Metlo is an open source API security platform to find APP vulnerabilities.
With Metlo you can:
- Create an Inventory of all your API Endpoints and Sensitive Data.
- Detect common API vulnerabilities.
- Proactively test your APIs before they go into production.
- Detect API attacks in real time.
Once you start the scan your API traffic using one of our connectors and then analyzing trace data.
Testing
Get started for free!
There are three ways to get started with Metlo. Metlo Cloud, Metlo Self Hosted, and our Open Source product. We recommend Metlo Cloud for almost all users as it scales to 100s of millions of requests per month and all upgrades and migrations are managed for you.
You can get started with Melto Cloud right away without a credit card. Just make an account on https://app.metlo.com and follow the instructions.
Although we highly recommend Metlo Cloud, if you’re a large company or need an air-gapped system you can self host Metlo as well! Create an account on https://my.metlo.com and follow the instructions on our docs here to setup Metlo in your own Cloud environment.
If you want to deploy our Open Source product we have instructions for AWS, GCP, Azure and Docker.
You can also join our Discord community if you need help or just want to chat!
Features
- Metlo Demo
- Endpoint Discovery – Metlo scans network traffic and creates an inventory of every single endpoint in your API.
- Sensitive Data Scannning – Each endpoint is scanned for PII data and given a risk score.
- Vulnerability Discovery – Get Alerts for issues like unauthenticated endpoints returning sensitive data, No HSTS headers, PII data in URL params, Open API Spec Diffs and more
- API Security Testing – Build security tests directly in Metlo. Autogenerate tests for OWASP Top 10 vulns like BOLA, Broken Authentication, SQL Injection and more.
- CI/CD Integration – Integrate with your CI/CD to find issues in development and staging.
- Attack Detection – Our ML Algorithms build a model for baseline API behavior. Any deviation from this baseline is surfaced to your security team as soon as possible.
- Attack Context – Metlo’s UI gives you full context around any attack to help quickly fix the vulnerability.
Testing
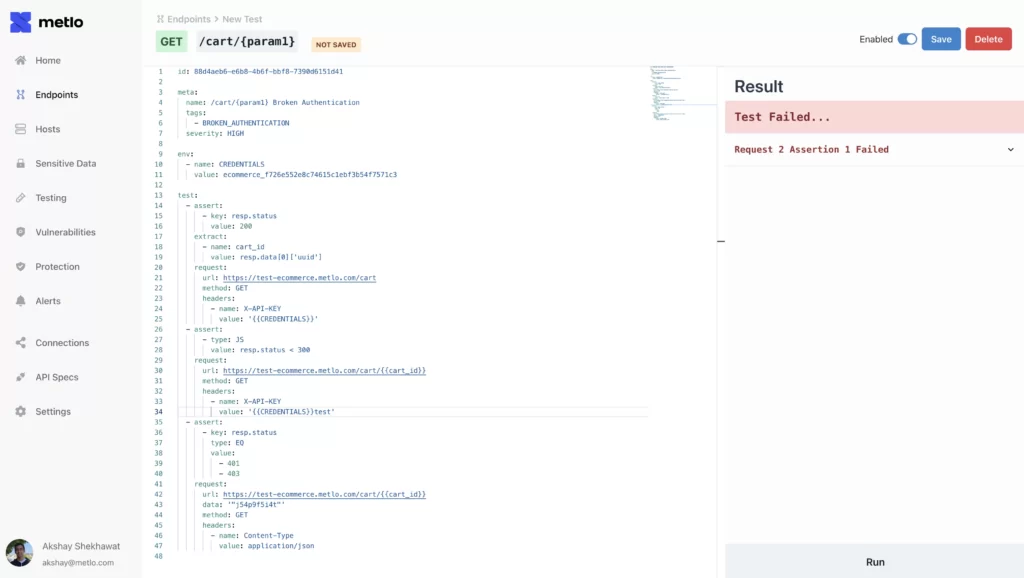
For tests that we can’t autogenerate, our built in testing framework helps you get to 100% Security Coverage on your highest risk APIs. You can build tests in a yaml format to make sure your API is working as intendend.
For example the following test checks for broken authentication:
id: test-payment-processor-metlo.com-user-billing
meta:
name: test-payment-processor.metlo.com/user/billing Test Auth
severity: CRITICAL
tags:
- BROKEN_AUTHENTICATION
test:
- request:
method: POST
url: https://test-payment-processor.metlo.com/user/billing
headers:
- name: Content-Type
value: application/json
- name: Authorization
value: ...
data: |-
{ "ccn": "...", "cc_exp": "...", "cc_code": "..." }
assert:
- key: resp.status
value: 200
- request:
method: POST
url: https://test-payment-processor.metlo.com/user/billing
headers:
- name: Content-Type
value: application/json
data: |-
{ "ccn": "...", "cc_exp": "...", "cc_code": "..." }
assert:
- key: resp.status
value: [ 401, 403 ]
You can see more information on metlo docs here.
Why Metlo?
Most businesses have adopted public facing APIs to power their websites and apps. This has dramatically increased the attack surface for your business. There’s been a 200% increase in API security breaches in just the last year with the APIs of companies like Uber, Meta, Experian and Just Dial leaking millions of records. It’s obvious that tools are needed to help security teams make APIs more secure but there’s no great solution on the market.
Some solutions require you to go through sales calls to even try the product while others have you to send all your API traffic to their own cloud. Metlo is the first Open Source API security platform that you can self host, and get started for free right away!
Download Metlo – Open Source API Security Platform