Today, we are going to introduce you about Dimitri (Deepmagic Information Gathering Tool).
DMitry has the ability to gather as much information as possible about a host. The base functionality can collect possible subdomains, email addresses, uptime information, TCP port scan, whois lookups, and more.
Its provides the ability to perform :
- Perform an Internet Number whois lookup.
- Retrieve possible uptime data, system and server data.
- Perform a SubDomain search on a target host.
- Perform an E-Mail address search on a target host.
- Perform a TCP Portscan on the host target.
- A Modular program allowing user specified modules
So lets start..
Requirements:
- Kali Linux OS > DMitry
Go to the applications > information gathering > dmitry
Or
Open the Terminal and type dmitry and hit enter
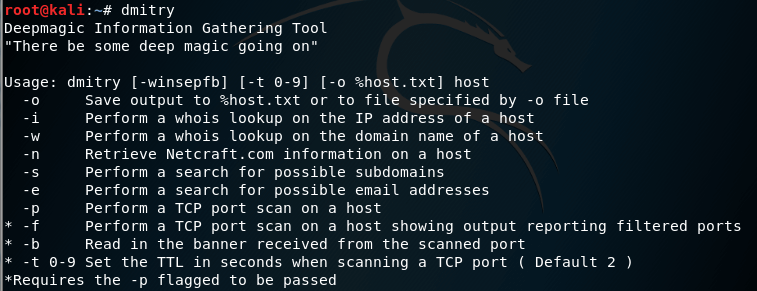
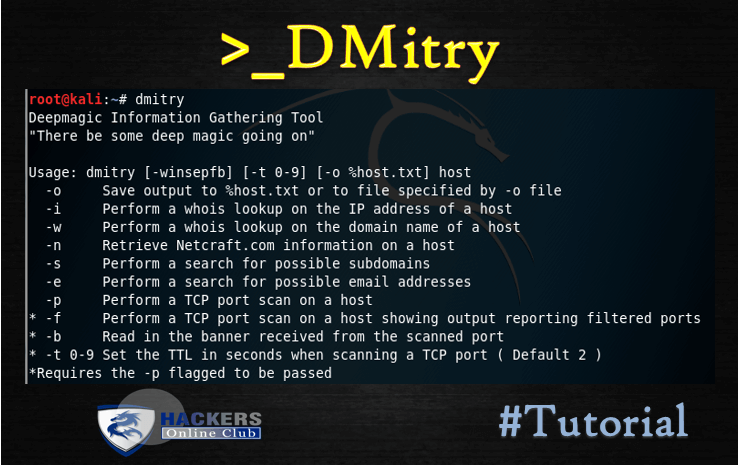
root@kali:~# dmitry -h Deepmagic Information Gathering Tool "There be some deep magic going on" dmitry: invalid option -- 'h' Usage: dmitry [-winsepfb] [-t 0-9] [-o %host.txt] host -o Save output to %host.txt or to file specified by -o file -i Perform a whois lookup on the IP address of a host -w Perform a whois lookup on the domain name of a host -n Retrieve Netcraft.com information on a host -s Perform a search for possible subdomains -e Perform a search for possible email addresses -p Perform a TCP port scan on a host * -f Perform a TCP port scan on a host showing output reporting filtered ports * -b Read in the banner received from the scanned port * -t 0-9 Set the TTL in seconds when scanning a TCP port ( Default 2 ) *Requires the -p flagged to be passed
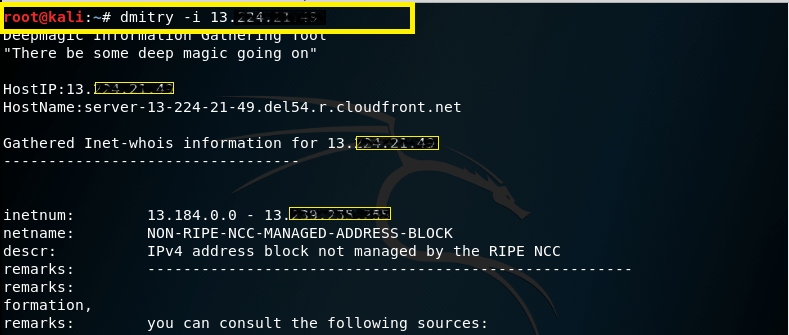
-i – This command is used to perform a whois lookup of the IP address of a host, this tells us that if we only no the name that dmitry will find the IP for us.
Syntax – dmitry –i (IP address)
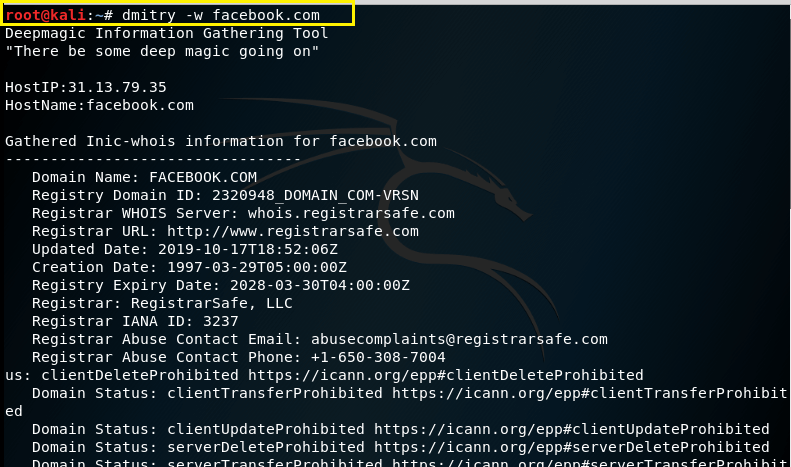
–w – This command is usin to perform a whois lookup on the domain name of a host.
Syntax – dmitry –w (domain.com)
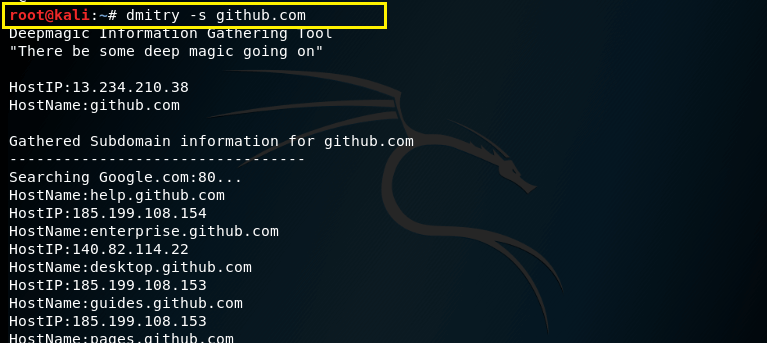
–s – This command is used to performs a search for possible sub domains.
Syntax – dmitry –s (domain.com)
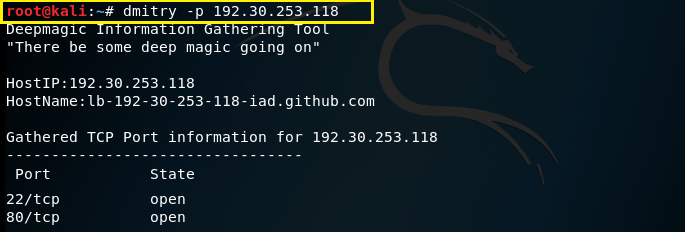
–p – This command is used to perform a TCP port scan on a host.
Syntax – dmitry –p (IP address)
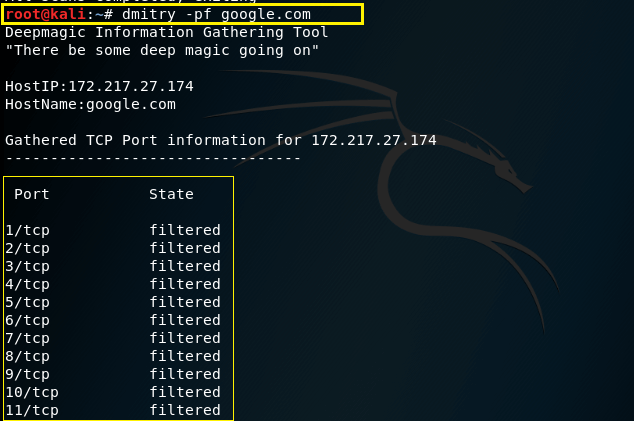
–f – This command is used to perform a TCP port scan on a host showing output reporting filtered ports (useful if there is a firewall in place). For running successfully this command -p must be set.
Syntax – dmitry –pf (domain.com)
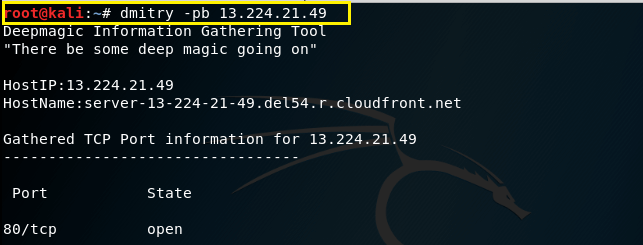
–b – This command is used to report to you a banner received from a scanned port (Note this will only work if the port sends us a banner when scanned). For running successfully this command -p must be set.
Syntax – dmitry –pb (IP address)
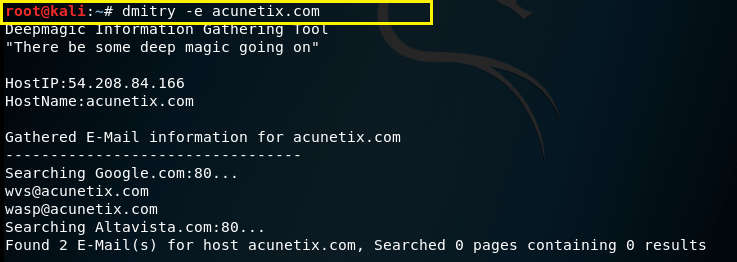
–e – This command is used to perform a search for possible email addresses.
Syntax – dmitry –e (domain)
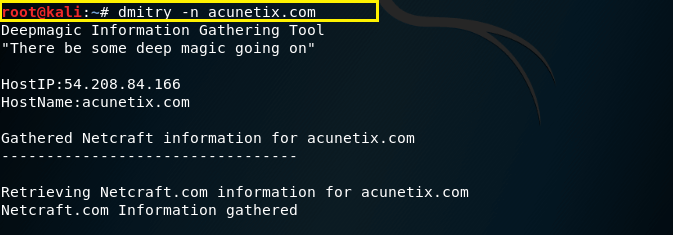
–n – This command is used to give us Netcraft.com information on a host.
Syntax – dmitry –n (domain)
–o – This command is used to save output specify with a given name our output the default is host.txt you could name it anything you want.
Syntax – dmitry –s (domain) –o (filename.txt)
Here , -s is just a command you can also use other commands and save it on a text file by using -o filename.txt
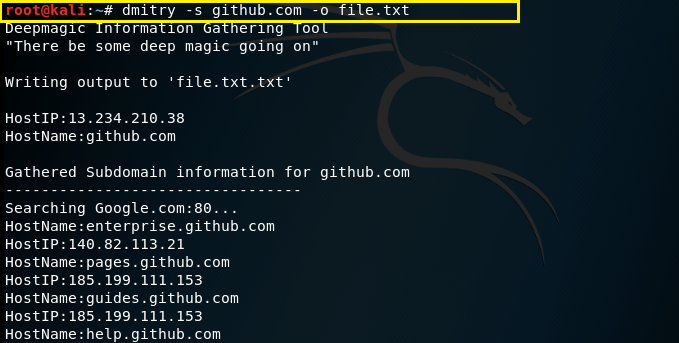
Here we are going to run some useful commands together .
Also See: Zenmap- Free Open Source Information Gathering Software
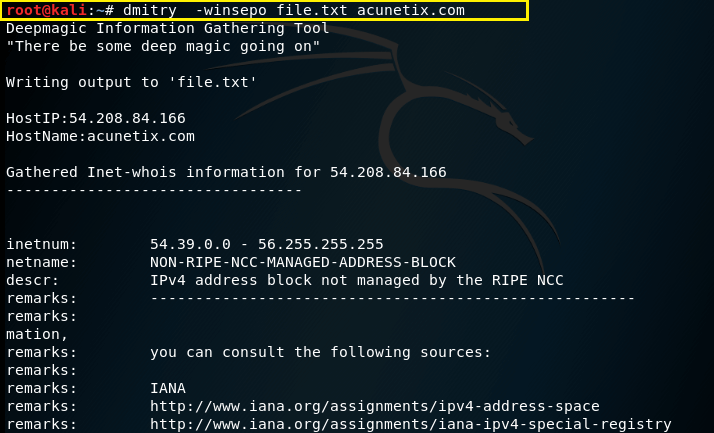
Run a domain whois lookup (w), an IP whois lookup (i), retrieve Netcraft info (n), search for subdomains (s), search for email addresses (e), do a TCP port scan (p), and save the output to filename.txt (o) for the domain domain.com:
Syntax – dmitry -winsepo filename.txt (domain.com)