This project was built by pentesters for pentesters.
Redeye is a open source suite to help you manage your data during a pentest operation in the most efficient and organized way.
Overview
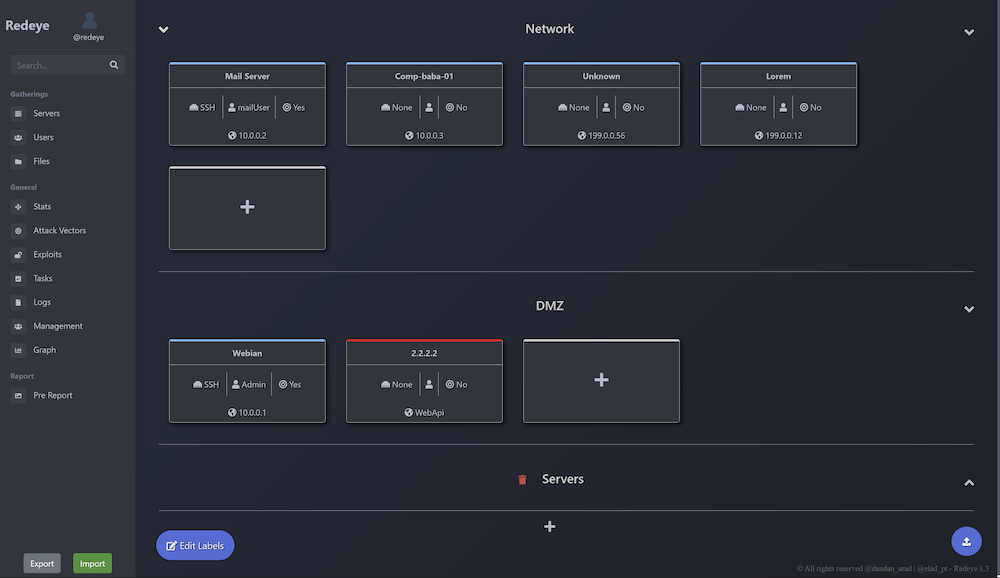
The Server panel will display all added server and basic information about the server such as: owned user, open port and if has been pwned.
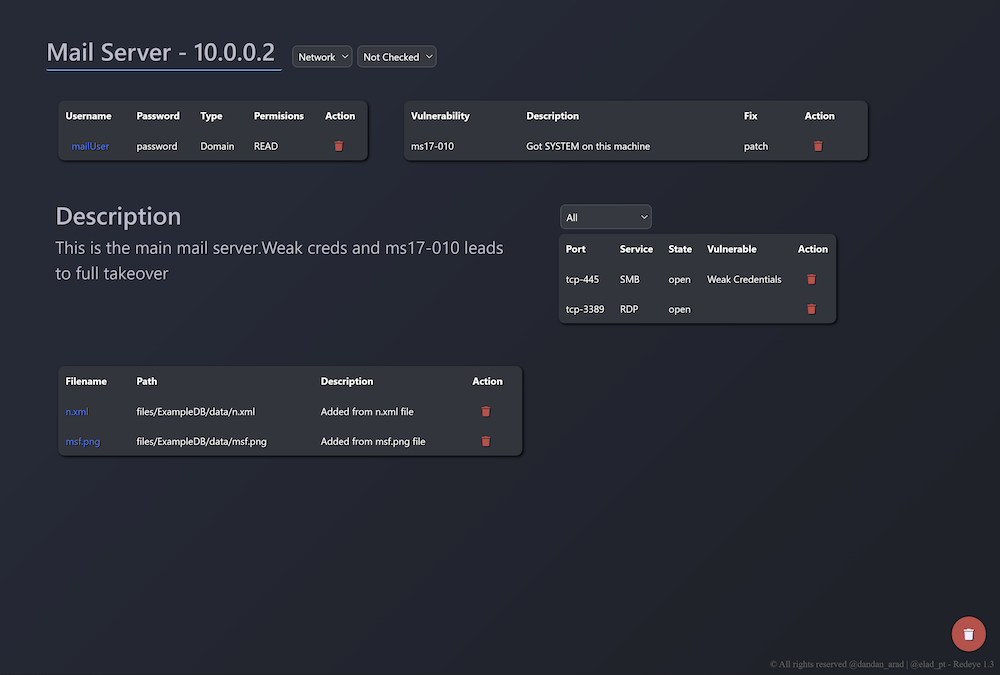
After entering the server, An edit panel will appear. We can add new users found on the server, Found vulnerabilities and add relevant attain and files.
Users panel contains all found users from all servers, The users are categorized by permission level and type. Those details can be chaned by hovering on the username.
Files panel will display all the files from the current pentest operation. A team member can upload and download those files.
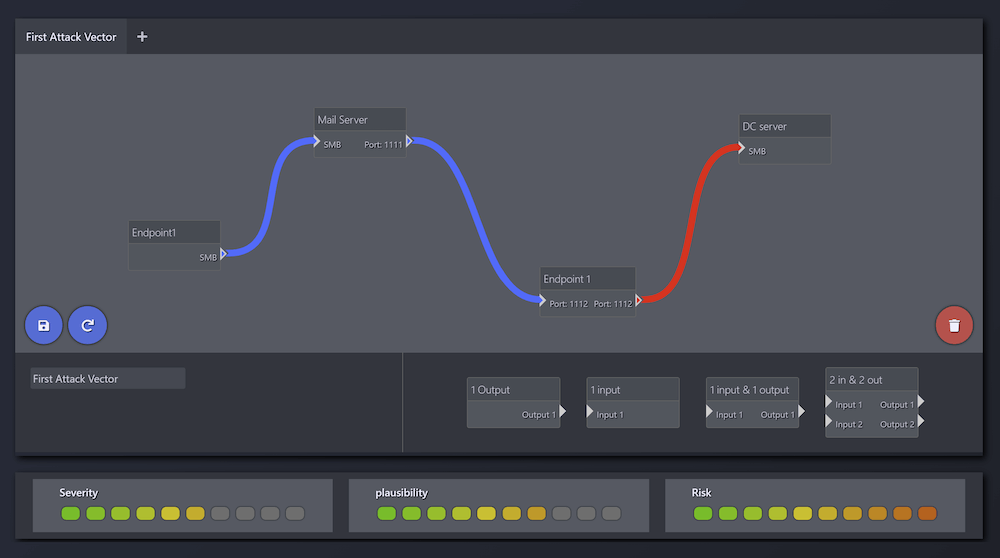
Attack vector panel will display all found attack vectors with Severity/Plausibility/Risk graphs.
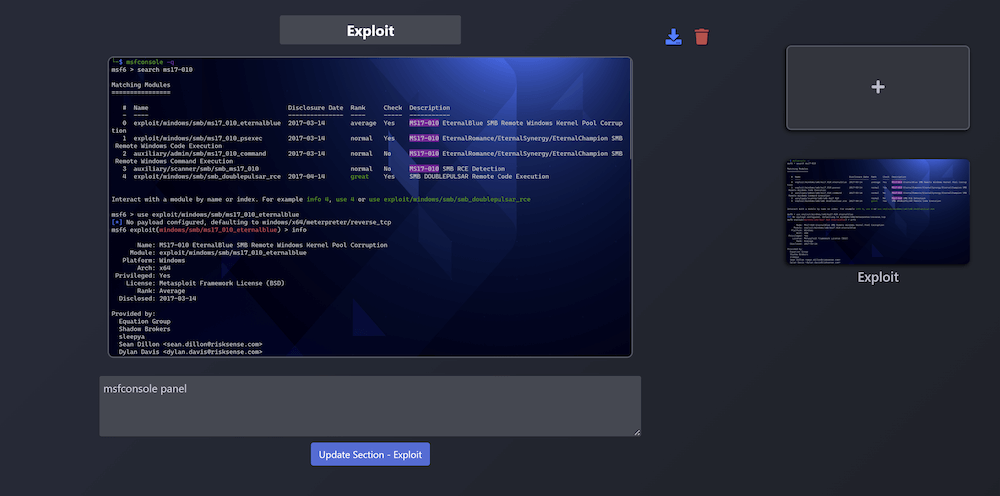
PreReport panel will contain all the screenshots from the current pentesting.
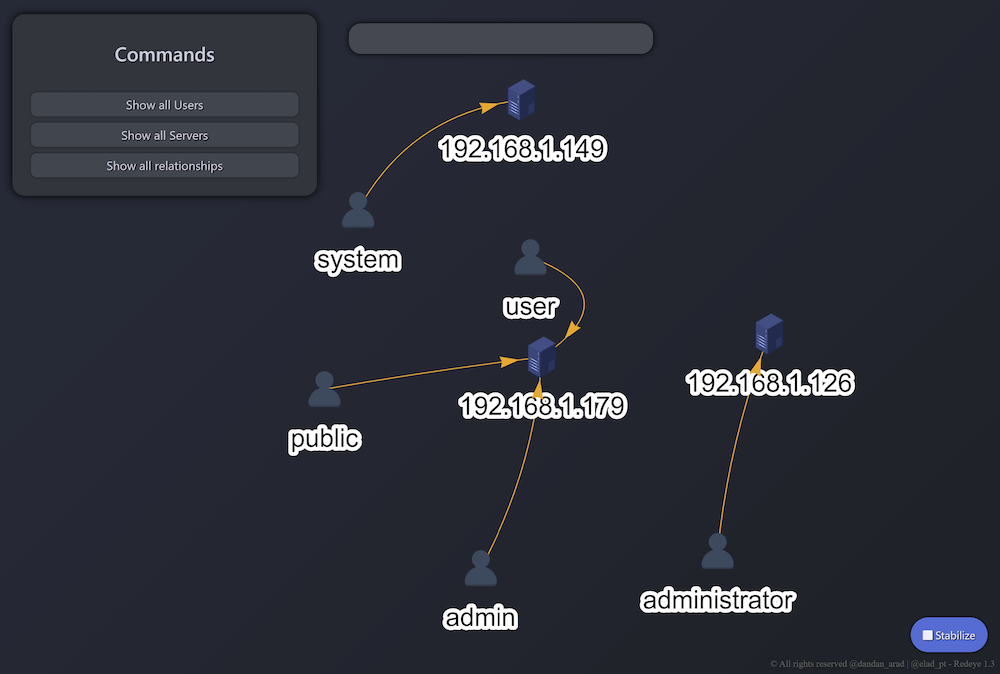
Graph panel will contain all of the Users and Servers and the relationship between them.
APIs allow users to effortlessly retrieve data by making simple API requests.
curl redeye.local:8443/api/servers –silent -H “Token: redeye_61a8fc25-105e-4e70-9bc3-58ca75e228ca” | jq
curl redeye.local:8443/api/users –silent -H “Token: redeye_61a8fc25-105e-4e70-9bc3-58ca75e228ca” | jq
curl redeye.local:8443/api/exploits –silent -H “Token: redeye_61a8fc25-105e-4e70-9bc3-58ca75e228ca” | jq
Installation
Docker
Pull from GitHub container registry.
git clone https://github.com/redeye-framework/Redeye.git cd Redeye docker-compose up -d
Start/Stop the container
sudo docker-compose start/stop
Save/Load Redeye
docker save ghcr.io/redeye-framework/redeye:latest neo4j:4.4.9 > Redeye.tar
docker load < Redeye.tar
GitHub container registry: https://github.com/redeye-framework/Redeye/pkgs/container/redeye
Source
git clone https://github.com/redeye-framework/Redeye.git cd Redeye sudo apt install python3.8-venv python3 -m venv RedeyeVirtualEnv source RedeyeVirtualEnv/bin/activate pip3 install -r requirements.txt python3 RedDB/db.py python3 redeye.py --safe
General
Redeye will listen on: http://0.0.0.0:8443
Default Credentials:
username: redeye
password: redeye
Neo4j will listen on: http://0.0.0.0:7474
Default Credentials:
username: neo4j
password: redeye