In this article, we will be taking a closer look at the STRRAT malware.
STRRAT’s been around since 2020 but has seen a recent resurgence in mid 2022. Since then, its popularity is peaking.
Let’s jump right in and get you up to speed on this threat. Analysis by Any Run.
We’ll cover IOCs, network activity and walk you through the dynamic analysis.
What is STRRAT?
STRRAT is a Remote-Access Trojan (RAT) written in JAVA. It’s equipped with a wide range of malicious capabilities:
1. Stealing personal information from web browsers and email programs
2. Being able to save keystrokes typed when the computer is both online and offline.
3. Opening backdoors on infected systems.
4. Imitating a ransomware attack.
The fake ransomware act is where the RAT adds .crimson extension to files without actually encrypting them.
The STRRAT malware family is also well known for its ability to evade detection by security software.
It employs the living off the land tactics, which means that it uses legitimate system tools and software to carry out malicious activities. This makes it difficult to spot, because it blends in with benign system processes.
STRRAT also uses process hollowing to hide its malicious code. This involves creating a new process that appears legitimate, but actually contains the malware’s code.
And, of course, the code has multiple obfuscation layers, making static analysis difficult.
Here’s a high level overview of the malware:
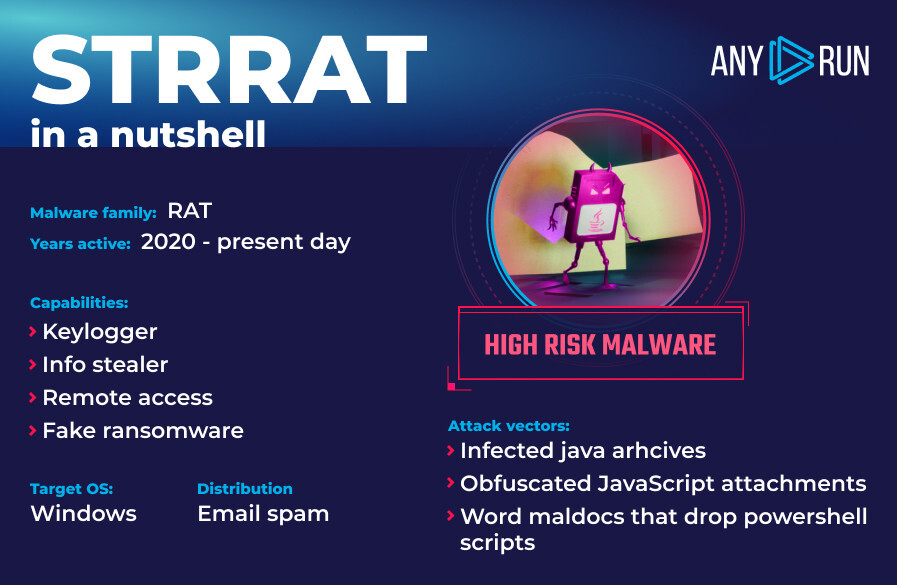
STRRAT malware distribution
STRRAT is a sneaky piece of malware that can get onto your device through a few different ways. A common method is through bulk emailing or phishing attacks.
The forms of STRRAT’s initial propagators differ. The RAT uses malevolent, disguised JavaScript files intended to deliver the virus onto the target’s hardware, Microsoft Maldocs with macros that drop a PowerShell script, and JAR archives.
IOCs and Network Traffic
Here’s the indicators of compromise we managed to find. The main object:
Str.jar
|
|
SHA256
|
682bdbc79d5131b2ed3b8ef1160e0322a5e1c29f41fa4ea7bf181d0efdd77964
|
SHA1
|
89a4528b4b35e38a29ca015dc1a71f4983a39ff9
|
MD5
|
9f745c583f322f39c625b5c2a3540835
|
Dropped executable file
|
|
SHA256
|
C:\Users\admin\AppData\Local\Temp\ina-92668751\na1043254276010525600.dIl |
- jne
- sqllite
- system-hook
The malware also attempted to connect to GitHub and a shady domain:
|
DNS requests |
|
|
Domain |
objects.githubusercontent.com |
|
Domain |
github.com |
|
Domain |
7650.hopto.org |
|
Network Traffic |
|
|
IP |
91.193.75.134 |
|
IP |
199.232.192.209 |
|
IP |
140.82.121.3 |
In addition to transmitting data, we observed frequent attempts to link up with the 91[.]193[.]75[.]134 IP address.
ANY.RUN malware sandbox made it very easy to retrieve all this data.
The sample we will be dealing with today arrived as a JAR file.
A JAR file, or a Java Archive, is a ZIP package that contains a Java executable. Once downloaded, it will run on your machine like any old program as long as you have Java Runtime Environment (JRE) installed.
In addition to being a rare filetype, STRRAT’s Java file is packed full of benign code that can confuse many antivirus programs.
We will be employing a sandbox for dynamic analysis, as it can accurately detect the executable’s threat.
STRRAT malware analysis
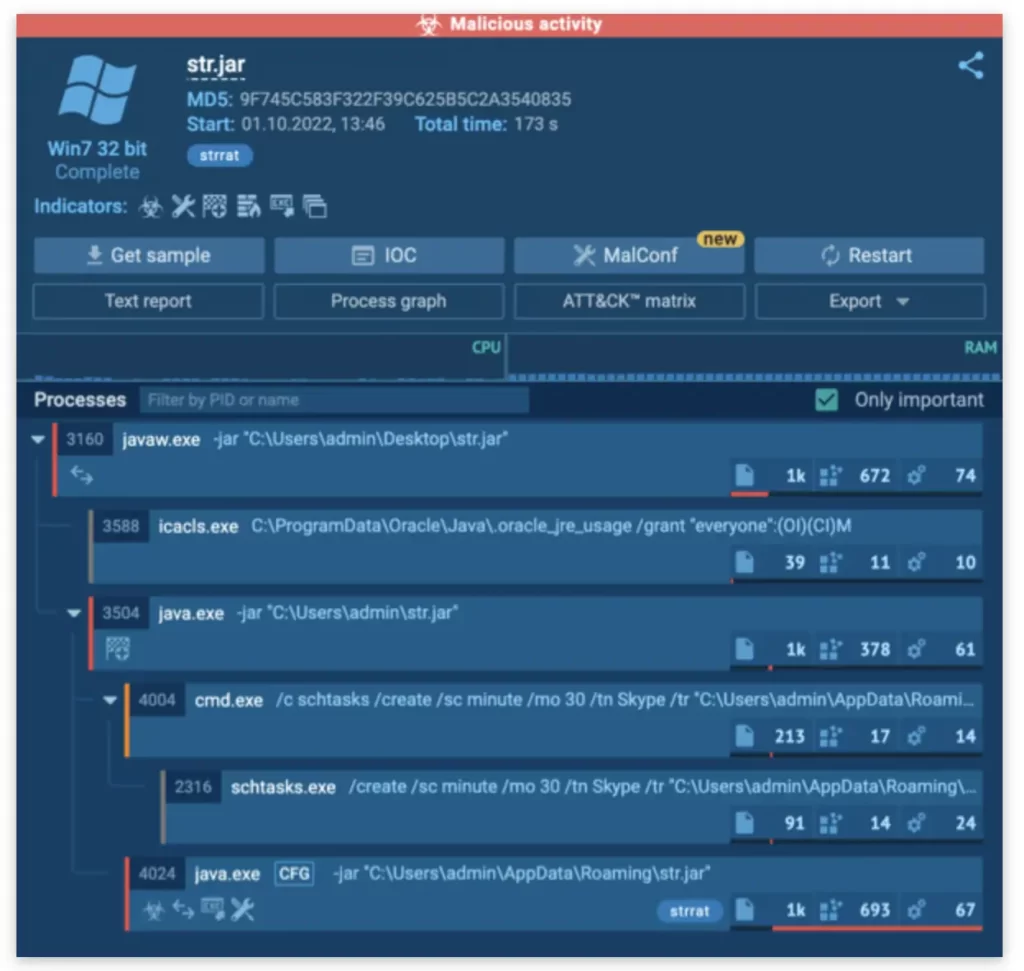
Here’s the STRRAT sample we used for this analysis.
A JAR file replication
The first thing noticeable is that JAR files are being replicated. We start the processing from the desktop, then STRRAT creates copies of the file in two different folders: one in C:\Users\admin and the other in C:\Users\admin\AppData\Roaming. This replication process is repeated regularly as the malware runs.
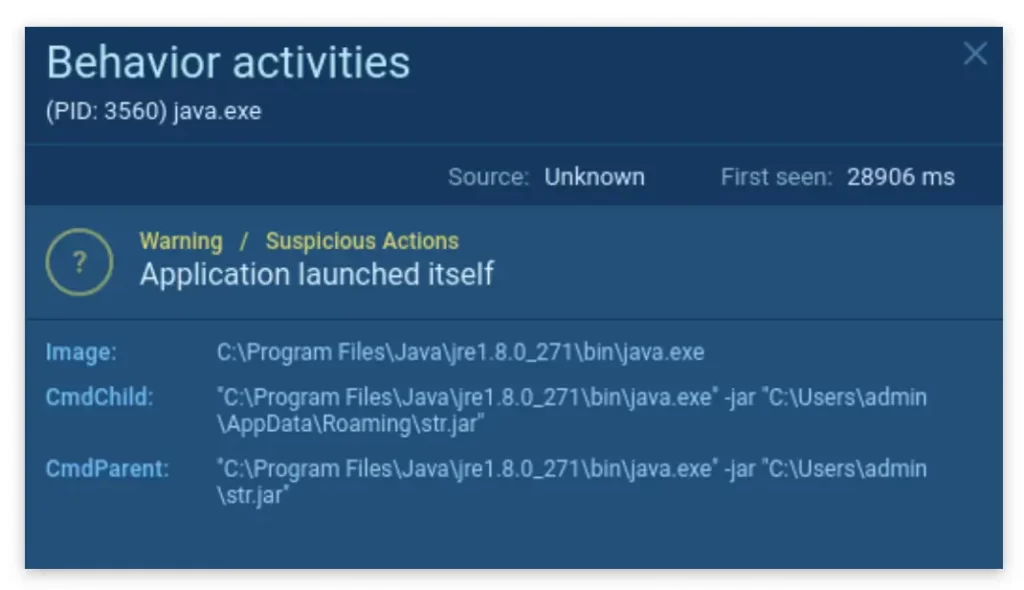
STRRAT controls file access by executing a Java program
Next, the malware executes a command to utilize icacls in order to control file access. This command grants all users permission to access the .oracle_jre_usage folder:
icacls C:\ProgramData\Oracle\Java.oracle_jre_usage /grant “everyone”:(OI)(CI)M
Application launch of STRRAT malware
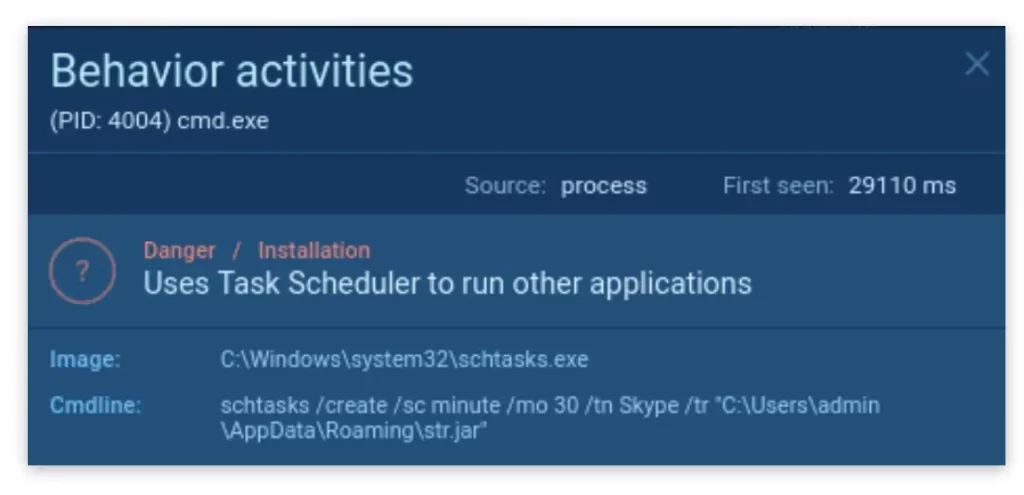
Next, STRRAT creates an event in the Scheduler using the command line:
schtasks /create /sc minute /mo 30 /tn Skype /tr “C:\Users\admin\AppData\Roaming\str.jar
The goal is to program the Task Scheduler to run malicious software in a process called Skype every 30 minutes.
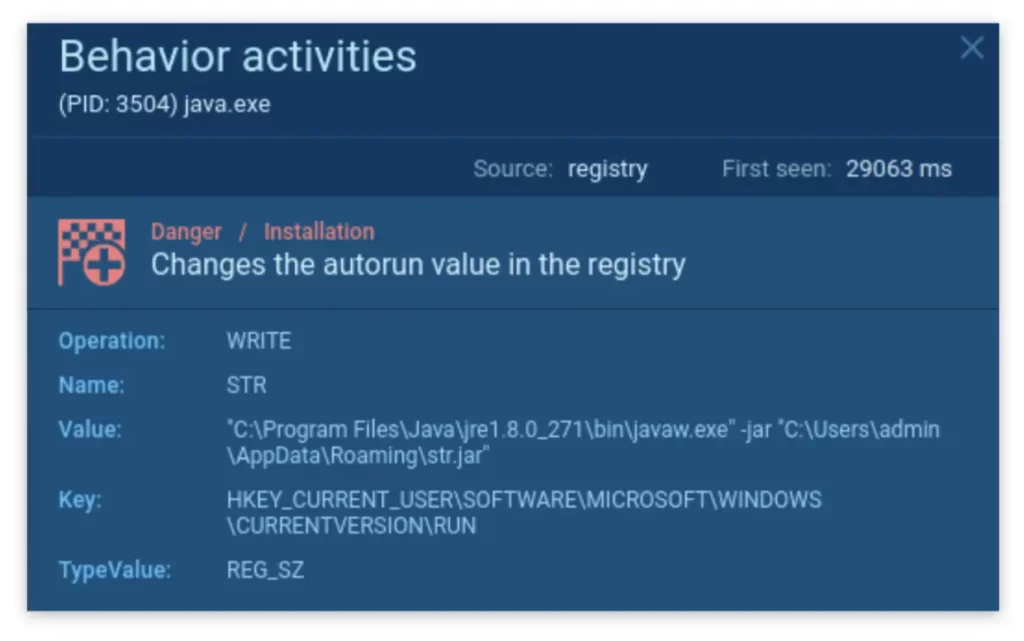
If we examine the 3504 process more closely, we will see that the malware will run itself on startup. It achieves this by:
- First changing the autorun value
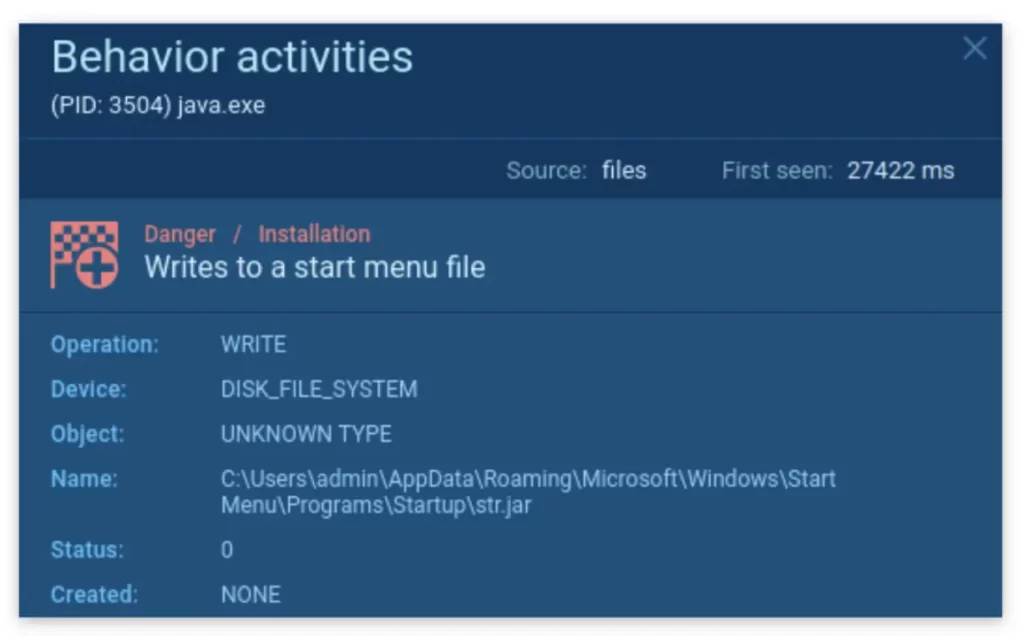
- Then, writing itself into the startup menu
STRRAT spawns more JAR files
STRRAT’s process creates additional Java Archive Files that are obtained from public repos.
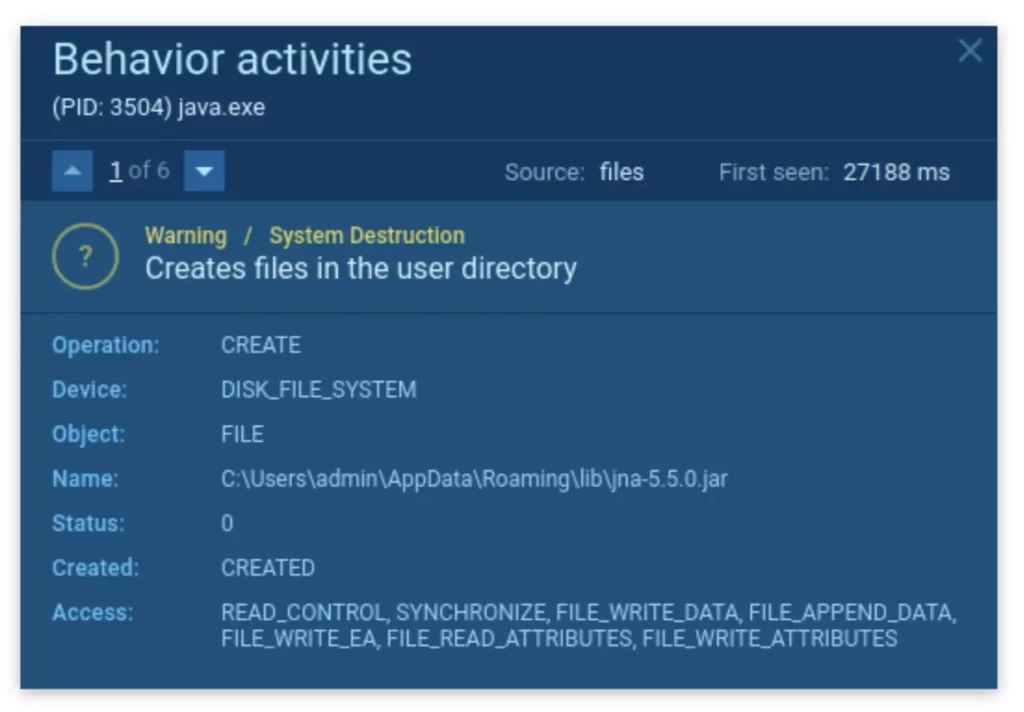
The malicious software was downloaded from the web, and then it generated the library files. If you run the virus through Command Prompt, you can view them. This is a bizarre occurrence – we can trace the program’s logs if we run it with CMD.
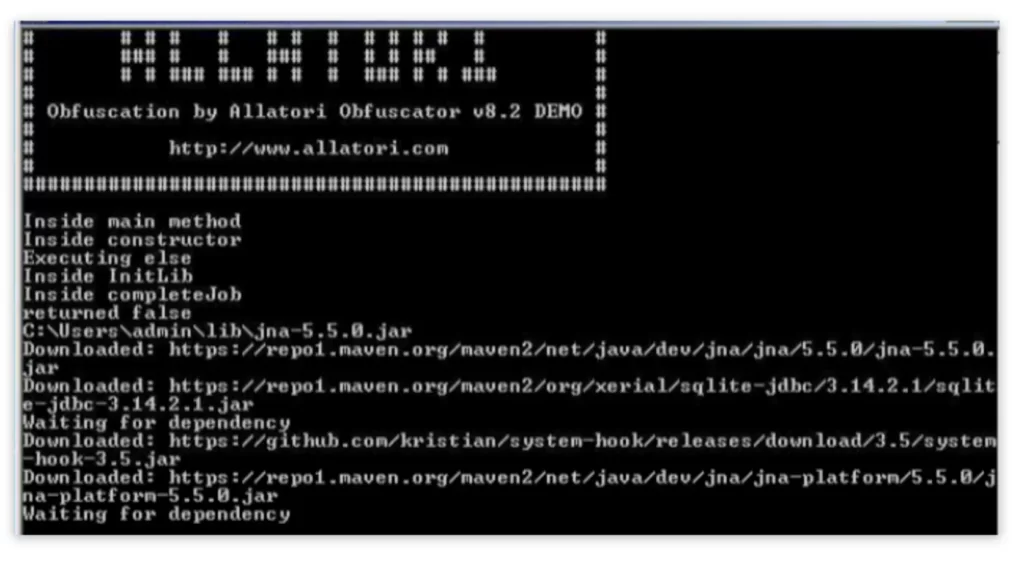
Extracting STRRAT config with ANY.RUN
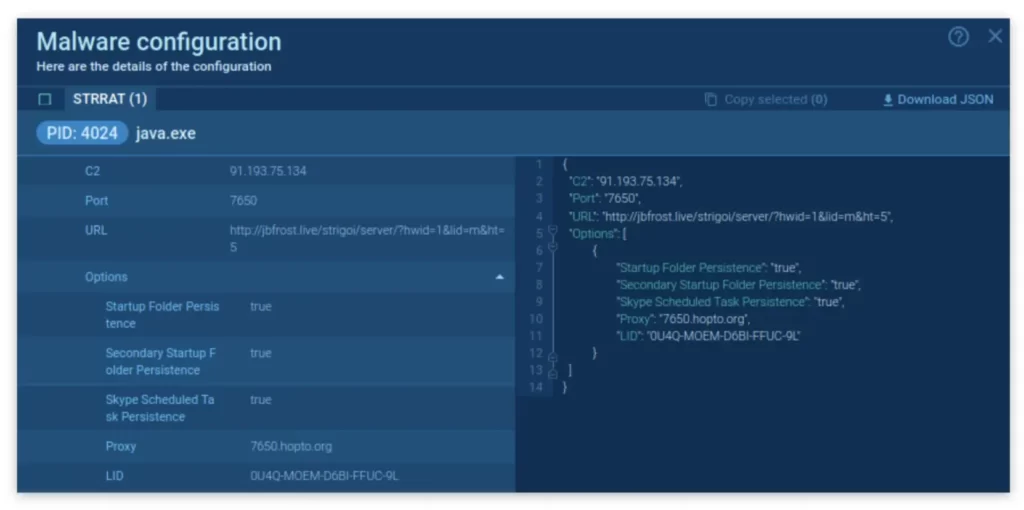
Using ANY.RUN malware sandbox, we can easily review the malware config: the service automatically unpacks the sample from memory dumps and extracts the control server data:
Here are the parameters we managed to find:
|
Required |
Options |
|
C2 address |
2 places where malware needs to install itself (Registry and StartconfigurationSkype task |
|
port |
Proxy |
|
URL link |
LID (license) |
And here’s how it looks in the service:
ANY.RUN sure makes the process of malware analysis look easy. Most of ANY.RUN’s features are actually free to use, but some more advanced ones are exclusive to the premium version. We’re excited to offer you a chance to try the ultimate ANY.RUN experience for free:
Wrapping up
In this article, we combed through the malicious code of this JAVA-based malware, exploring its features with ANY.RUN’s malware sandbox. We extracted valuable data and managed to figure out what the code actually does in two ways — manually and within the online sandbox.
We hope that if you made it this far, you’re now armed with a much better understanding of the SRRAT threat and well-equipped with IOCs to configure detection rules. As always, stay safe online!