Teler is an real-time intrusion detection and threat alert based on web log that runs in a terminal with resources that we collect and provide by the community.
Features
- Real-time: Analyze logs and identify suspicious activity in real-time.
- Alerting: teler provides alerting when a threat is detected, push notifications include Slack, Telegram and Discord.
- Monitoring: We’ve our own metrics if you want to monitor threats easily, and we use Prometheus for that.
- Latest resources: Collections is continuously up-to-date.
- Minimal configuration: You can just run it against your log file, write the log format and let teler analyze the log and show you alerts!
- Flexible log formats: teler allows any custom log format string! It all depends on how you write the log format in configuration file.
- Incremental log processing: Need data persistence rather than buffer stream? teler has the ability to process logs incrementally through the on-disk persistence options.
Why teler?
Teler was designed to be a fast, terminal-based threat analyzer. Its core idea is to quickly analyse and hunt threats in real time.
Installation
From Binary
The installation is easy. You can download a prebuilt binary from releases page, unpack and run! or run with:
▶ curl -sSfL ‘https://ktbs.dev/get-teler.sh’ | sh -s — -b /usr/local/bin
Using Docker
Pull the Docker image by running:
▶ docker pull kitabisa/teler
From Source
If you have go1.14+ compiler installed and configured:
▶ GO111MODULE=on go get -v -u ktbs.dev/teler/cmd/teler
In order to update the tool, you can use -u flag with go get command.
From GitHub
▶ git clone https://github.com/kitabisa/teler
▶ cd teler
▶ make build
▶ mv ./bin/teler /usr/local/bin
Usage
Simply, teler can be run with:
▶ [buffers] | teler -c /path/to/config/teler.yaml
# or
▶ teler -i /path/to/access.log -c /path/to/config/teler.yaml
If you’ve built teler with a Docker image:
▶ [buffers] | docker run -i –rm -e TELER_CONFIG=/path/to/config/teler.yaml teler
# or
▶ docker run -i –rm -e TELER_CONFIG=/path/to/config/teler.yaml teler –input /path/to/access.log
Flags
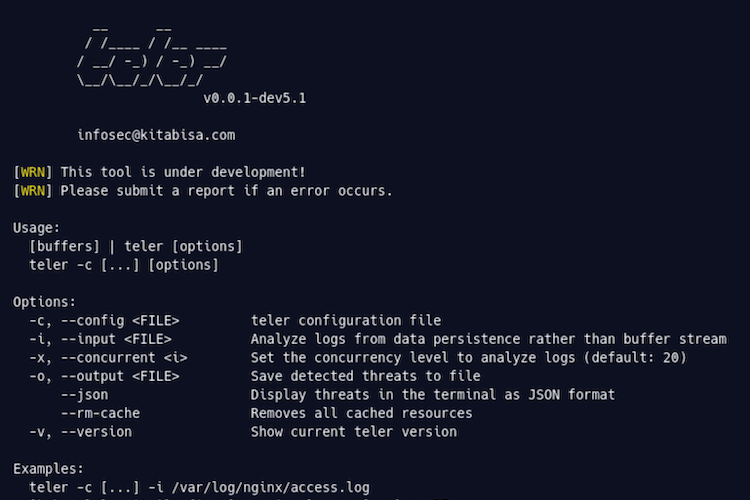
▶ teler -h
Here are all the switches it supports.
-c, –config teler configuration file
kubectl logs nginx | teler -c /path/to/config/teler.yaml
-i, –input Analyze logs from data persistence rather than buffer stream
teler -i /var/log/nginx/access.log
-x, –concurrent Set the concurrency level to analyze logs
(default: 20) tail -f /var/log/nginx/access.log | teler -x 50
-o, –output Save detected threats to file
teler -i /var/log/nginx/access.log -o /tmp/threats.log
–json Display threats in the terminal as JSON format
teler -i /var/log/nginx/access.log –json
–rm-cache Remove all cached resources
teler –rm-cache
-v, –version Show current
teler version teler -v