SSH Server Vulnerable to Terrapin Flaw – Analysis
Security researchers from Ruhr University Bochum in Germany have identified a Terrapin flaw in the Secure Shell (SSH) cryptographic network protocol.
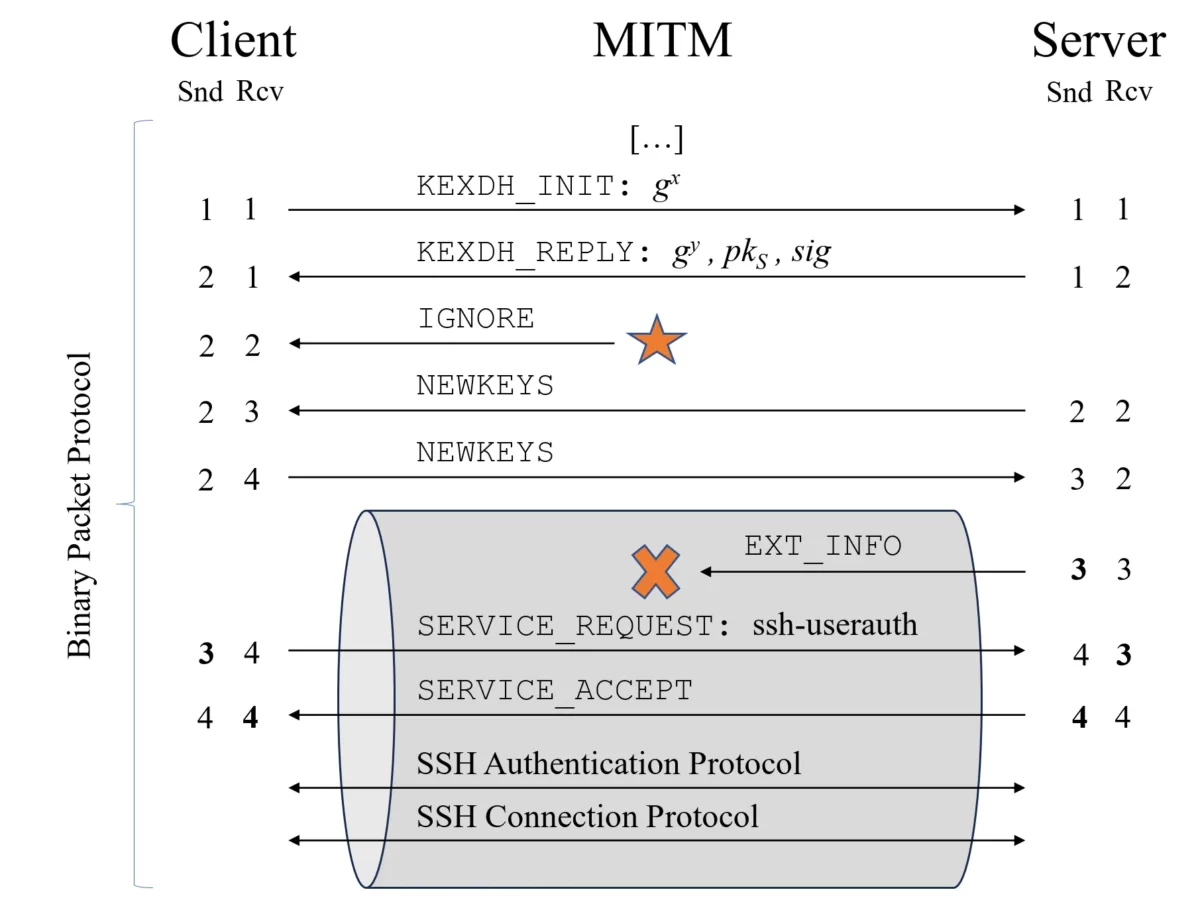
Recognized by the CVE-2023-48795 prefix truncation attack, can potentially be exploited by malicious actors to weaken the security measures in a normally considered secure channel.
What is a Terrapin Flaw attack?
- Target the SSH protocol, affecting both clients and servers.
- Manipulate sequence numbers during the handshake process to compromise the integrity of the SSH channel.
- It can downgrade public key algorithms and turn off defenses against keystroke timing attacks.
- Require attackers to be in an adversary-in-the-middle (AitM) position.
- Allowing an attacker to downgrade the connection’s security by truncating the extension negotiation message (RFC8308) from the transcript.
- The truncation can lead to using less secure client authentication algorithms and deactivating specific countermeasures against keystroke timing attacks in OpenSSH 9.5.
How To Perform Terrapin Attack?
- To perform Terrapin attack, require MitM capabilities at the network layer (the attacker must be able to intercept and modify the connection’s traffic).
- Additionally, the connection must be secured by either ChaCha20-Poly1305 or CBC with Encrypt-then-MAC. However, our scan indicates an extensive adoption of these encryption modes; therefore, Terrapin applies to most real-world SSH sessions.
Impact:
- Nearly 11 million SSH servers are vulnerable (52% of scanned servers).
- The US, China, Germany, Russia, Singapore, and Japan are the most vulnerable systems.
- Attackers have a large pool of vulnerable servers to choose from.
Additional points:
- Ruhr University Bochum team provides a Terrapin vulnerability scanner.
- CISA warns of actively exploited bugs in the Chrome and Excel parsing libraries.
CVE numbers. These are:
- CVE-2023-48795: General Protocol Flaw
- CVE-2023-46445: Rogue Extension Negotiation Attack in AsyncSSH
- CVE-2023-46446: Rogue Session Attack in AsyncSSH
Call to action:
- Check your SSH client or server for Terrapin vulnerability.
- Update to the latest version of OpenSSH.