The security researchers have discovered new Malware Family ‘Farseer’
The Unit 42 security researchers have discovered another malware family built for the more frequently-targeted Microsoft Windows operating system we named ‘Farseer’. As with HenBox, Farseer also has infrastructure ties to other malware, such as Poison Ivy, Zupdax, and PKPLUG.
Palo Alto Network researcher gives name Farseer. Previously the researcher discovered espionage Android malware family, HenBox, which had countless features for spying on their victims – primarily the Uyghur population – including interaction with Xiaomi IoT devices, and the Chinese consumer electronics manufacturer’s smart phones.
Also Read: To Examine Malware Analysis
Farseer employs the known technique of DLL sideloading to load its payload. The malware’s configuration files share similarities with those of HenBox, starting with the fact that both are text files that are read and parsed at run-time. For persistence, Farseer creates a registry entry to run a VBS script that executes bscmake. exe, and thus the malware itself.
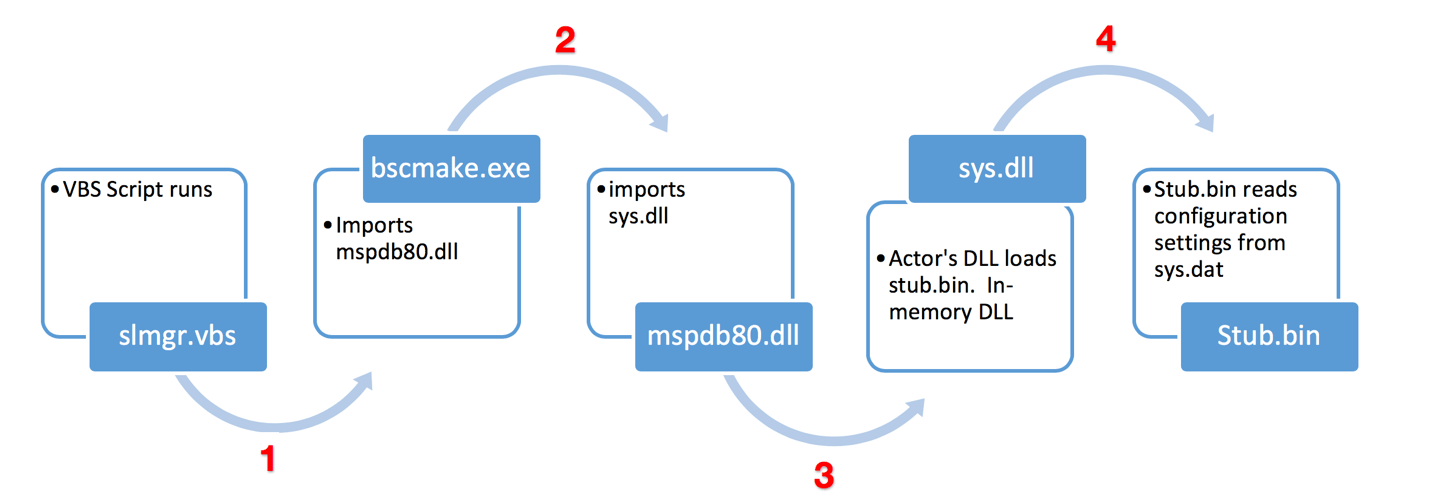
Whereas HenBox posed a threat for devices running Android, Farseer is built to target Windows, which appears to be more typical given previous threats seen from the group or groups behind this, and related malware,” the security researchers conclude.
Farseer – the use of trusted binaries to load malicious code – to load its payload, the malware begins by dropping known, legitimate, signed binaries to the host. These binaries, signed by Microsoft or other vendors, are typically trusted applications when checked by antivirus software or the operating system and thus do not raise any suspicious alerts.
Conclusion
The threat actors behind Farseer, and related malware including HenBox, continue to grow their armoury with the addition of this previously-unknown malware family. The overlapping infrastructure, shared TTPs and similarities in malicious code and configurations highlights the web of threats used to target victims in and around the South East Asia region and perhaps beyond, the security researchers added.
Farseer payloads are backdoors that beacon to pre-configured C2 servers for instructions. The malware uses various techniques to evade detection and inhibit analysis. For example, DLL sideloading using trusted, signed executables allows the malware to execute rather seamlessly; some payloads are encrypted on disk preventing analysis, especially as decompression and decryption occurs at runtime, in-memory, where code is further altered to thwart forensic analysis.











