All-In-One Anonymity, Privacy, and Security platform, SADD.IO, Causes Paradigm Shift in Cybersecurity.
Introduction
The cyberworld has definitely become one of humanity’s most used resources in this day and age. We use it to communicate, manage funding, entertain ourselves, and provide services. Though, these are just a few benefits, the cyberworld can also be very dangerous, depending upon how it is navigated.
Sure, using the latest antivirus software, virtual private networks (VPNs), anonymity networks, or even virtual machines could aid in protecting yourself. However, one’s limited knowledge in cybersecurity, and how that knowledge is applied when navigating the cyberworld, could render these tools as utterly useless.
Desmond Jackson, Chief Executive Officer of Penetration Testing and Software Development Company, Jackson CS Consulting, LLC (JCSC), realized that the tools listed above only provide a limited amount of protection in certain areas of cybersecurity. So in early 2018, he created SADD.IO: Scalable Anonymous Disposable Desktops (SADD), to provide anonymity, privacy, and security as an All-In-One platform.
This article will first, give a bit of history about the developer, define the areas of cybersecurity, explain what SADD is, show the difference that SADD makes on the areas of cybersecurity, present some use-cases, list some key benefits, and finally discuss and conclude the overall impact of SADD.
About the Developer
Desmond, is a 22-year-old, Entrepreneur, from Lowndes County, Alabama. He has been coding since the age of eight, with his very first program being a batch fork virus. By ten years old, he learned how to modify variables in flash games via memory injection. At twelve, Desmond found himself experimenting in areas of network, software, and operating system security.
Around the age of sixteen, he was highly involved with Web Penetration Testing. This landed him multiple freelance and contracting opportunities with companies like Enjin PTE LTD and Nitrogen Sports. Though in High School, Desmond was already conducting collegiate academic research under Dr. Albert Lilly and Dr. Jeffery Gray, at the University of Alabama. There, he found multiple vulnerabilities that affected the network and also invented JScanner: A Java Malware Defense Tool, that detected malicious Java bytecode.
Desmond, ultimately graduated from the University of Alabama, obtaining his Bachelors of Science in Computer Science. Throughout college, he worked at companies such as Google, as a Software Engineer, Synopsys as a Research and Development Engineer, and Cigital as a Cybersecurity Consultant. Besides operating JCSC, Desmond enjoys gaming competitively, mentoring the younger generation, and inventing new technology.
Areas of Cybersecurity
To understand how SADD causes a paradigm shift in cybersecurity, we must firstly identify and define the different areas of cybersecurity. Cybersecurity can generally be wrapped into 5 areas. These areas are: Network Security, Application Security, Information Security, Operational Security, and Disaster Recovery.
Network Security is a set of defensive measures that need to be taken to protect, detect, and react to attacks caused over the network. Application Security involves using tools and testing techniques to find vulnerabilities in organizations’ applications. Information Security concerns data protection, whether the data is stored on a machine or transferred from one machine to another.
Operational Security consists of organizations assessing public information about themselves that could lead to unauthorized access. Finally, Disaster Recovery relies on techniques to remediate widespread data loss or outages as a result of cyberattacks.
What is SADD?
The whitepaper shown on the sadd.io website, explains that SADD is simply a user generated, web-based, virtual machine, that is routed through the Tor network, and is forensically disposed of at the end of the user session. In order for a user to first generate the virtual machine they either need to contact support for a demo “access token” or purchase a 30 day “access token”.
An access token can be purchased for $2.50 via Paypal, Credit Card, or Cryptocurrency. Depending on the medium of purchase, an access token could be viewed as a concert ticket for users with no ties to any of their personal information. Once an access token has been purchased, users are able to use it to generate a virtual machine with a specified Operating System and time-limit.
The current available Operating Systems are Windows 10 and Kali Linux. SADD’s privacy policy explains that users do not need to provide any information about themselves to purchase an access token, worry about logging, or even collection of personal information on any of SADD’s servers/websites.
SADD’s privacy policy also acknowledges that the privacy policy of the third parties that it interacts with to process payments, protect its servers, and communicate with users may differ from its own privacy policy. So, if the users’ goal is to be anonymous and private, they are encouraged to use VPNs, proxies, or anonymizers to make purchases of access tokens and to utilize the service.
However, SADD’s Terms of Use asks that users do not use the service for criminal or tortious activity. The figures below shows the steps to generate a SADD desktop:

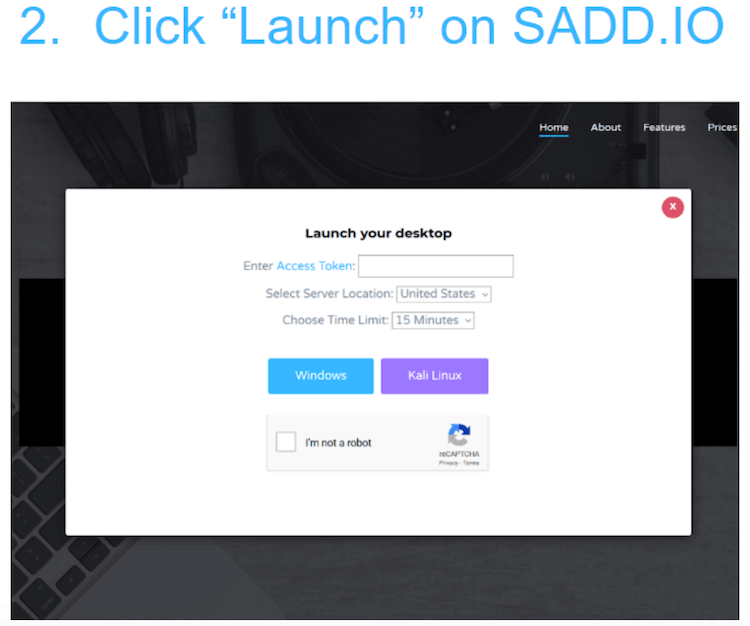
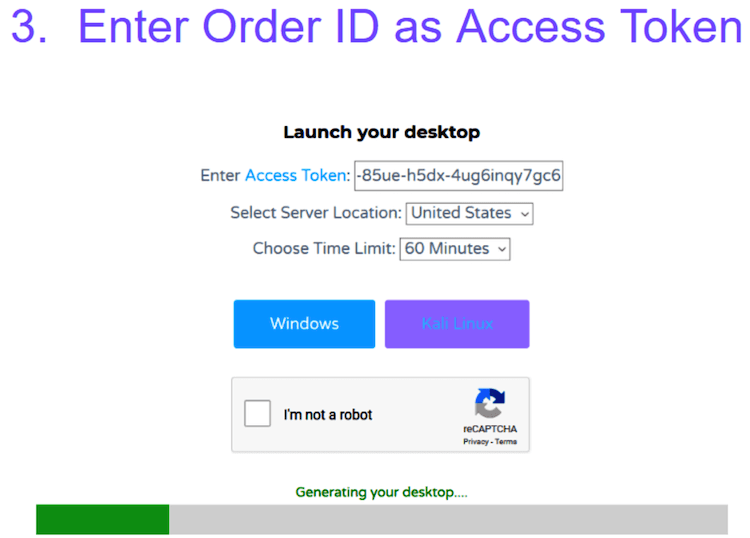
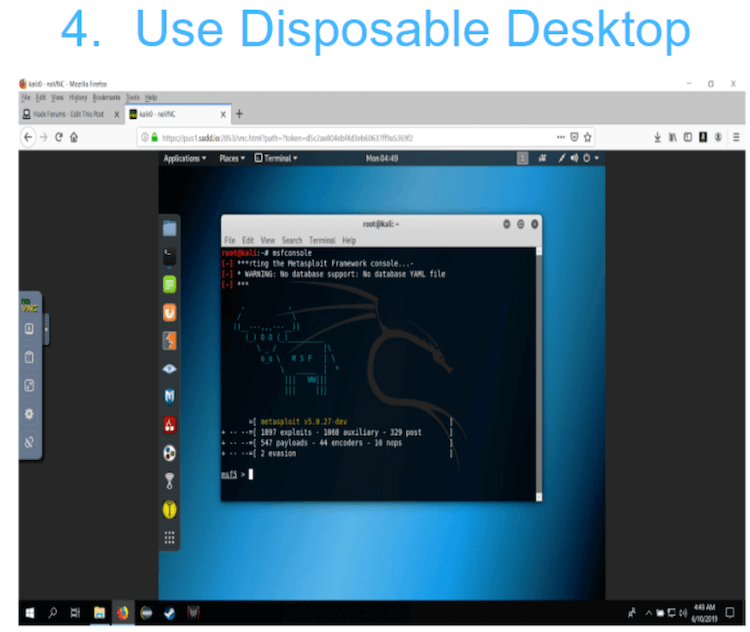
How SADD affects the Areas of Cybersecurity
SADD provides numerous amounts of benefits to the 5 different areas of cybersecurity. Starting with Network Security, we can see from the patent publication that SADD provides its users with a browser isolated virtual machine which is also routed through the Tor network. This means that the user does not have to worry about access control, anti-malware software, or firewalls alike.
The virtual machine that users control is not only physically separated from their machine but the network it operates in is also a separate network. Users cannot be attacked strictly through their virtual machine’s public IP address. The next area of cybersecurity that is affected is Application Security.
The whitepaper explains that the SADD website uses a limited amount of inputs, that are sanitized, checked, and validated. The whitepaper also touches on how SADD eliminates IP address leakage, DNS leaks, and Operating System fingerprinting. The third area of cybersecurity that SADD tackles is Information Security.
SADD protects all of its users’ information by forensically destroying all data that corresponds with the user generated desktop. Any and all data that is transmitted between the user’s machine and the SADD desktop is encrypted via TLS 1.2 or 1.3, per the whitepaper. Everything that is done is completely anonymous, private, and secure.
The fourth area of cybersecurity is Operation Security and SADD does a great job of enhancing it. Organizations and Businesses that utilize SADD no longer have to worry about their proprietary data being grouped with public data, as isolation is built-in. SADD also provides simplified regulatory compliance due to the nature of the creation and destruction of the virtual machines.
The final and fifth area of cybersecurity that SADD affects is Disaster Recovery. Since SADD utilizes virtualization technology, it can be customized for businesses to frequently “save” or backup the user’s progress if need be. This can help prevent data loss and easily address recovery issues.
Use Cases
There are many use cases for SADD technology. Some use cases apply to finances, business security, and providing a learning environment for students who are either interested in or active in the cybersecurity space:
- Foreign Target Engagement and Surveillance
Government agencies can engage foreign targets with no risk of culpability.
- Maintaining Business Security and Integrity
Employees can use the disposable desktops without risking the security and data integrity of the company.
- Anonymous Cryptocurrency Transaction Platform
SADD could be customized to become a platform where individuals could make anonymous transactions. There would be no fingerprints or traces of the transaction left on the desktop after the transaction is completed.
- Jump-Box
SADD could be customized to act as a “jump-box” for specific systems. Giving authorized users the ability to access certain systems in a company privately and securely.
- Learning Environment
SADD could be customized to provide different cyber environments to schools for students with an interest in cybersecurity.
Key Benefits
- Cyber threat mitigation with cloud-based isolation technology.
- Regulatory and litigation risk reduction for eDiscovery, privacy non-compliance, and liability.
- Employee productivity with expanded freedom for business and personal web use.
- Simplify IT governance and control of employee web access.
- IT efficiency and effectiveness by eliminating web policy exceptions with a solution that is simple to deploy, easy to use, and support.
Discussion
The discussion below is taken directly from the whitepaper. It makes some very good points about the SADD platform.
When a user decides to use the SADD platform, it is highly important for the user to identify their goals. Does the user want to maintain anonymity?
Does the user want security? Or does the user only care about privacy? Security and privacy are automatically provided by SADD, but anonymity can be easily ruined by the user through very simple mistakes. These mistakes include but are not limited to:
- Logging into personally identifiable websites.
- Conducting activities that users do on a normal basis, such as visiting a particular page on a blog everyday at a specific time.
- Using the same keywords that the user normally uses when searching the Internet.
- Performing some reaction as a result of a personal life event.
Many Internet users who want to remain anonymous will occasionally compare SADD to VPNs. SADD is in fact different from a VPN because it does not only anonymize the user, but also protects their system via isolation, and maintains privacy by shredding the virtual machines altogether.
VPNs on the other hand, only provide anonymity at the network level. That anonymity is only maintained if the VPN provider does not keep any logs or Personally Identifiable Information (PII) of its users.
As with all online services, there has to be a level of trust. If the user does not have complete and full access or control over what is being used, there needs to be trust. Many VPNs state that the VPN does not keep logs but when the VPN is subpoenaed tons of user information as well as logs are surrendered.
It is always a good idea for users to look at the privacy policy of every service of choice. In terms of safety, SADD has a bigger impact than VPNs. If every business in the world had an inhouse SADD backend server to generate desktops, it would be extremely difficult to identify users for a couple of reasons:
All generated desktops are routed through Tor, therefore, the internet would view the connection as a Tor user.
Now that the SADD server is decentralized, it would be difficult to attack the server.
VPNs are definitely more identifiable at the network level. This is because when a user connects to a VPN the user is simply using the Internet Service Provider (ISP) and sometimes Domain Name Service (DNS) settings of that VPN (if configured correctly) to connect to the internet.
Any misconfigurations of the VPN could actually hurt the user’s anonymity. However, VPNs do have the upper hand in terms of speed and latency. SADD already has a lot of latency because of the Tor network and the user’s distance from the backend server. Not to mention that SADD also uses Cloudflare’s Content Delivery Network to deliver content to its users, adding more latency.
Over the previous two years, some users have shown concern on multiple different blogs and forums about the nefarious activities that SADD could be used for. One blog in particular, DarkWebList, states that “Common Law-Abiding people” are not so concerned about destroying their browser history.
This is not an entirely true statement as a survey conducted by the Pew Research Center ultimately determined that Americans alone think that their everyday privacy is very important to them. The simple response given in the review article of SADD, posted by the decentralized international hacktivist group, Anonymous, says that “It is assumed [that] with every good creation, comes bad actors.” It would be tough to regulate nefarious actions because:
- What would alert the SADD server maintainers that nefarious activities are taking place, if all network traffic is routed through Tor?
- How could the SADD server maintainers observe that malicious activities are occurring without violating the privacy of the users?
In another conversation, SADD could be very beneficial to not only individuals and businesses, but Governmental entities as a whole. SADD’s modular backend design allows entities to enhance anonymity even more than what SADD already provides.
Entities could do this by purchasing a SADD backend server through the To Be Determined (TBD) plan on the website. The TBD plan gives the purchasing entity physical access to the server. With physical access, the proper physical protocols, and network configurations, entities could easily make the purchased server only accessible through the Local Area Network (LAN) connections.
If the entity does not disclose to some outside source that a SADD server has been purchased or leaks the LAN IP address of the server, it is not likely that the server would be in mind for a malicious actor to attack.
Conclusion
In conclusion, SADD does an excellent job of maintaining the anonymity, privacy, and security of all of its users. As with any online service, there is always room for improvement. SADD is a very generalized service that has many possible applications as shown in the Use Cases. It is important to always remember that no matter how private and secure this platform is, anonymity is only as good as the knowledge of the user as explained in the discussion section.
While the SADD platform can be used like a VPN in allowing users to check emails, stream videos, and play video games, the latency given by the Tor network would not only slow these functions down, but it would also defeat the purpose of the service.
SADD was designed to provide anonymity, privacy, and security as a service for users who want to either protect their businesses, maintain anonymity, protect their privacy, provide themselves with more security, or educate others.
Frequently Asked Questions (FAQ)
I saw this product in 2018, what has changed?
- Users can no longer generate a “free desktop” with the click of a button. Free desktop generation used to be only 15 minute sessions and HTTP only. Now all desktop generations are considered “premium”. That is 15 to 60 minute sessions and all traffic is HTTPS.
- To generate a “free desktop” you must contact support via email at [email protected] or live chat to obtain a One-Time-Use (OTU) “access token”, and state for what purpose you plan to use SADD for. Once the OTU has been used it is wiped from existence.
- All desktop generations require an “access token” to execute.
- Prices to generate a desktop are now $2.50/mo.
- Desktop options are now Windows 10 and Kali Linux.
- The User Interface has been beautified and made more readable.
- All mouse bugs have been eliminated and overall efficiency of the service has been improved.
How is SADD different from a VPN?
- Although VPNs mask your public IP address and create an encrypted tunnel from A to B in order to stop prying eyes, they do not protect your machine from the likes of viruses, vulnerabilities, and are not untraceable. Also your privacy when it comes to VPNs depends upon its privacy policy.
- SADD will not only make you anonymous on the internet, but it also isolates your machine from the virtual machine you control at the physical and network level, providing security. The virtual machine is forensically disposed of at the end of the user session to maintain privacy.
What if I use a VPN in conjunction with SADD?
- You will increase your overall anonymity, privacy, and security. However, you will add more latency to your connection to SADD of course. SADD actually recommends this in its privacy policy.
Does SADD log or record what users do?
- SADD does not log or record what users do. It actually forensically destroys all generated virtual machines and data. Please see the privacy policy.
How do we know that SADD and/or the VPN I use is being honest?
- Any internet service that you use and do not fully control requires a certain level of trust. This includes SADD, VPNs, and proxies alike. VPNs advertise privacy but sometimes their privacy policy begs to differ. Take a look at this article to see if your VPN is being honest with you. SADD’s patent publication, however, explains that the forensic disposal of user data and actions is a part of its tear down process.
Is there some sort of Whitepaper on SADD that discusses its intricacies?
- Yes, please read the whitepaper here. For even more detail, please read the patent publication.
How much does SADD cost a month?
- $2.50 a month for one “access token”.
Why are “access tokens” required now?
- Back in 2018, SADD support received many email complaints from users saying that they were not being able to generate desktops. It is believed that some users were generating multiple “free desktops” taking up slots for other users. SADD support decided to put an end to that.
Is there some sort of demo token?
- Yes, please email [email protected] or contact live chat to request a One-Time-Use (OTU) “access token”.
Is this a recurring subscription?
- No, once “access token” expires, then you must manually purchase another “access token”.
How long does an “access token” last?
- 30 days and another must be purchased after this time has passed.
Are “access token(s)” concurrent?
- No, if you give your “access token” to someone else, you must use them one at a time. If not, the oldest session that was generated will be destroyed and replaced with the newer session.
How does the “access token” help Anonymize the user? Where is the “access token” stored? How does it work?
- The “access token” is simply the order ID of your purchase through our third party, Selly. Essentially you are purchasing an order ID. SADD does NOT require you to use real personal information to purchase an “access token”. It actually encourages the use of VPNs, proxies, and or cryptocurrency. The “access token” should be viewed as a concert ticket, as its order ID does not directly correlate with who generated the virtual machine because that information is not kept record of.
I want to purchase my own dedicated server for my Employees. How would I go about doing that?
- Send an email to [email protected] and request a quote for the To Be Determined (TBD) plan.
- One small server will allow up to 25 concurrent users, API access, and year round support.
Couldn’t SADD be used for nefarious activities?
- Of course SADD could be used to conduct nefarious activities. However, SADD does not condone any illegal activities per the Terms of Use. Violation of the Terms of Use will immediately disable Token based Access.
I have files and data on my generated desktop. How can I retrieve this data before the virtual machine is forensically destroyed?
- If the files are less than 1 MB, Jackson CS Consulting LLC, website has a client-side Javascript file encryption tool located here on https://jcsc-llc.com/aes.html. You can encrypt files and then upload them to a cloud space of your choice.
- If the files are bigger than 1 MB use some tool to encrypt the files and then upload them to a cloud space of your choice.
Who owns SADD and its Intellectual Property?
- Desmond Jackson wrote all the back-end code associated with the service and the patent is assigned to him.
I am looking to acquire SADD’s Intellectual Property or invest in the platform. Who should I contact?
- Please contact Desmond Jackson at [email protected]
Watch Video
References
-
“Scalable Anonymous Disposable Desktops.” SADD, Jackson CS Consulting, LLC, 25 Mar. 2018, https://sadd.io/.
-
Hawk. “Better Than A VPN? Introducing a New Technology to Become Anonymous.” Anonymous News, Anonymous, 16 July 2018, http://anonymous-news.com/better-than-a-vpn-introducing-a-new-technology-to-become-anonymous/.
-
Jackson, Desmond Armani. SCALABLE ANONYMOUS DISPOSABLE DESKTOPS (SADD) . 17 Oct. 2019, https://pdfaiw.uspto.gov/.
-
Johnson, Aaron, et al. “Users Get Routed:Traffic Correlation on Tor by Realistic Adversaries.” Users Get Routed, ACM, 8 Nov. 2013, www.ohmygodel.com/publications/usersrouted-ccs13.pdf.
-
“What You Must Know About OS Fingerprinting.” Infosec Resources, InfoSec, 11 Mar. 2015, https://resources.infosecinstitute.com/must-know-os-fingerprinting/.
-
Kaufman, Lori. Learn How to Securely Delete Files in Windows. How-To Geek, 12 July 2017, www.howtogeek.com/72130/learn-how-to-securely-delete-files-in-windows/.
-
Mardisalu, Rob. “100+ VPN Logging Policies Debunked (2019): TheBestVPN.com.” TheBestVPN.com, TheBestVPN, 15 May 2019, https://thebestvpn.com/118-vpns-logging-policy/.
-
Prince, Matthew. “Announcing 1.1.1.1: the Fastest, Privacy-First Consumer DNS Service.” The Cloudflare Blog, Cloudflare, 1 Apr. 2018, https://blog.cloudflare.com/announcing-1111/.
-
Kumar, Mohit. Warning: Critical Tor Browser Vulnerability Leaks Users’ Real IP Address-Update Now. The Hacker News, 4 Nov. 2017, https://thehackernews.com/2017/11/tor-browser-real-ip.html.
-
Patrick, and 0brand. “Security in Real World.” Whonix, Whonix, 27 Feb. 2018, https://www.whonix.org/wiki/security_in_Real_World.
-
“Does a VPN Protect against Computer Viruses?” Buffered.com, Buffered Ltd, 2018, https://buffered.com/faq/vpn-protect-computer-viruses/.
-
Brinkmann, Martin. “Sadd: Anonymous Virtual Desktops with Tor Built-in – GHacks Tech News.” GHacks Technology News, GHacks, 23 Aug. 2018, https://www.ghacks.net/2018/08/23/sadd-anonymous-virtual-desktops-with-tor-built-in/.
-
“What Is SADD.IO and How Does It Work? Latest Guide.” Dark Web List – Dark Web Search – Dark Web News, Dark Web List, 14 June 2019, https://www.darkweblist.com/2019/hacking/what-is-sadd-io-and-how-does-it-work/.
-
Madden, Mary, and Lee Rainie. “Americans’ Attitudes About Privacy, Security and Surveillance.” Pew Research Center: Internet, Science & Tech, Pew Research Center, 24 Mar. 2016, https://www.pewresearch.org/internet/2015/05/20/americans-attitudes-about-privacy-security-and-surveillance/.
-
Rouse, Margaret. “What Is Browser Isolation? Definition from WhatIs.com.” Searchsecurity, TechTarget, 22 May 2019, https://searchsecurity.techtarget.com/definition/browser-isolation/.
-
Fruhlinger, Josh. “What Is Cyber Security? Types, Careers, Salary and Certification.” CSO Online, CSO, 5 Dec. 2019, https://www.csoonline.com/article/3482001/what-is-cybersecurity-definition-frameworks-jobs-and-salaries.html.