New iPhone Spyware iShutdown method detect by security researchers.
This method involves looking for specific entries in a file called “Shutdown.log.” The presence of these entries indicates a potential spyware infection.
- Suspicious entries: The security researchers identify a number of suspicious entries that can be found in the Shutdown.log file, such as entries that indicate that the device was shut down unexpectedly or that certain apps were running at the time of shutdown.
- Python scripts: The authors have created some Python scripts that can be used to automate the analysis of the Shutdown.log file.
- Effectiveness of the method: The method is effective at detecting Pegasus malware, but it requires the user to reboot their iphone frequently.
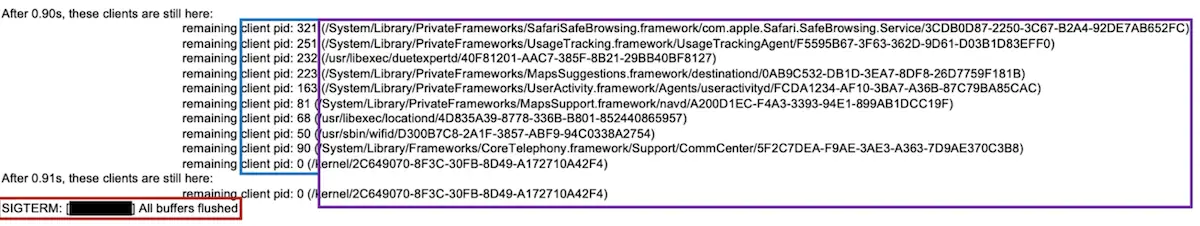
Analysis iShutdown scripts
According to Kaspersky research, to automate the analysis process, we’ve created a few Python3 scripts to help extract, analyze and parse the Shutdown.log artifact. As a prerequisite, the user needs to generate a sysdiag dump and extract the archive to the analysis machine.
iPhone’s previous flaw:
The article discusses a vulnerability in iPhones that allowed spyware like Pegasus, Reign, and Predator to be installed on a device. This could be done by tricking a user into clicking on a malicious link. Once installed, the spyware could steal a user’s data, including contacts, messages, and photos.
We’ve analyzed and confirmed the reliability of detecting a Pegasus malware infection using the Shutdown.log artifact stored in a sysdiag archive. The lightweight nature of this method makes it readily available and accessible. Moreover, this log file can store entries for several years, making it a valuable forensic artifact for analyzing and identifying anomalous log entries.
kaspersky added
How To Protecting yourself?
- Keeping their iPhones up-to-date with the latest security patches.
- Being cautious about clicking on suspicious links.
- Avoiding downloading apps from untrusted sources.
- Running a scan using a security app or taking their iPhone to a professional if they suspect spyware infection.











