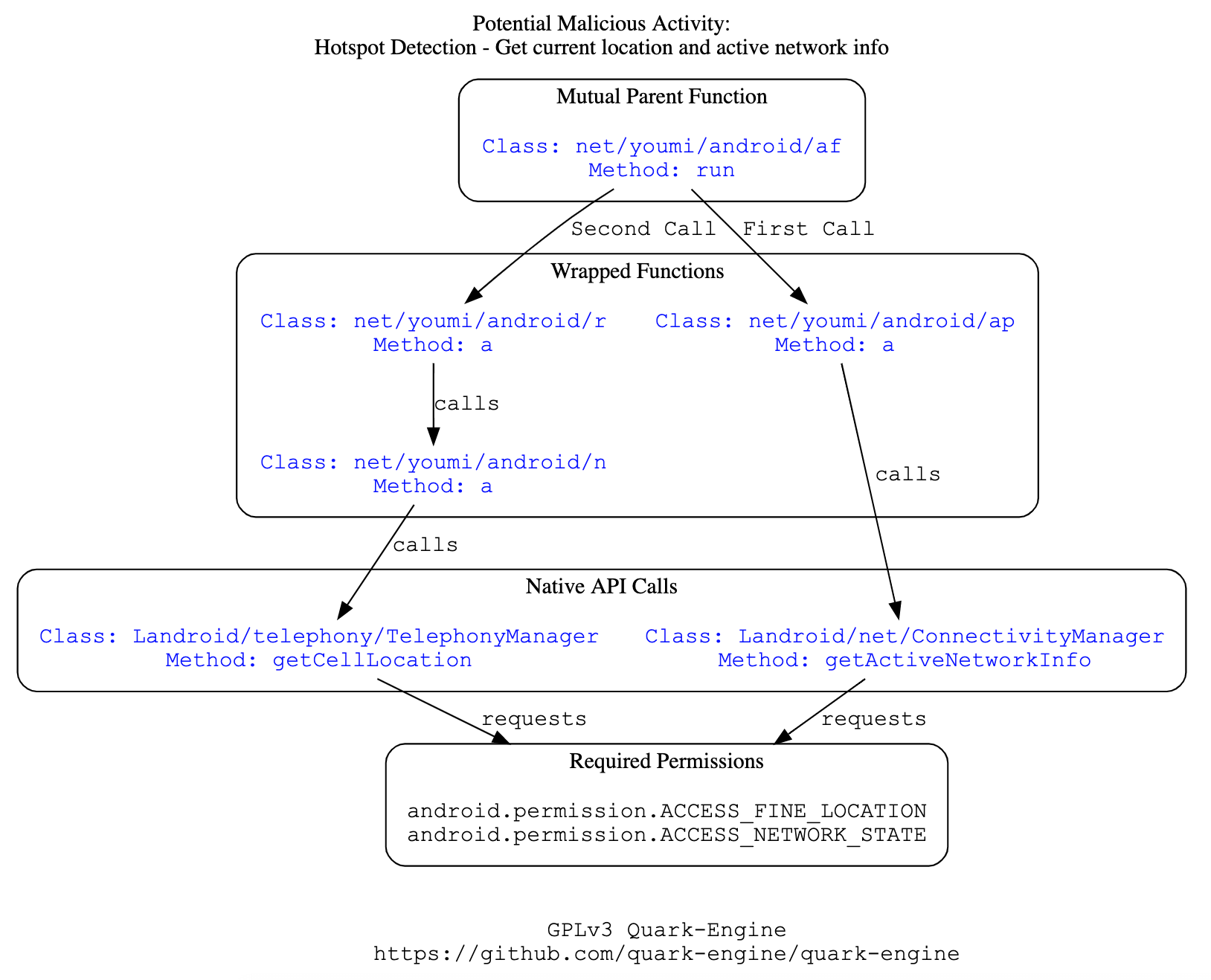
Call Graph for Every Potential Malicious Activity
According to developers they will soon release this feature in the next version of quark!
Summary Report
Examine with rules.
quark -a sample/14d9f1a92dd984d6040cc41ed06e273e.apk \ -r rules/ \ --summary
QuickStart
Installation
$ git clone https://github.com/quark-engine/quark-engine.git; cd quark-engine/quark $ pipenv install --skip-lock $ pipenv shell
Make sure your python version is 3.7, or you could change it from Pipfile to what you have.
Check –help to see the detailed usage description.
$ quark --help
Test It Out
You may refer to the Quark Engine Document for more details of testing and development information.
Analysis Reports of Real Malware
Qaurk Engine will soon provide analysis reports of real malware! For your best experience of viewing the report, please use desktop web browser. We’re planning to make a mobile version of report.
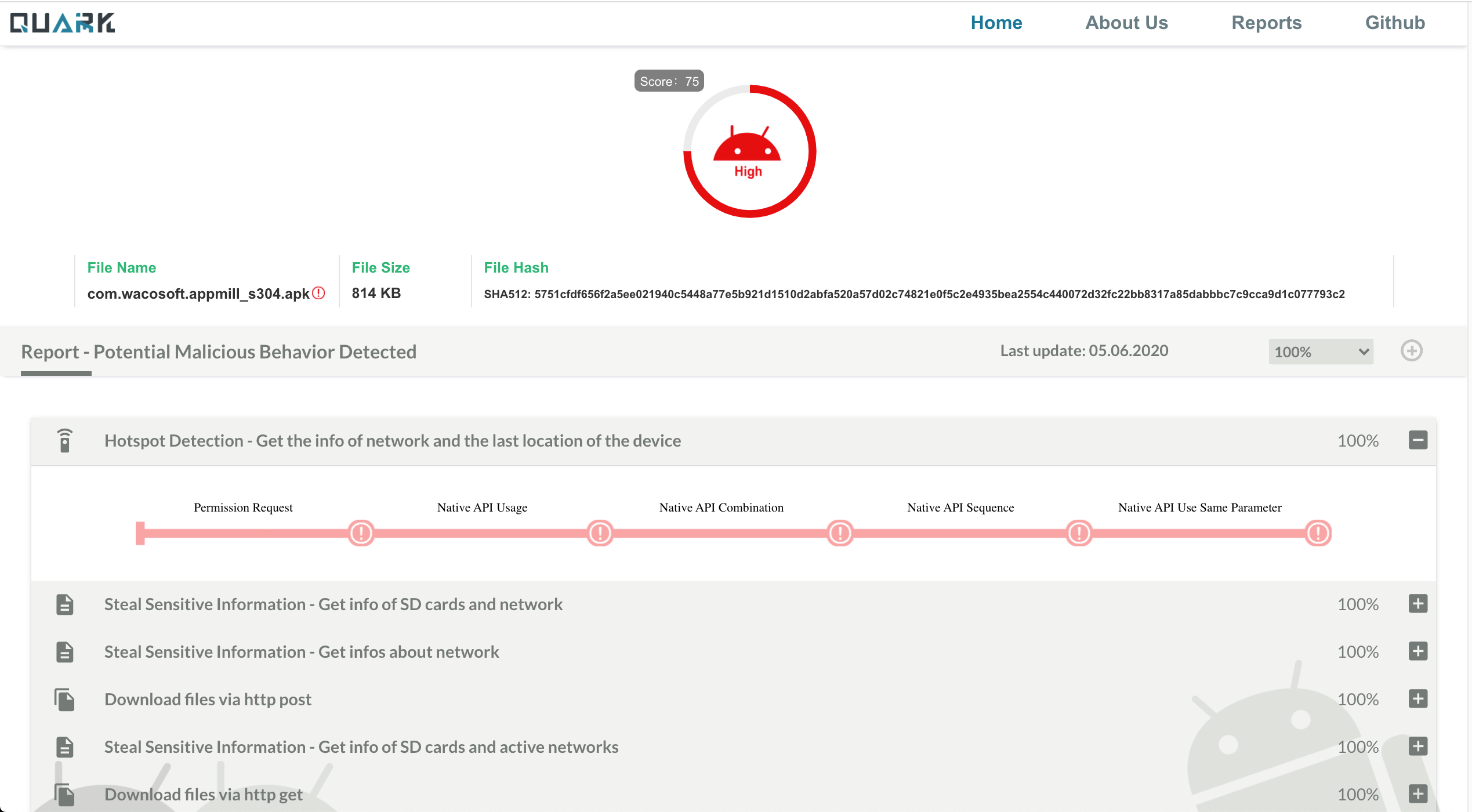
If you really want to see the very first version of report please visit here
Also, we will soon give out our new detection rules!, the developers said.