Malware sandbox is the fastest tool for analysis
With so many loaders, stealers, and ransomware evolving so quickly, and it’s difficult to stay on top of things. This makes their analysis more challenging and time-consuming. But cybersecurity specialists can’t waste their time. Waiting can cause severe damage. The question is, how do we avoid all of that and speed up malware analysis? Let’s find out.
Malware analysis
Performing malware analysis involves a malicious sample’s research to get the following information:
- How malware works: if you investigate the code of the program and its algorithm, you will be able to stop it from infecting the whole system.
- Characteristics of the program: improve detection by using data on malware like its family, type, version, etc.
- What is the goal of malware: trigger the sample’s execution to check out what data it is targeted at, but of course, do it in a safe environment.
- Who is behind the attack: get the IPs, origin, used TTPs, and other footprints that hackers hide.
- A plan on how to prevent this kind of attack.
Analysts can use this data to detect malware, respond to attacks effectively, and enhance security. Generally, there are several types to perform malware analysis:
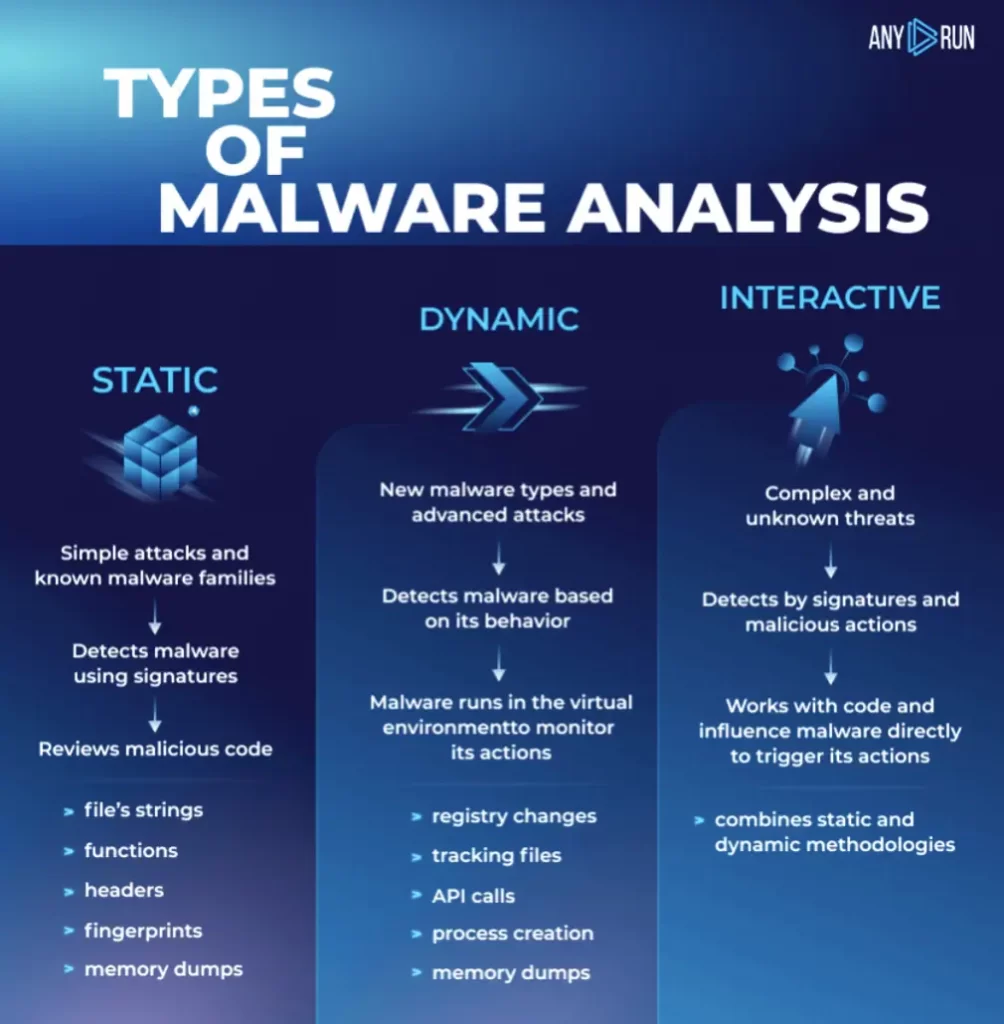
For interactive analysis it is better to use an interactive sandbox. It is a tool for executing suspicious programs from untrusted sources in a safe environment for the host machine. You can build your own sandbox or use ANY.RUN service.
Sandbox approaches
There are different approaches to the analysis in sandboxes. They can be automated or interactive.
Online automated tools allow you to upload a sample and get a report about its behaviour:
- You have to wait up to 15 minutes for the analysis cycle to finish and then receive a report.
- You can’t interact with a sample directly. Modern malicious programs can understand whether they are run on a virtual machine or a real computer. They require users to be active during execution.
- You need to deploy your own virtual environment, install operation systems, and set the required software for dynamic analysis to intercept traffic, monitor file changes, etc. We should remember that analysis doesn’t always follow the line, and things may not work out as planned for this malicious object.
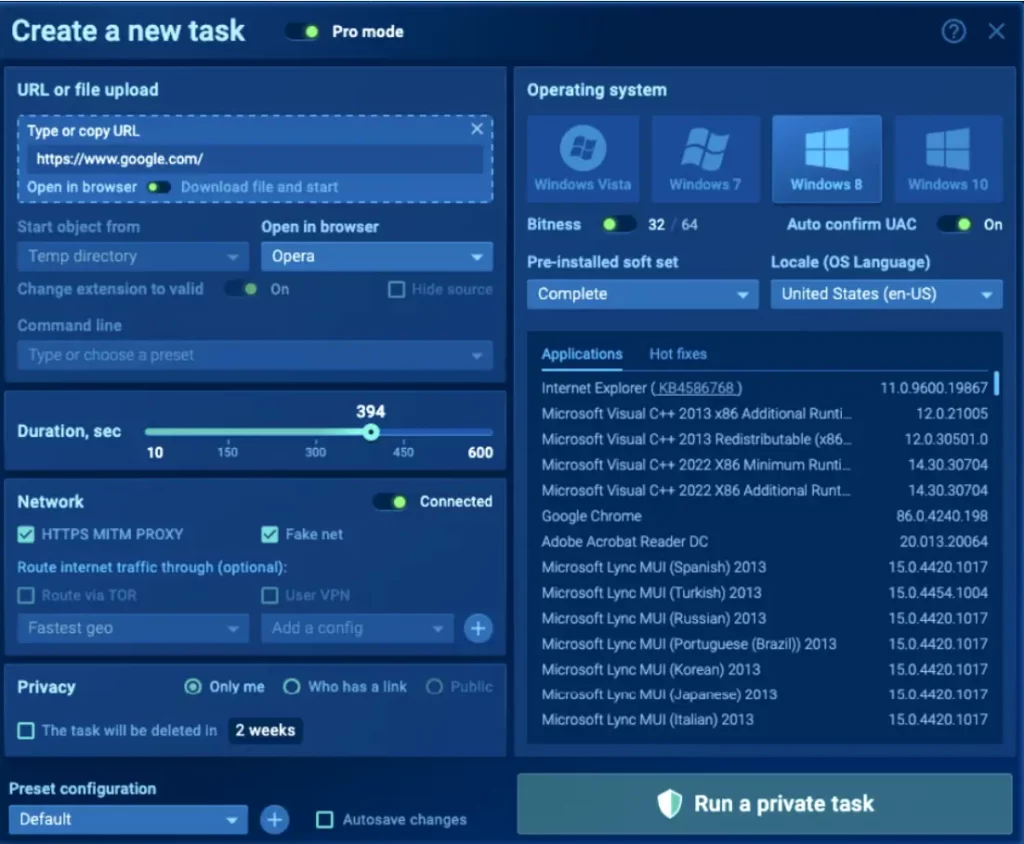
All of these cons may cause damage to security if an unusual sample remains undetected. Thankfully, now we have interactive solutions, for example – ANY.RUN sandbox. There you can detect, analyze, and monitor threats:
Instant access is one of the service’s main advantages: you receive initial results straight after a task is run. One or two minutes are usually enough to complete the research after the end of a task.
Malware is tricked into executing as if it is launched on a real machine. Users can influence the simulation in real-time and interact with the virtual environment: click a mouse, input data, reboot the system, open files, etc.
You can customize a VM with specific requirements like a browser, Microsoft Office, choose OS bitness, and locale. Choose pre-installed tools: FakeNet, MITM proxy, Tor, and VPN. Configure your own environment on the fly.
Fast malware analysis with ANY.RUN
Let’s analyze one of the submissions to see the fast analysis in action.
Looking at the process tree, we can see the EXCEL.EXE process running, and after a couple of seconds, the EQNEDT32.EXE starts execution. Exploiting the Microsoft equation editor vulnerability (CVE-2017-11882) was used, showing that the sample is malicious.
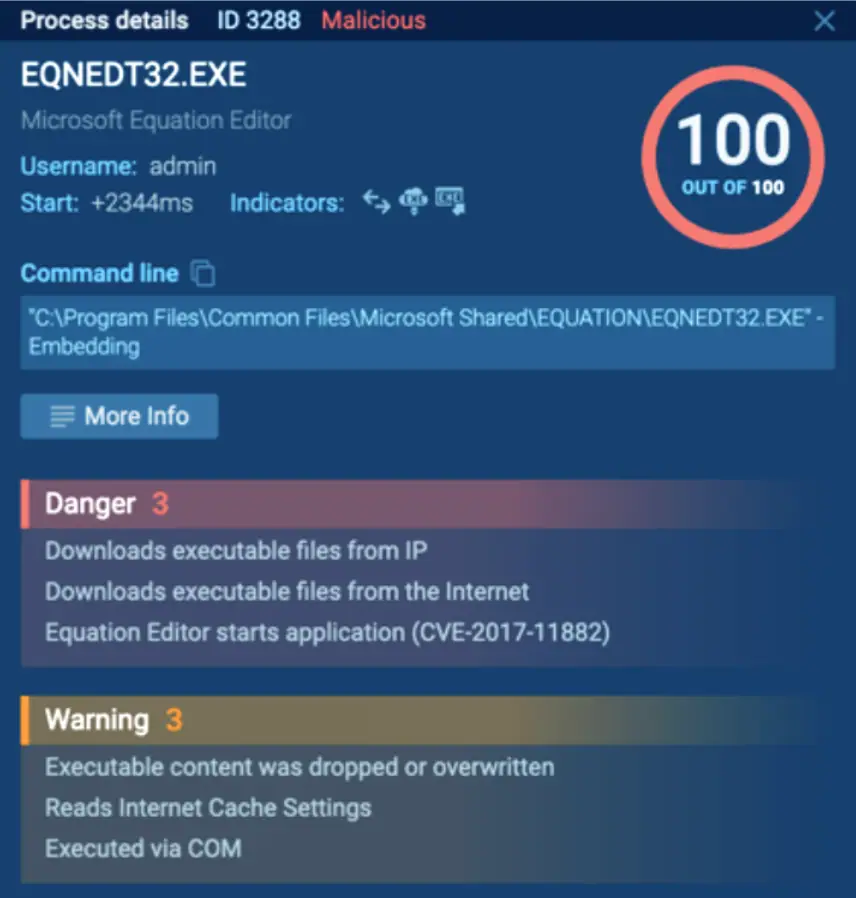
After the exploitation, the EQNEDT32.EXE process downloads and starts the executable file from the Command & Control server. We can tell that the analyzed sample is malicious 3 seconds after the task’s launch thanks to the real-time data. And the analysis can be completed within minutes.
14 seconds are more than enough to get the malware family detected by the network’s Suricata rules. Local signatures detect this sample after it creates files and writes them into the registry.
The real-time analysis starts immediately after the task is launched in ANY.RUN. Once the Excel file is opened, the infection process starts. In the virtual machine, we have an opportunity to react to it and maybe trigger the possible malware to act.
The RegAsm.exe system process is injected, then it steals personal data, drops applications, and changes the autorun value in the registry. Moreover, LokiBot is detected. We also know from “HTTP Requests” that EQNEDT32.EXE downloads the main payload from the following URL http://192.210.214.146. In the “Connections” field, we can find out that RegAsm.exe connects with microdots.in.
Our task is still running, and we’ve collected a lot of data. But if something seems a little off, the executed file or maldoc may not have worked out. You can relaunch the task with new configurations: pick a different system’s locale, run it with Tor, or choose another OS. And you may get a completely new outcome within a couple of minutes. Try it yourself:
Write the “HOC” promo code at [email protected] using your business email address and get 14 days of ANY.RUN premium subscription for free!
You can spend extra time performing a more comprehensive analysis with the help of the MITRE ATT&CK matrix, the process graph. Work on one sample jointly and save or share your task with colleagues using various types of malware reports.
Cybersecurity professionals need to evaluate threats fast and respond efficiently before damage occurs. You can try it out and see how it can save your time and speed up malware analysis.