As of 13 March, GitHub recommends that all users implement Two-factor authentication (2FA).
A two-factor authentication step would be helpful to protect the accounts of GitHub’s 100 million users.
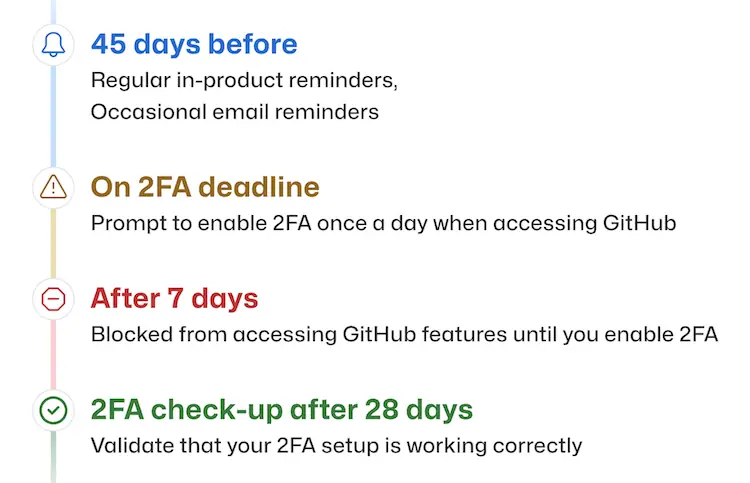
If your account is selected for enrollment, you will be notified via email and see a banner on GitHub website, asking you to enroll. You’ll have 45 days to configure 2FA on your account. Before that date nothing will change about using GitHub except for the reminders. The website will let you know when your enablement deadline is getting close, and once it has passed you will be required to enable 2FA the first time you access the GitHub website.
If you already set up 2FA with a security key, GitHub will use that as the primary two-factor authentication channel. Security keys provide the strongest protection for your account credentials.
GitHub continues to invest in account security to help secure the broader supply chain. We want enrolling your GitHub account in 2FA to be as easy as possible, using methods that are reliable and secure so you always have access to your account, the company added.
GitHub recommends Two-factor authentication (2FA), and gives the direction to use it.
- If you enable 2FA, after you successfully enter your username and password, we’ll also prompt you to provide a code that’s generated by a time-based one time password (TOTP) application on your mobile device or sent as a text message (SMS).
- After you configure 2FA, your account enters a check up period for 28 days. You can leave the check up period by successfully performing 2FA within those 28 days. If you don’t perform 2FA in that timespan, you’ll then be asked to perform 2FA inside one of your existing GitHub.com sessions.
- If you cannot perform 2FA to pass the 28th day checkup, you will be provided a shortcut that lets you reconfigure your 2FA settings. You must reconfigure your settings before you can access the rest of GitHub. For more information, see “Accessing GitHub using two-factor authentication” and “Configuring two-factor authentication.”
- In addition to authentication with a TOTP application or a text message, you can optionally add an alternative method of authentication with GitHub Mobile or a security key using WebAuthn. For more information, see “Configuring two-factor authentication” and “Configuring two-factor authentication.”
What is Two-factor authentication (2FA)?
Two-factor authentication (2FA) is an extra layer of security used when logging into websites or apps. With 2FA, you have to log in with your username and password and provide another form of authentication that only you know or have access to.
For GitHub, the second form of authentication is a code that’s generated by an application on your mobile device or sent as a text message (SMS). After you enable 2FA, GitHub generates an authentication code any time someone attempts to sign into your account on GitHub.com. The only way someone can sign into your account is if they know both your password and have access to the authentication code on your phone.
The company said, we strongly recommend using a time-based one-time password (TOTP) application to configure 2FA. TOTP applications are more reliable than SMS, especially for locations outside the United States. Many TOTP apps support the secure backup of your authentication codes in the cloud and can be restored if you lose access to your device.
After you configure 2FA, your account will enter a 28-day check up period. You can leave the check up period by successfully performing 2FA in those 28 days.
If you delete your authenticator application after configuring two-factor authentication, you’ll need to provide your recovery code to get access to your account. Many TOTP apps support the secure backup of your authentication codes in the cloud and can be restored if you lose access to your device.
Using a security key
If you’ve set up a security key on your account, and your browser supports security keys, you can use it to complete your sign in.
- Using your username and password, sign in to GitHub through your browser.
- If you use a physical security key, ensure it’s connected to your device.
- To trigger the security key prompt from your operating system, select “Use security key”.
- Select the appropriate option in the prompt. Depending on your security key configuration, you may type a PIN, complete a biometric prompt, or use a physical security key.
How To Recover your account if you lose your 2FA credentials
- Using a two-factor authentication recovery code
- Authenticating with a security key
- Authenticating with a fallback number
- Authenticating with a verified device, SSH token, or personal access token
- If you lose access to your two-factor authentication credentials, you can use your recovery codes, or another recovery option, to regain access to your account.
Using a two-factor authentication recovery code
Use one of your recovery codes to automatically regain entry into your account. You may have saved your recovery codes to a password manager or your computer’s downloads folder. The default filename for recovery codes is github-recovery-codes.txt.
1. Type your username and password to prompt authentication.
2. Under “Having problems?”, click Use a recovery code or request a reset.
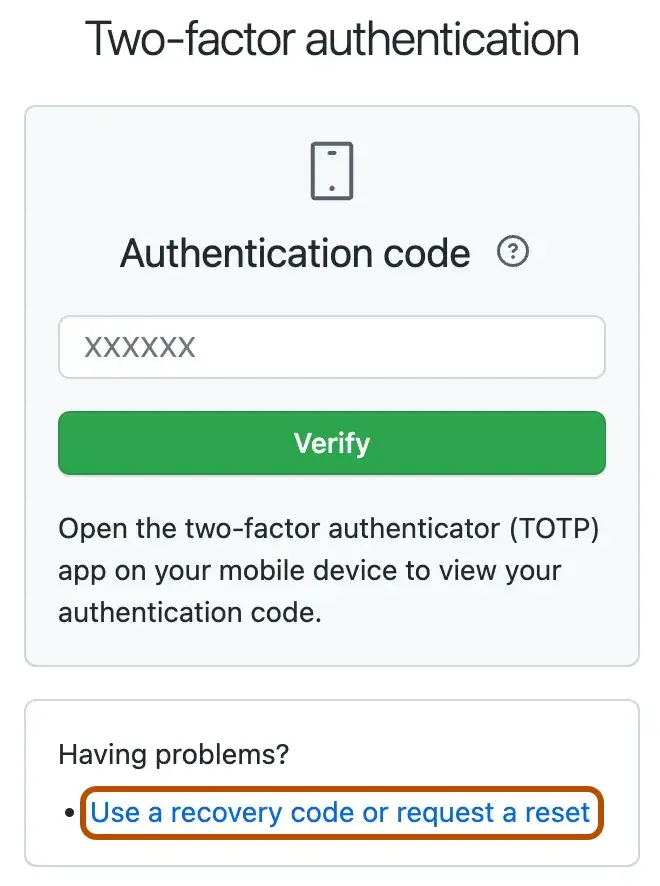
3. Type one of your recovery codes, then click Verify.











